Vulnerabilities in our Python environments are really irritating. They slow us down, are difficult to identify, and can delay the development process. What makes them more frustrating is that most of these vulnerabilities are known. Countless developers would have faced them before and they report these issues online. However, we use so many open source libraries these days, it’s almost impossible to keep up-to-date with all the dependencies and known vulnerabilities.
So wouldn’t it be nice if someone checked for known vulnerabilities in your Conda environment?
That’s why Sonatype decided to develop Jake. Jake is a tool that scans the open source packages in your current Conda environment. It then identifies all the known, publicly disclosed vulnerabilities! This check is performed against Sonatype’s OSS Index. OSS Index is a comprehensive collection of all vulnerability information for open source software. It’s derived from public sources across the web. So when you fire up Jake, it identifies the dependencies in your environment. Then it checks OSS Index to see if those dependencies have any known vulnerabilities. And the best part is that it’s free!In this post, you will learn how to set up and run Jake to check for vulnerabilities in your environment.
Who Is Jake For?
This tool is specifically for Python developers who work with Conda environments. However, maybe you should be using Conda even if you don’t know about it. In that case, Jake will make your life easier.
So, who should use Conda?
Conda is a virtual environment management system. You should ideally create separate virtual environments for each of your Python projects. This way packages installed for some other project will not create vulnerabilities in your current one. There isn’t much of a downside really to using virtual environments. Hence, it’s advisable to use separate virtual environments for your projects.
You can either use Python’s preinstalled module called venv, or use Conda. Both of them help you isolate projects and their dependencies. However, Conda environments are language agnostic. They support not only Python, but also other languages such as R. Conda is also more flexible. It allows you to install packages from repositories such as Anaconda Repository. And if you use Conda, Jake is a must-have for you to easily identify vulnerabilities in your environment.
How to Install Jake
As mentioned, Jake is a tool for Python developers to easily check for vulnerabilities in their Conda environments. Now let’s see how we can set it up to easily identify vulnerabilities in our environment.
Download Using PIP
The easiest and the fastest way to install Jake is to use PIP.
$ pip3 install jake
As shown below, it’ll start collecting the required packages found in Python Package Index (PyPI). It will then install them.
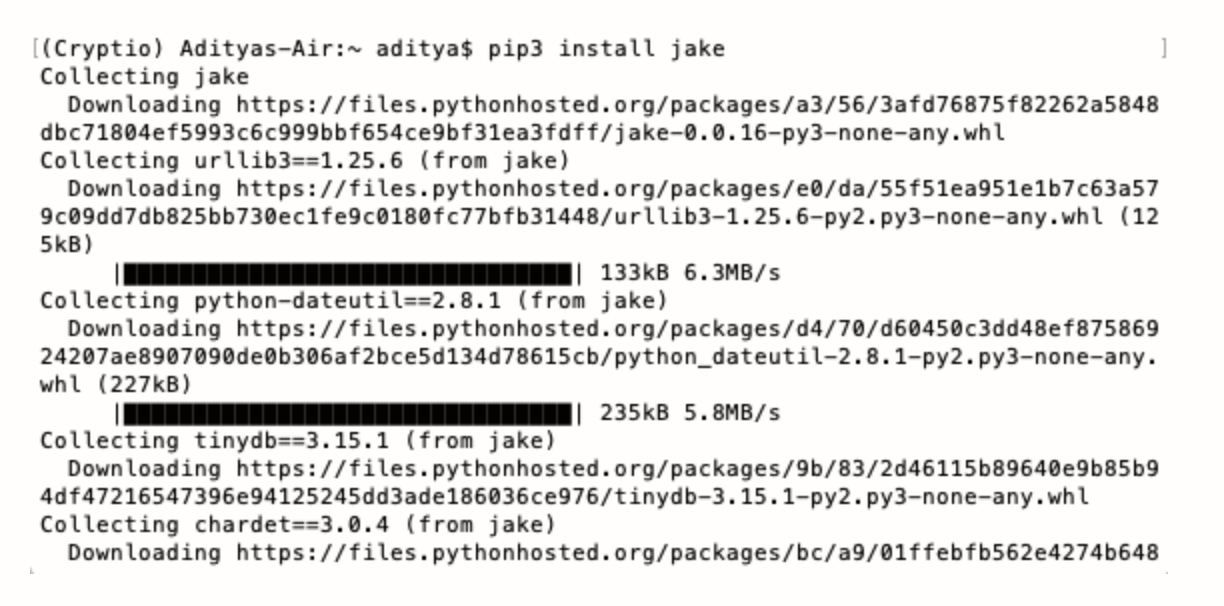
PIP is a package installer. It’s used to install and manage Python packages. Read this piece if you want to install PIP. If you use Python 2 >=2.7.9 or Python 3 >=3.4, then you already have PIP installed.
Build From Source
To build from source, you need to install Python 3.7 or higher and follow these steps:
- Clone the repo.
- Run python3 venv .venv (or whatever virtual environment you prefer).
- Then run source .venv/bin/activate.
- Then run pip install -r requirements.txt.
- Finally run pip install -e.
This will install Jake pointed at the local source you cloned.
