
"Dogfooding" is such a strange word, and I'm using it as a substitute for "Eating your own dog food". As we do have a global audience, I worry that the term is somewhat provincial (and maybe a bit strange out of context). So here, here's the explanation of this idiom on Wikipedia.
Sonatype is "recursive". We're a group of developers, creating tools for developers, getting feedback from developers. Logically, we tend to use everything we make. We're the first customer. We deploy early development releases of Nexus Professional to our own Nexus Professional instance, we use repository.sonatype.org as a test case as the release approaches, and every feature we send out to our customers has been audited and tested internally. By the time you download our software, we've already been using it often for a few months or weeks, and we also make heavy use of Sonatype Insight to identify licensing and security risks.
Now, this blog post is a bit risky. I'm about to tell you about the security issues that the Engineering team discovered in Nexus when we ran Nexus through our Insight scanner during the Nexus 2.1 release. By doing this, I'm exposing people that haven't updated Nexus to 2.1 to some risk. At the same time, I've given everyone ample notice to upgrade (I even made a video imploring people to upgrade), and I'm a big believer in transparency. If we know something related to security, you should know it as well after we've given people enough time to upgrade.
Security Issues Discovered in Pre-2.1 Nexus Releases
Here's a quick snapshot of the relevant Nexus Pro JIRA issue that covered the security issues we found in Nexus using Insight:
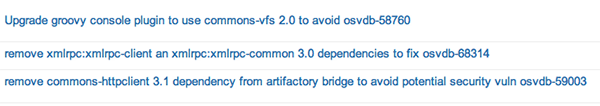
The OSVDB vulnerabilities we found were:
- OSVDB-59760 - Apache Commons VFS Exception Error Message Cleartext Credential Disclosure
- OSVDB-68314 - Apache XML-RPC SAX Parser External Entity Information Disclosure
- OSVDB-59003 - Apache HttpClient POST Request Handling Memory Consumption DoS
Unless you want to risk exposing a secure credential, get hacked via some XML, or suffer a denial of service attack via our Artifactory bridge, you probably want to upgrade to Nexus 2.1 right now. Got it? Good, Download Nexus Pro 2.1 Here or Download Nexus OSS 2.1 Here.
Going Forward: A Scan for every release?
Maybe. What I'd really like to see is for every single open source project out there to do the same. If I'm going to be depending on Spring or Hibernate, I'd like to see some proof that the developers have done some due diligence.
I think that posting an Insight scan alongside every software release is something that all software companies and open source projects should consider. We're considering it for all releases going forward. There would be no more effective way to let your customers know that your software is clear of licensing issues and free of vulnerabilities than to post an Insight Application Health Check alongside your software.
NOTE: You might be asking, why the picture of the surfing dog? My answer is simple. Why not a picture of a surfing dog? Next question.




