"Only with the introduction of trucks and tanks in World War I did horses finally become supplanted as the main assault vehicle and means of fast transport in war. Arabian and Bactrian camels played a similar military role within their geographic range", shared Jared Diamond, in his seminal 1997 book entitled Guns, Germs, and Steel: The Fates of Human Societies." In all these examples, people with domestic horses or camels [then later with trucks and tanks], or with improved means of using them, enjoyed an enormous military advantage over those without them."
Throughout all of history, elite societies have both been formed, and crushed, through the advent of new technologies or the availability of better resources to them. The have's have outpaced the have nots. The better equipped prospered and those without, languished.
Evidence of Horses and Camels
In our most recent State of the Software Supply Chain Report, I revealed evidence that cybersecurity adversaries had dramatically compressed the time between vulnerabilities being announced and their exploits being spotted in the wild. Between 2006 and 2017, the mean time between announcement and exploit had compressed from 45 to 3 days.
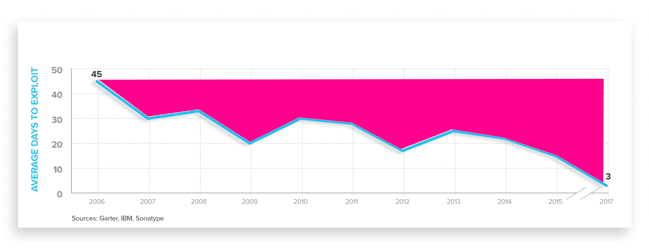
Furthermore, I shared a compilation of evidence pointing to a new battlefront of software supply chain attacks where adversaries were injecting malicious code into OSS projects using the maintainer-level credentials; these moves effectively compressed adversarial time to exploit down to zero.
For cybersecurity and DevOps pros, the advantage rests with the adversaries. The attacks (guns), malicious code and known vulnerabilities (germs), and tools (steel) used by today's adversaries are the equivalent of the trucks and tanks used in World War I, while most security pros and many DevOps practices are still relying on horses and camels.
Advantage by the Numbers
Further evidence of adversarial advantage can be found in our 6th annual DevSecOps Community Survey, released today. We queried 5,558 developers and DevOps pros to better understand what advances they've made, training they've received, and challenges they've faced. While significant advancements have been made by those with DevSecOps Elite practices, two responses standout. When asked if organizations suspected or experienced an open source breach in the past 12 months, 1 in 4 participants admitted that adversaries had successfully breached their environments. Entry points were found through open source components and web applications.
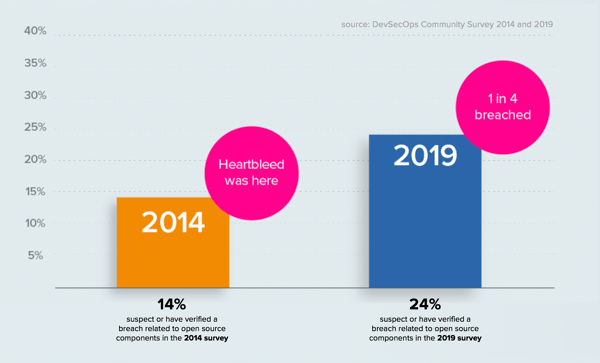
Simply put, the applications they are building and deploying are being compromised at an alarming rate. To put this more into perspective, look no further than the report from three weeks ago revealing that EU officials have received 59,000 breach notices since GDPR became law eight months ago.