How to Use Jake
Inside of your Conda environment, just run Jake with this command:
conda list | jake ddt
This will fire up Jake. Jake identifies the dependencies (in my case urllib) in the current Conda environment (in my case Cryptio). It will then check OSS Index to see if they are any vulnerabilities. Jake checks the packages one by one. It also notifies you if there are no known vulnerabilities for the current version.
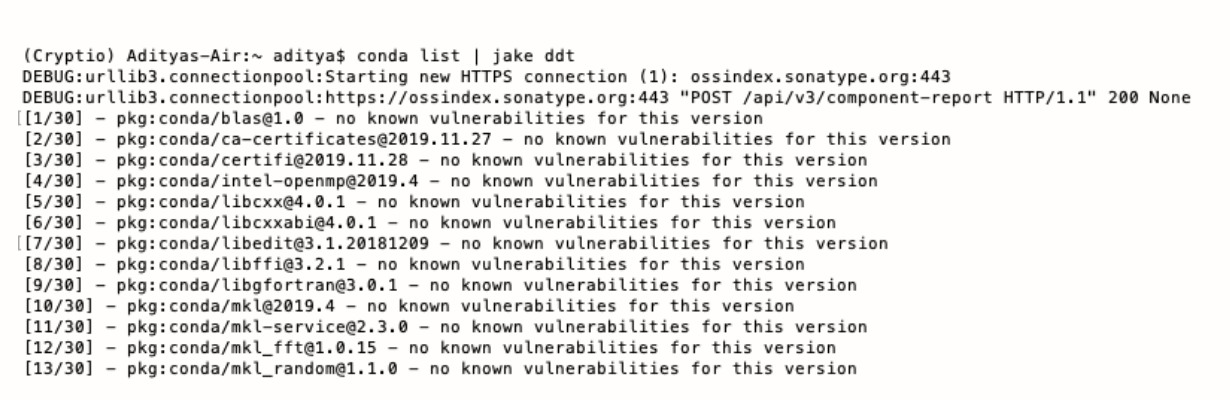
If it does identify a vulnerability, as shown below, it will report its OSS Index ID, title, CVSS score, and description.
Jake will eventually check each package and report all the known vulnerabilities from the OSS Index.
How to Read the Vulnerability Details
Jake reports some information about each identified vulnerability. Let’s dig into this information.
Title
The title tells you what type of issue it is, such as data handling. The title also contains the CVE identifier. For example, the data handling issue is identified as CVE-2018-16395. The CVE (Common Vulnerabilities and Exposures) is a free and open industry standard database of publicly known cybersecurity vulnerabilities. It contains the description for the vulnerability. It also contains at least one public reference. You can also find more references on the link provided by Jake in the “Reference” section.
Description
The description explains the issue in more detail. It usually tells you the situation when this issue can creep up. It also details the reasoning behind the issue.
CVSS Score
The information reported by Jake also includes the CVSS (Common Vulnerability Scoring System) score. The CVSS score ranges from 0.0 to 10.0. This score reflects the severity of the vulnerability. The idea is to help developers and organizations prioritize their vulnerability management processes. As we can see above, the CVSS score for the data handling vulnerability is 9.8. This is an extremely high CVSS score.
As noted in the description, this issue can be “leveraged to create an illegitimate certificate.” This may then “be accepted as legitimate” during “signing or encryption operations.” Drawing from this knowledge, and the high CVSS score, we can understand that this is a really serious vulnerability. Hence, we should ideally tackle this on a higher priority.
CVSS Vector
The CVSS vector textually represents the rationale behind the CVSS score. You can use the guide here to identify the metric value from its corresponding string in the vector. For example, in the CVSS vector for data handling we have AV:N. This indicates the Access Vector metric has a value of Network.
How to Use Jake (Advanced)
Jake is built for one very specific task. Hence, it doesn’t need a ton of commands. However, there are some advanced options for a few special situations.
As Jake is open source, you too can start contributing to this awesome project! In case you want to contribute to its development or need debug data for a sticky situation, you can run the following:
$ jake —VV
The OSS Index results are cached for 12 hours. In case you want to clear out your local cache manually, you can run this:
$ jake —C
If you send too many requests then you may get rate limited. To resolve that, you need to set optional configuration of your OSS Index username and API key. But before you do that, you need to register for an account. Then to set the configuration, run the below:
$ jake ddt --snake or jake ddt -S
Support
Sonatype doesn’t support Jake. You cannot create support tickets for any issues. This is just Sonatype’s contribution to the open source community. OSS Index is also a free service. It just reports the data derived from public sources. It doesn’t provide additional human-curated intelligence, insights, nor expert guidance. Therefore, you should use Jake at your own risk tolerance.
But some projects need additional human guidance and expertise. For teams that need more support against open source risk, check out Sonatype’s Nexus Platform. It goes beyond public data sources, having analyzed more than 65 million components. This tool empowers your team to automate open source governance. It also helps scale DevOps and supports a wide range of languages and tools. Nexus Platform provides precise, curated, and actionable intelligence. It will aid you across your entire development life cycle and allow your team to release faster.
Conclusion
Jake is a free tool that will help you easily identify vulnerabilities in your Conda environment. It’s simple to use. It saves you tons of time. And it will empower you to develop Python projects much faster while controlling open source risk. Read more about Jake here.




