Happy New Year!
To kick off 2019 we will be covering a vulnerability that is complex in context. All developers are aware of the varieties of privilege escalation and Cross-Site Scripting (XSS) that allow bad actors to exploit their way to sensitive files. CVE-2017-5662 is another example of one of those vulnerabilities and, in this case, allows a very specific vector for the hack – SVG files.
Name of the Vuln/Sonatype ID: CVE-2017-5662
Type of vulnerability: DoS
Components affected: Apache Batik before version 1.8
Vulnerability Description:
SVG file exploits are not new, nor are they unique. With literally thousands documented over the years, SVG file attacks are common enough that they’ve inspired the creation of a couple of different filters to make them somewhat safer. Their capability as a scalable XML text file for images versus true image files like JPEG, GIF, or BMP permit both their design flexibility and inherent danger.
Because SVG files are often simply treated as images and accepted in lieu of traditional image files, it is common for developers to fall into routine thinking and treat any user-submitted SVG file as syntactically valid. However, because at their core, SVG files are far more dynamic, there is a high probability of their misuse if every XML tag and value in the SVG file is not scrutinized when they are processed. As a minor example, an SVG created with an older, deprecated standard could be storing a metadata value, such as the name of the Author within it. If a developer is not careful and blindly trusts these values, rendering them can lead to XSS attacks if an attacker is able to supply a crafted SVG.
The Attack Mechanics:
Treating SVG files carelessly means that compromise is much easier than developers might think. It only takes a few lines of malformed XML against a root account for an attacker to gain access to sensitive files or data, or initiate a Denial of Service (DoS) by triggering an amplification attack.
The critical point to remember is that SVG files aren’t image files and, as such, their XML format makes them a powerful means to exploit a variety of vulnerabilities.
In this case, an image could be worth a thousand words - literally.
A Real-world example:
CVE-2017-5662 specifically addresses an Apache Batik manipulation that allows a bad actor to create malformed XML in an SVG file in order to create a DoS attack on the server.
An example of a real, crafted SVG file is: https://issues.apache.org/jira/secure/attachment/12776137/ssrf.svg
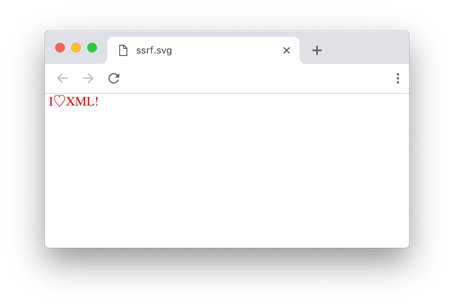
When rendered within a web browser or an SVG viewer, a simple text from the SVG document is displayed: I♡XML!
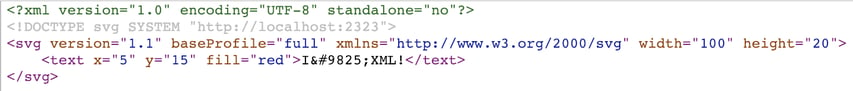
However, the XML source reveals an external DTD link within the <!DOCTYPE> tag, which if parsed by the application could cause security issues, depending on how it is being used. In this particular case, the crafted SVG may cause Server-Side Request Forgery (SSRF) attacks or be misused for port-scanning.
Preview of the SVG file in Chrome web browser:
Source of `ssrf.svg`:
When inspected with netcat (nc), the following HTTP request headers are observed having been sent sent by Apache Batik, as the SVG is parsed.
chaotic@m0lly:~$ nc -l 2323
GET / HTTP/1.1
User-Agent: Java/1.7.0_60-ea
Host: localhost:2323
Accept: text/html, image/gif, image/jpeg, *; q=.2, */*; q=.2
Connection: keep-alive
As you can see, the command is issued to accept text/html and then keep the connection open. If the server processes the syntax as written, a DoS attack is executed.
Why it matters:
Administering an attack like the SVG vector exploit could take down a server running any Batik component version before 1.8. In addition, depending on the context and user being compromised, could expose an organization’s most sensitive data.
The best remediation path:
Upgrade to Batik version 2.2, where this vulnerability has been fixed.
DevOps-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers. Customers of Sonatype Nexus were notified of CVE-2017-5662 within days of the discovery. Their development teams automatically received instructions on how to remediate the risk.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities.
If you're not a Sonatype customer, and want to find out if you're using the vulnerable version of Apache Batik in a specific application, you can use Sonatype's free Nexus Vulnerability Scanner to quickly find out.








