Around this time last year, InfoWorld called 2022 the “the year of software supply chain security.” Unfortunately, one year later still feels very much like we’re back at the beginning. Our data shows software supply chain attacks are on a radical incline, increasing an average of 742% yearly since 2019. Bad actors continue to target open source project ecosystems–and there’s no reason to believe next year will be different.
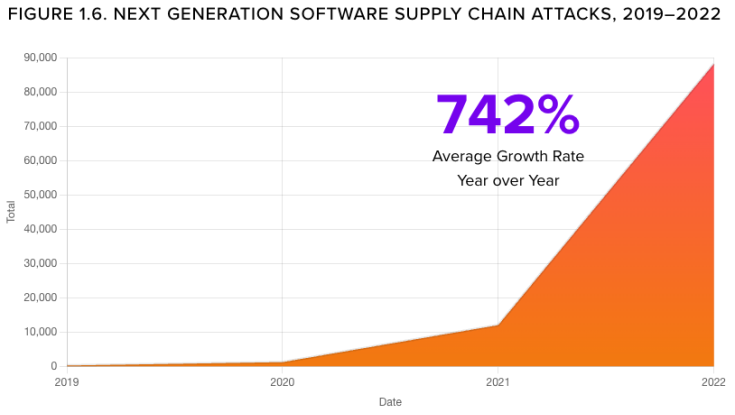 Increase in Software Supply Chain attacks since 2019.
Increase in Software Supply Chain attacks since 2019.
These attacks seem to correspond with the ongoing growth of the software supply chain. Our data on open source component downloads is showing continued growth for the top four development ecosystems.
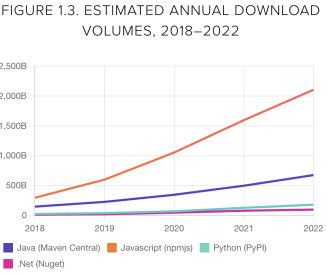
Download trends by ecosystem since 2018
On top of this, modern applications consist of 85% third-party open source components. One report surveyed IT leaders, who expect to increase their use of open source software by 80% for emerging technologies.
The use of open source in software development is a great success story for the tech industry. But the growth, widespread nature of open source software, and ease of publishing make it an attractive target for bad actors.
Today we look ahead with the help of experts at Sonatype to see what changes in development practices, open source security, and regulation will define 2023.
The year of the SBOM
Thanks to the steady pro-regulation drumbeat of industry leaders, increasing federal requirements stemming from President Biden's Cybersecurity Executive Order and the wake of the breach that impacted SolarWinds, the idea of needing a Software Bill of Materials (SBOM) is catching on.
The topic is also gaining prominence outside the U.S., with Japanese and European (the Cyber Resilience Act) SBOMs expected in the coming year.
However, many organizations treat their creation as a simple checkbox for policy compliance, and not part of a larger effort:
In the words of our CTO Brian Fox:
“With the looming deadlines established by memo M-22-18 and Executive Order 14028, SBOMs will dominate a large part of the cybersecurity conversation in 2023. SBOM capabilities are rapidly emerging as table stakes for cyber resiliency, and with good reason—they are critical for better dependency management and reducing the time to fix vulnerabilities.
However, SBOMs alone are not the solution. I’ve seen so many organizations scrambling to meet the letter of the law, but without taking a step back to think about how they should really be managing their software supply chain. What good is having an ingredient list if you don’t know where the ingredients come from, or if they’re poisoned?
The ultimate goal of these regulations is to better secure and protect software supply chains. The SBOM is an extremely important tool, and you can’t manage your software supply chain without it, but it’s only part of the action needed to improve our security posture.”
Sonatype’s VP of Product Innovation Dr. Stephen Magill added:
“Pairing SBOMs with high-quality vulnerability data is where the magic really happens. This combination lets you set up continual and automated monitoring of your open source vulnerability risk."
Security pains on the horizon
There’s no way to minimize the serious concerns in the year ahead. From public school systems to energy infrastructure, 2022 showed us that no industry is immune from attacks. We'll likely see the same rough waters in 2023, underscoring the importance of software supply chain management.
Research from Gartner suggests digital supply chain risk is a serious trend, with 45% of organizations worldwide experiencing attacks on their software supply chains. Data on cybercrime trends in 2023 suggests we’ll see costs of $11 trillion in the coming year. Even some insurance companies see cyberattacks as “uninsurable”.
A wake-up call for open source users
Many groups defending their security posture have pointed to open source project maintainers as responsible for failures. As a consequence, we’ve also seen hesitation around the use of open source software.
