Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Part 1: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 17, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Just like automobile manufacturers, software “manufacturers” need to apply supply chain management principles for both efficiency and quality.
Read More...
Securosis Dives Deep into our 2014 Survey
By
Derek Weeks on July 02, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
There are two ways to motivate others to action: emotional appeal and fact based analysis.
Read More...
We're bringing sexy back, Sonatype hits the catwalk
By
Derek Weeks on June 24, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
Enthusiasm for securing the software supply chain is growing in both conversation and practice.
Read More...
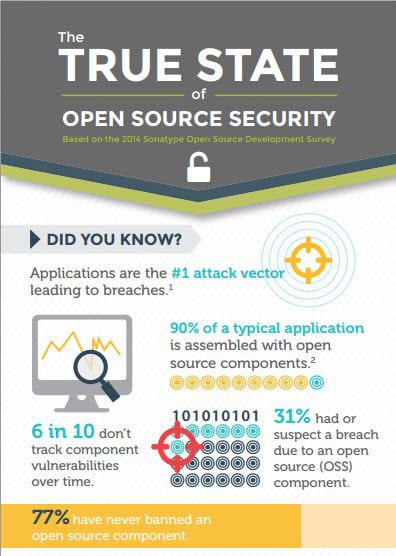
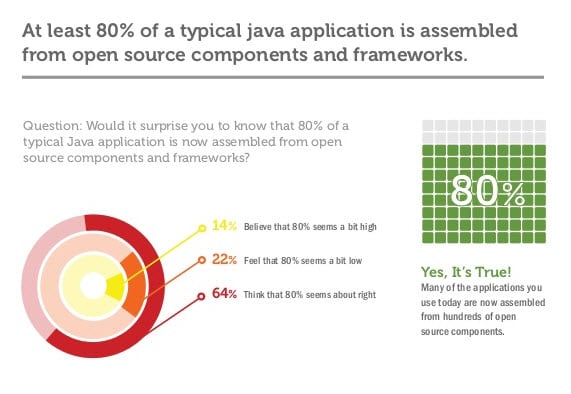
5 Things You Need to Know About Open Source Components
By
Mark Miller on June 04, 2014
Cyber Supply Chain Management and Transparency Act
5 minute read time
You can't get away from it. Thousands of open source components are being used in every industry, every day, to quickly build and deploy applications.
Read More...
On the Shoulders of Giants: Influential Books for Software Developers
By
Jamie Whitehouse on May 16, 2014
Sonatype Says
4 minute read time
While there are many books I have read during my career as a software engineer, there are a handful that have been influential in my thinking.
Read More...
Hacking Minecraft - A Metaphor for Bleeding Hearts
By
Jeffrey Wayman on May 09, 2014
minecraft
6 minute read time
Over a month has passed since HeartBleed was announced to the public, and while saturation into the mainstream media likely peaked shortly after that, it.
Read More...
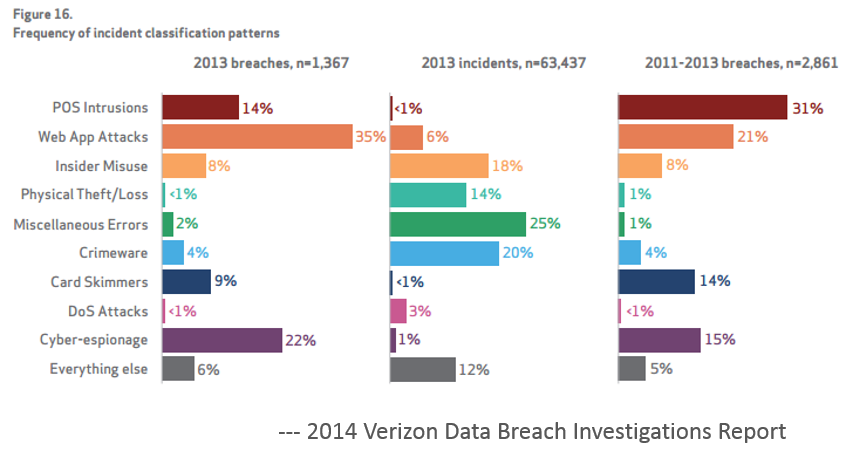
Like a Good Holiday, the Verizon Breach Report is Here
By
Ryan Berg on May 02, 2014
Sonatype Says
5 minute read time
Like a good holiday the Verizon 2014 Data Breach Investigation Report (DBIR) is something I look forward to every year.
Read More...
Are we doing enough to prevent future “bleeding hearts”?
By
Wayne Jackson on April 10, 2014
Sonatype Says
4 minute read time
As the HeartBleed bug wreaked havoc on the internet over the past few days, we at Sonatype began thinking about the lessons learned from this recent scare.
Read More...
DevOps: The Last Great Hope for Application Security?
By
Derek Weeks on April 08, 2014
Component Lifecycle Management
3 minute read time
Once upon a time, there was a great battle between speed and security. Development wanted to go fast. But, security wanted to slow down and be safe.
Read More...