Bracing for impact... or how one Sonatype Engineer responded to the Apache Struts2 announcement while dealing with a hurricane bearing down on him.
Date: Tuesday, September 12th, 2017
By: Ryan Knell, Application Security Researcher
It’s been a long week...
It’s well understood that the majority (up to 90%) of exploits of a given vulnerability come after a public disclosure, not before. For this reason, whenever a high-impact vulnerability is discovered our data research team has a special expedited process we follow with the aim of ensuring our customers are able to respond immediately.
Earlier last week, we had just finished expedited research of Struts vulnerabilities s02-51 and s02-52.
Separately, since I live in Florida, I had been keeping an eye on the projected track of Hurricane Irma. Water and bread are hot commodities and difficult to find. On Thursday, September 7, 2017 I woke up at 3:30 AM (EST) to scour Walmart. I decided to buy a portable grill, spatula, charcoal, and snacks. Unfortunately, there was still no water on the shelves. I came back home to get gas cans from the garage to them fill up.
At 3:36 AM...
as I was looking around at Walmart, the research team received an alert email from one of monitoring systems hinting that a new struts vulnerability was about to be released.
At 5 AM...
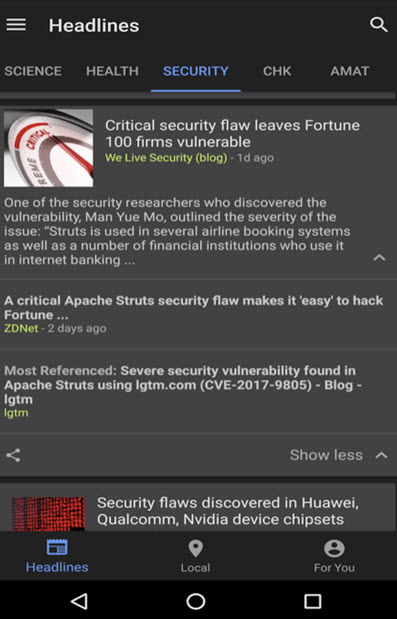
I tried to relax and checked the latest hurricane advisory. There wasn’t much of an update, so I started skimming through my news feeds. I saw that the Struts2 Remote Code Execution vulnerability - CVE-2017-9805 (the ones we had already researched earlier in the week) had made it to the news
 [Screenshot of the security news feed from my phone]
[Screenshot of the security news feed from my phone]
I immediately thought about that earlier hint from our monitoring system and went to check the latest Struts security bulletin. I noticed there was a new Struts vulnerability in the bulletin, S2-053 (CVE-2017-12611), which was also remote code execution. Half asleep, I confirmed we had a new critical vulnerability from one of our monitoring feeds and that I was the first of the team to pick it up, so I immediately began researching the vulnerability. Hurricanes are great for research!
The clock starts ticking...
Knowing this would be important for our customers to receive an immediate notification in our Nexus Lifecycle product, I immediately kicked off our Fast Track process. I should explain here that we have two speeds for performing research. Fast Track and Deep Dive. Fast Track is critical in getting advisory-accurate information to our customers within hours of discovery. Deep Dive is the process that provides the enriched security metadata around a specific vulnerability and corrects many inaccuracies denoted in the original security advisory.
After gathering my initial security research data, checked to see who else on the team was available for a review. Knowing that another member of my team, Adam, was also based in Florida and likely up storm prepping, he was my first target:
ryan> hey
adam> hey. how’s the prep going?
ryan> coming along. you?
adam> getting there
ryan> looks like we’ve got another issue with struts
adam> oh?
ryan> RCE
Adam performed a peer review of my research by 7:21 am and confirmed the root cause of this vulnerability: a sub-component of Apache Struts2 called `Apache Freemarker`. Using the Struts2 s2-053 bulletin as an example, if a parameter such as `redirectUri` is forcefully evaluated as an expression as seen below, the attacker could craft a request resulting in Remote Code Execution (RCE) when the Freemarker Template engine processes the request.
<@s.hidden name="redirectUri" value="${redirectUri}" />
2 hours have passed...
We have a critical vulnerability on a popular Struts component; we need to get this data to our customers immediately. While our fast-track process is designed to get security issues to our customers within a day, we have a tiger team process that is designed to get high-impact security issues to our customers in hours. Since this Struts issue was a high-impact vulnerability, it qualified for the tiger team process. Our tiger team process combines the Fast-Track and the Deep Processes in order to give complete and accurate information to our customers in a more timely manner than Fast Track alone.
8 hours have passed...
the research is finished, peer reviewed, customer facing enhanced metadata completed, and the research has been processed by our implication systems. The data is pushed to our Lifecycle Product and available to customers. Any customers who are affected will now receive an alert informing them of the new information, and they will immediately understand which applications are affected and combined with the deep research provided, how to begin remediation.
As of today, September 12, 2017...
Many days have passed since we Tiger Teamed this key Apache Struts research into the product and our customers started remediations. However, the official advisory that drives many other tools is still not fully published in the NVD...merely showing that the number is reserved. Here's the content as of this writing a full 5 days later:
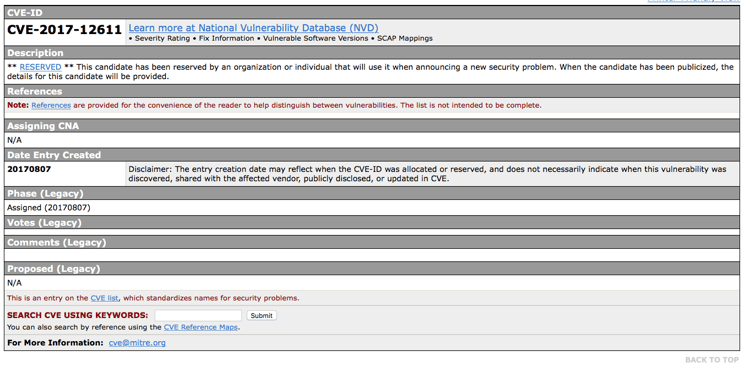
(btw this is not an uncommon situation, Brian Fox wrote about this same thing during the commons-collections event.)
Any products that don't provide a broad team of researchers who are able to validate, vet and correct disclosures are leaving you exposed, long after the attackers have been notified. Although the sleepless night of hurricane prep gave me a few extra hours head start, other nights I rest well knowing that the automated processing and the broad Sonatype research team ensure a rapid response every time.
Meanwhile, at home, there has been severe impact to the state of Florida ranging from wind to flood damage. I decided to hunker down and ride out the storm here in Jacksonville, Florida where the St. Johns river has flooded local communities and the beach areas were flooded. I was fortunate to avoid the brunt of the flooding, but many others were not.
Ryan
