Yesterday, I reported that Apache Airflow servers belonging to various firms and individuals had not been patched. These servers, most of which were still running the 2015 version of the workflow management platform, Airflow, were caught leaking thousands of credentials and configuration secrets, due to lax configuration and security practices, according to researchers at Intezer.
Most of these issues could have been avoided by simply checking the configuration and upgrading Airflow to version 2, which comes with extensive improvements and security enhancements.
While that was already an important lesson in why you should update versions promptly, an even bigger issue emerged today. Apache has disclosed what some cybersecurity experts have called "a nasty 0-day path traversal" in HTTP server version 2.4.49.
Zero-day actively exploited in the wild
Tracked as CVE-2021-41773, the vulnerability is the result of an incomplete path normalization logic implemented in the Apache HTTP server 2.4.49 that in turn introduced a vulnerability. Unfortunately, the vulnerability was exploited in the wild before it was reported to the Apache project, making it a zero-day.
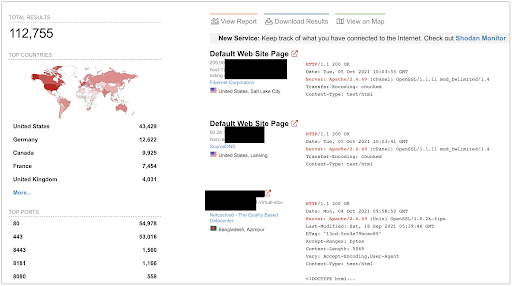
Although the issue only impacts web servers running Apache "httpd" v2.4.49 and not earlier versions, Shodan search results show there are over 112,000 Apache servers across the globe running that version, with about 40% located in the U.S.:
"An attacker could use a path traversal attack to map URLs to files outside the expected document root. If files outside of the document root are not protected by "require all denied" these requests can succeed. Additionally this flaw could leak the source of interpreted files like CGI scripts," reads Apache's security advisory.
Ash Daulton along with the cPanel Security Team reported the vulnerability to Apache on September 29th, with Apache releasing a fixed release 2.4.50 on October 4th.
Update: The fix for CVE-2021-41773 made into 2.4.50 was deemed incomplete, and a new CVE has been assigned to this vulnerability, CVE-2021-42013, along with an "emergency patch" in 2.4.51.
The path traversal fix previously made in 2.4.49 did check for presence of path traversal characters ("../") but was incomplete. It did not take into account the possibility of an attacker providing the percent-encoded versions of these characters. The new fix that went into the "httpd" server version 2.4.50 now checks for "%2E" and "%2e" which is the encoded representation of the dot (".").
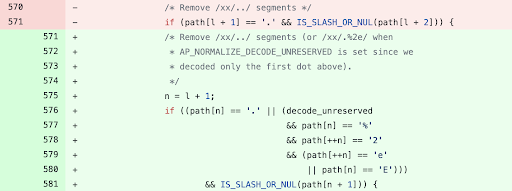
Yann Ylavic, member of the Apache HTTP server project team, notes the fix should now normalize the second dot in the URL path when the path is preceded by a dot.
"As Apache HTTP Server 2.4.49 was only released a few weeks ago it's likely many users will not have upgraded yet," an Apache spokesperson told BleepingComputer. "If and how this issue can be exploited is highly dependent on how users will have configured the server."
Those using "httpd" version 2.4.49, should upgrade to the latest version rather than using access control configuration as mitigation, advises Apache. On default installations, threat actors can exploit the vulnerability to obtain the source code of interpreted files, such as CGI scripts.
Importance of patching security vulnerabilities urgently
Discovery of both this Path Traversal zero-day and the case of Apache Airflow servers at leading tech firms leaking thousands of credentials, speak to the importance of prompt patching. The latter also demonstrates how simple misconfiguration flaws and going with the "default" configuration options can spill out secrets.
Path Traversal flaws are not to be underestimated either. Despite repeated reminders and advisories issued by Fortinet, the years-old VPN firewall vulnerability (CVE-2018-13379) continues to be exploited even today, because many entities are behind on patching.
This year, attackers exploited the Fortinet past traversal flaw to leak passwords from over 500,000 VPNs. That's 10 times the number of VPN firewalls that were compromised last year through the same exploit.
As I have said repeatedly, there are three takeaways from incidents like these:
- Active exploitation of assets begins almost immediately after vulnerability disclosures, even the most well-coordinated ones, are made public. Although for zero-days, the active exploitation precedes vulnerability disclosures making the scenario even worse.
- Attackers eye public exploits and constantly mass scan networks for applications vulnerable to new and years-old, but popular flaws, such as the Fortinet VPN vulnerability.
- Not every fix may be sufficient: something the Sonatype Security Research team has seen time and time again. Just because a vendor claims to release a fix for a vulnerability, doesn't always mean the fix is adequate or complete. As we see in the case of Apache's Path Traversal zero-day, clever threat actors can sometimes find a workaround to bypass a security fix.
As such, while the traditional advice to regularly update your applications to properly vetted fixed versions remains applicable, security professionals are constantly racing against cybercriminals and time, and have to be proactive.
The same goes for developers building the software applications the world relies on.
Manually monitoring CVE feeds and hard-to-find vulnerability disclosures, and then applying mitigations is no longer feasible, when your time should be going towards doing what you love: building kick-ass software.
Solutions like Sonatype Container provide a comprehensive approach to secrets management and configuration assessment, further extending runtime threat protection and access control to your production containers.
Sonatype's world-class security research data, combined with our suite of software supply chain and open source security solutions protect your developers, customers, and software development life cycle (SDLC) from vulnerabilities and malware.






