Two months after we launched our 2017 report, we all learned that Equifax had been breached. The hackers attack vector was a known vulnerable open source component from the Apache Struts project.
The world changed, the conversations changed, but did we all change?
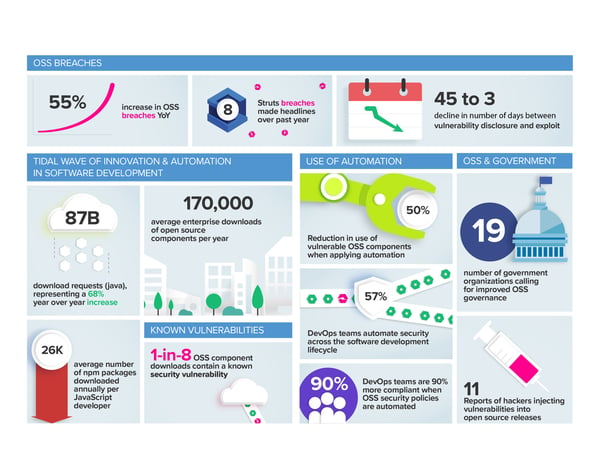
A series of high profile and devastating cyber attacks demonstrated that adversaries have the intent and ability to exploit, and in some cases plant, security vulnerabilities in the software supply chain. While Equifax was breached due to a Struts vulnerability, we also documented eight other Struts breaches this year. We also detailed a new battlefront of attacks on open source releases that impacted tens of thousands of developers.
In past reports we said all companies we’re becoming software companies, but this year, we crossed the chasm. From banking, to manufacturing, to healthcare, to entertainment; it’s no longer “innovative” startups disrupting established player - legacy companies are catching up. They’re building out armies of software developers, consuming extraordinary amounts of open source components, and equipping teams with tools designed to automate and optimize the entire software development lifecycle. Innovation is critical, speed is king, and open source is at center stage.
These three competing truths are why we develop the State of the Software Supply Chain each year, and why we’re excited to debut our fourth annual report today.
Like previous reports, the 2018 State of the Software Supply Chain Report blends a broad set of public and proprietary data with expert research and analysis. Unlike previous reports, we’ve identified new methods cybercriminals are employing to infiltrate software supply chains and an exponentially abbreviated mean time to exploit vulnerabilities.
Key findings include:
- Managing software supply chains through automated OSS governance
reduces the presence of vulnerable components by 50% - Downloads of known vulnerable open source components increased 120% YoY and their mean time to exploit compressed by 93.5% - or 4-fold
- DevOps teams are 90% more likely to comply with open source governance
when policies are automated - Public vulnerability databases lack information on more than 1.3 million
open source security advisories - Government regulation across the United States and Europe hints at software liability on the horizon
In addition to the points above, this year’s report offers expanded analysis across languages and ecosystems, to provide a more robust picture of the entire system. We’ve also more deeply explored how government regulations are impacting the world of open source as organizations struggle to self-regulate.
We recognize we have a unique vantage point within the open source community, and it gives us great pleasure each year to share some of our observations with you. We welcome any feedback you have, and hope you find this year’s report beneficial. You can download the full report at https://www.sonatype.com/2018-ssc.






