“The executive branch has for too long accepted antiquated and difficult–to-defend IT”, declared President Donald Trump in a new Executive Order released on Thursday, May 11th, 2017.
The Magnitude of Risk and Importance of a Plan
Over the past few years, we have witnessed mega-breaches that have impacted IT systems across our financial services industry, healthcare sector, and government. The vast majority of these breaches take advantage of weaknesses in software applications, according to the current and recent years of the Verizon Data Breach and Investigations report. The White House believes it is imperative that the United States modernize its IT infrastructure in order to better defend it.
Emphasizing the immediacy and magnitude of risks at hand, this new Executive Order asks each agency to identify critical infrastructure at the “greatest risk of attacks that could reasonably result in catastrophic regional or national effects on public health or safety, economic security, or national security”. If you want an idea of what a catastrophic event might look like, you only need visit the headlines coming out of the UK earlier today, where their national healthcare services, NHS, had been taken over by a ransomware attack -- preventing access to patient records, prescriptions, and insurance systems.

Rather than throw our collective arms up in despair convinced that systems will always be vulnerable to attack, the Trump administration is taking a proactive role in assessing vulnerabilities currently in our IT infrastructure, software, and their related supply chains. The Executive Order states, “Effective risk management involves more than just protecting IT and data currently in place. It also requires planning so that maintenance, improvements, and modernization occur in a coordinated way and with appropriate regularity.”
The Gluttony of Innovation
At Sonatype, we have long said, “software ages like milk, not wine”. Over the past three years, our State of the Software Supply Chain Report has shed light on the massive volume of software applications assembled with vast quantities of open source components sourced from an immense global supplier network. In 2016, these supply chains delivered billions upon billions of components to software development teams. While, on one hand, these practices improve net innovation and accelerate time to market, they also introduce huge volumes of very old and known vulnerable components that make it easier for our adversaries to successfully penetrate our critical IT infrastructure.
 A recent study by Sonatype revealed as many as 1 in 18 open source and third-party software components consumed by development teams had known security vulnerabilities. According to the new Executive Order, “Known but unmitigated vulnerabilities are among the highest cybersecurity risks faced by executive departments and agencies.” With regard to the unbridled use of vulnerable open source software components, the gluttony of our innovation is contributing to the fragility of our future.
A recent study by Sonatype revealed as many as 1 in 18 open source and third-party software components consumed by development teams had known security vulnerabilities. According to the new Executive Order, “Known but unmitigated vulnerabilities are among the highest cybersecurity risks faced by executive departments and agencies.” With regard to the unbridled use of vulnerable open source software components, the gluttony of our innovation is contributing to the fragility of our future.
Software Supply Chains and the Trust Gap
Unlike mature industries such as automobile manufacturing, most private organizations and government agencies don’t (yet) manage or govern their software supply chains. It’s imperative that our collective supplier-provided assets -- in this case, open source and third-party software components - are properly identified, tracked and quality-checked. There are often hundreds, if not thousands, of components used by a typical development team, and each component has tens, if not hundreds of dependencies as well as multiple versions.
Unfortunately, our dependence on components is growing faster than our ability to secure them. These shared components fall in the blind spot of most application security processes and are not top-of-mind when considering application risk. This creates a big trust gap.
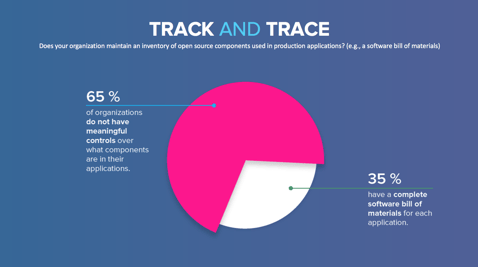
Just like a traditional supply chain, it has become impossible to manually manage the selection, tracking and inventorying of these supplier-provided components. The 2017 DevSecOps Community Survey of over 2,200 IT professionals revealed that only 35% of organizations maintain a complete software bill of materials to track which open source components were used in their applications.
Our software supply chains need the same type of automated visibility and management that have been mandated in other industries for years. The good news is: it costs far less and is far easier to implement.
Renewed Vigilance
The combination of growing component usage coupled with lack of security requires us to urgently re-evaluate our software supply chains and our traditional application security approaches to identify practical next steps for closing this security gap. Supply chain vigilance is a core component of Trump’s new Executive Order on Cybersecurity. Within 90 days of this order, a number of agencies will report to the President on “cybersecurity risks facing the defense industrial base, including its supply chain.”
Thankfully, a number of federal agencies and private organizations are already ahead of the curve. To counter the effects of massive component consumption, top performing development organizations are already embracing supply chain management best practices, including: (1) procuring components from fewer and better suppliers, (2) procuring only the best parts from those suppliers, and (3) continuously tracking and tracing the precise location of every component. Furthermore, Federal regulators and industry associations like Department of Defense, Department of Energy, IRS, FDA, FTC, UL, and FS-ISAC have take action over the past two years to build awareness and establish guidelines for sound software supply chain management practices. Current practices and lessons learned by these organizations and agencies should serve to better inform the U.S. government of present day cybersecurity risks.
While some might argue that this executive order mimics many efforts by previous administrations, the issuance of this new order confirms the Trump administration’s desire to continue defending and protecting our national IT infrastructure, software and other critical systems. You can read the full text of the Executive Order here “STRENGTHENING THE CYBERSECURITY OF FEDERAL NETWORKS AND CRITICAL INFRASTRUCTURE” Executive Order here.