DevSecOps Elite Practices are Encouraging
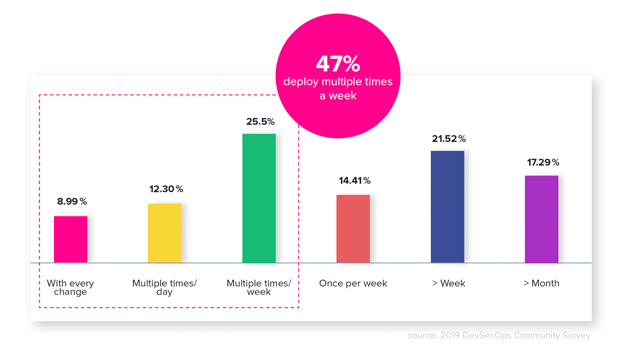
Hope is not lost. Clear evidence of progress by elite DevSecOps organizations was noted throughout the survey responses. For example, as organizations matured their DevOps practices, their frequency of deploys continues to increase. Over 47% of respondents in this year's survey said they were deploying changes into production multiple times per week. If adversaries are getting faster at exploiting vulnerabilities, DevOps organizations that can identify cybersecurity risks and remediate them sooner can better defend themselves.
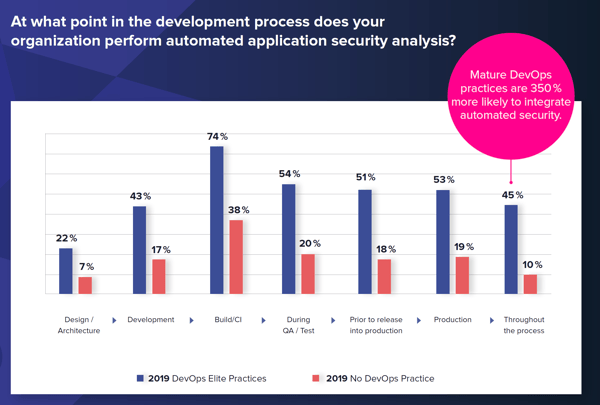
As with last year's survey, we analyzed differences between organizations with little to no DevSecOps practice and those with mature DevSecOps practices (that we refer to as the "elite" group). Time and again, we saw the "elite" organizations far outpacing their "no DevOps" peers with greater investments in automated tooling, training, and cybersecurity planning, including:
-
DevOps Automation - Elite DevSecOps practices are 700% more likely to have fully integrated and automated security practices across the DevOps pipeline. They also have increased feedback loops that enable security issues to be identified directly from tools.
-
Open Source Controls - 62% of respondents with elite programs have an open source governance policy in place where automation improves adherence to it, compared to just 25% of those without DevOps practices.
-
Container Controls - 51% of respondents with elite practices say they leverage automated security products to identify vulnerabilities in containers, while only 16% of those without said the same thing.
-
Training - Organizations with elite DevSecOps practices are 3x more likely to provide application security training to developers than those organizations without DevOps practices.
-
Preparedness - 81% of those with elite practices have a cybersecurity response plan in place compared to 62% of those without DevOps practices.
In elite programs, their use of automation, focus on controls, and preparation for the near inevitable breach, are all part of their proactive programs aimed at thwarting or minimizing adversarial threats.
It's Not Just About Fast
As Diamond pointed out, adversarial advantage lied not just with those who had adopted faster war resources or machines, it was held by those who "improved means of using them". The same has been said of DevOps and DevSecOps practices.
You'll remember in 2010 when Dave Farley and Jez Humble penned Continuous Delivery that they advised all of us to "build quality in". They were not simply writing the book to advise us how to accelerate.
Three years later, Gene Kim and his other co-authors published The Phoenix Project. Across it's pages, the authors educated us on the three ways of DevOps. You'll also remember that the first way of DevOps was to understand the performance of the entire system end-to-end and never pass a known defect downstream.
As the number of successful breaches continue to rise, elite DevOps organizations are making investments to better protect themselves not just by building stronger castle walls. These organizations are taking steps to integrate and automate security across the development lifecycle. In many cases, they are not relying on traditional application security tools; they are deploying new technologies to reduce quality and security defects sooner and more often. They are also making significant investments in training employees in secure coding practices.
Success favors the prepared. What means are your organization improving?
To learn more about the practices, training and investments being made by the DevSecOps Elite, I invite you to download a copy of the 2019 DevSecOps Community Survey today.







