On January 16, 2021, Sonatype became aware of three malicious packages that were published to npm, and leveraged brandjacking and typosquatting techniques that we previously warned about.
The names of the packages are:
|
npm package |
versions |
Published to npm by |
|
an0n-chat-lib |
0.1.0 to 0.1.5 |
|
|
discord-fix |
0.0.1, 0.0.2 |
|
|
sonatype |
2.0.3 to 2.0.7 |
Sonatype's Security Research Team has also determined the actor(s) who authored these packages are the authors of the CursedGrabber Discord malware family which was discovered by Sonatype in November 2020.
"These packages contain variations of Discord token stealing code from Discord malware discovered by Sonatype on numerous occasions," said Sonatype Security Researcher Ax Sharma, who led the technical analysis against this malware campaign. [1, 2]
Detection and analysis
The malicious packages were detected by Sonatype's Security Research Team leveraging Sonatype Intelligence research service. On analyzing these packages closely, our Security Research Team confirmed that the packages pose a security risk and gathered clear evidence that the malware campaign was using a Discord bot to generate fake download counts for the packages to make them appear more popular to potential users.
Simultaneously with these research efforts we notified npm to remove these malicious components from the npm repository. As of this publishing, they are still available for download. We'll update this piece once npm and GitHub have removed the vulnerability.
All versions of these packages are malicious and being tracked under Sonatype's vulnerability identifier sonatype-2021-0045.
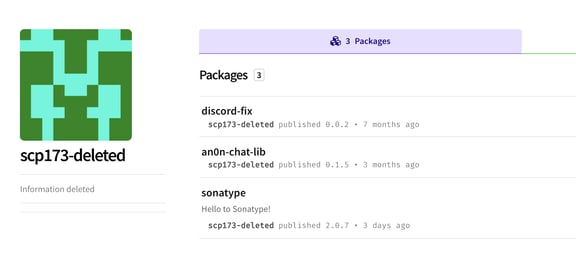
Image: Three malicious component components published by CursedGrabber malware creators
Customer impact
"Based on the visibility we have, none of the packages were downloaded by Sonatype customers and our customers remain protected from potential software supply chain attacks arising from malicious, counterfeit packages like these," stated Sharma.
These findings reiterate that software supply chain attacks will only become more common and underscore how crucial it is for organizations that protect against such attacks to continuously improve their strategies against them.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections. In fact, Sonatype - working with others in the cybersecurity research community - identified a 430% increase in upstream software supply chain attacks over the past year. With open source software component downloads surpassing 1.5 trillion in 2020, companies and their developers can no longer rely on manual reviews, analysis, and tracking to protect themselves against similar software supply chain attacks.
If you're not a Sonatype customer and want to find out if any open source software components you are using are known to be vulnerable, Sonatype's free Sonatype Vulnerability Scanner is available for you to use. The Sonatype Vulnerability Scanner will analyze any application within seconds and will produce a software bill of materials (SBOM) detailing the quality and security of each open source component used therein.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one or subscribe to automatically receive Sonatype Intelligence Insights hot off the press.