Our data has shown this is unfounded, and that open source consumers are more often at fault. The vast majority of risk involved with using open source lies with development teams downloading outdated software. Even high profile concerns like the Log4j vulnerability that were resolved over a year ago are still seeing poor adoption of fixed versions.
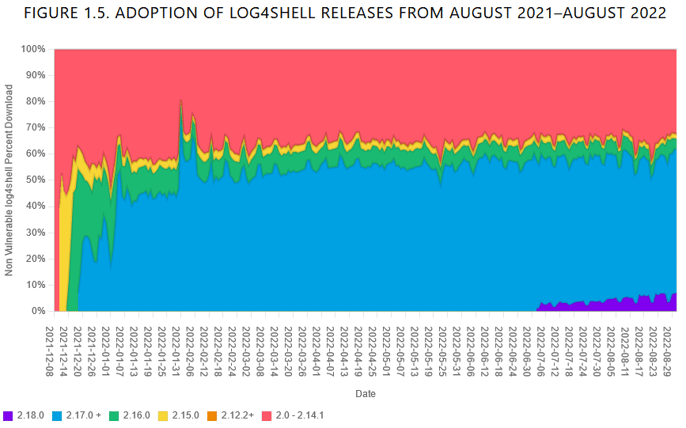 Graph of Log4Shell release adoption over time. The red zone represents percentage downloads of vulnerable versions over time. Image from the 8th Annual State of the Software Supply Chain report.
Graph of Log4Shell release adoption over time. The red zone represents percentage downloads of vulnerable versions over time. Image from the 8th Annual State of the Software Supply Chain report.
Again, Brian Fox:
“Shrinking security teams and stagnant cybersecurity budgets mean bad actors could potentially become the biggest winners of the current economic climate. The good news is that there are steps organizations can take to immediately improve their security posture. Consumers are driving 96% of the risk in open source – if we change even a fraction of those consumption behaviors and use the supply management tools that are currently at our disposal, enormous risk is immediately eliminated from the industry.”
We’ve seen this year in Sonatype’s own data that 95% of vulnerable downloads had a non-vulnerable option available. Solutions will need to be tailored for each organization’s needs – with rising standards for SBOMs and Vulnerability Exchanges becoming more adopted. Projects like OpenSSF’s Scorecards and Sigstore will no doubt be adopted widely and improve the quality of software and upstream development in the long run.
For organizations, the software supply chain will become a C-Suite-level priority.”
Addressing open source consumer behavior is the key to improving negative security trends in the year ahead.
Efficiency is the name of the game
The continuation of economic austerity into 2023 will put even more pressure on developers than ever. DevOps is a great phenomenon but has, in some respects, gone too far in making many software developers solely responsible for security. Next year will be all about adjusting the balance.
This economic uncertainty is going to force organizations to implement automation. That will empower developers’ decision-making, giving them better visibility so they can focus more on innovation – not putting out fires. No company can afford to neglect the investment needed to inject quality of life into developers’ everyday workflow.
Sonatype’s data suggests companies that invest in automated security also see gains in development efficiency, as discussed in Chapter 4 of our 2020 State of the Software Supply Chain report.
“Cybersecurity is a necessity in today’s world, meaning cyber budgets tend to have a little more resiliency than the larger tech industry. That said, reduced teams and limited developer capacity will force organizations to embrace efficiency and invest in automated tooling”. – Wayne Jackson, CEO, Sonatype
It’s not all bad news
Small steps can make a big impact
Although attackers are getting more sophisticated, the good news is that gradual effort has real value. Even basic protections can foil attackers in the coming year, but it’s critical you know where attacks are coming from.
“Bad actors will always take the path of least resistance. The malicious attacks we’ve seen lately have been low in sophistication, mirroring consumption behaviors. We’ll continue to see direct contribution attacks into source code because it’s easy and it’s working. There needs to be a more holistic understanding of software supply chain hygiene, and how open source consumption plays a direct role in that.” – Brian Fox
2023 can still be a great year
In addition to a lot of long shadows cast over 2023, we are happy to share an encouraging note from Wayne Jackson:
“I’ve overseen multiple companies through four economic downturns. While difficult, sometimes these downturns bring out the best in organizations, and create an environment that allows product leaders and continual innovators to shine.”
With that, we at Sonatype wish everyone a safe and happy 2023.

Image credit: Soroush Karimi
Related
- Why High-Quality Data is Critical for Effective Software Composition Analysis
- EU Cyber Resilience Act: Good for Software Supply Chain Security, Bad for Open Source? (Brian Fox)
- Lessons Learned From 2022 And Technology Predictions For 2023 (Forbes)
- SBOM Quick Start Guide for Sonatype Lifecycle customers