Guess who's back? Earlier this month, CVE-2021-22114 in spring-integration-zip, returned for the second time to cause havoc.
The vulnerability originates due to failure to sufficiently sanitize user supplied input, which is perhaps one of the biggest problems in secure development. In this case, failure to sanitize archive entry names prior to extraction allows an attacker to traverse beyond the intended root directory and extract files to an arbitrary location, possibly overwriting existing ones.
To help everyone understand what this all actually means, we're taking a deep dive into this returning vulnerability.
Name/Vulnerability Identifier: CVE-2021-22114
Type of Vulnerability: Path Traversal
Severity:
CVSS 3.1 Score: 5.3 / Medium
CVSS 3.1 Metrics: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:N/I:H/A:N
Components Affected:
Mave:
Org.springframework.integration:spring-integration-zip
[1.0.2.RELEASE, 1.0.4.RELEASE)
However, this is not the first time we see this issue. This is the second attempt at fixing a Path Traversal vulnerability which was originally reported as CVE-2018-1261. In the fix released for this CVE, the project developers made an initial effort to identify traversal characters and throw an exception if malicious behavior was detected.
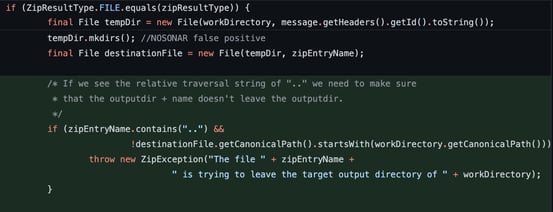
Image: Fix implemented for CVE-2018-1261. Path check on FILE type only.
This was done only for the file type and did not cover the case of Byte Arrays. An attacker could use Byte Arrays to bypass the initial check and the framework would return the errant path to the user application to further process. This insufficient fix resulted in CVE-2018-1263.
This time around, the path checks were implemented in their own function, 'checkPath,' and respectively called where needed.
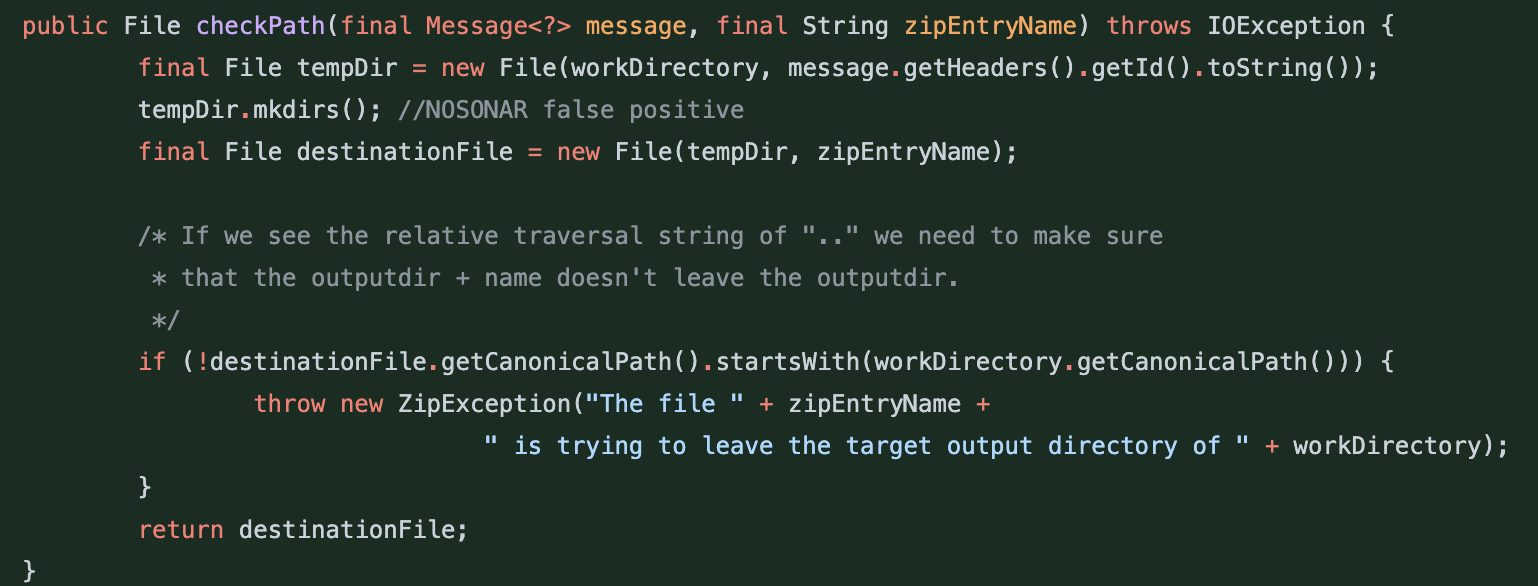
Image: Fix implemented for CVE-2018-1263. Path check moved to a helper function.
Now, 2 vulnerabilities and 1 insufficient fix into our journey, 3 years later researchers were able to bypass previous restrictions and a third vulnerability arose, CVE-2021-22114. Attackers could craft special archive entry names that met the condition of starting with the working directory but leveraged file separators to then traverse beyond the intended root directory hence exploiting the path traversal.
A stronger check is now implemented and a release containing the fix for CVE-2021-22114 is available.
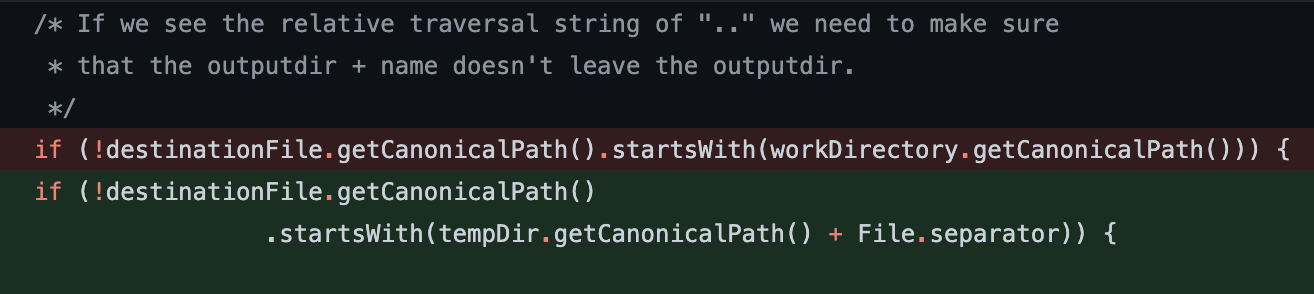
Image: Hardened path check implemented for CVE-2021-22114.
Our Security Research team was quick to expedite our complete deep dive research on the vulnerability, which was then published to Sonatype Intelligence and all of our products. Customers of Sonatype benefit from the following information.
Sonatype's take:
The `spring-integration-zip` package is vulnerable to Arbitrary File Write due to Path Traversal. The `checkPath()` method in the `UnZipTransformer` class fails to sufficiently sanitize archive entry names prior to extraction. Consequently, entries containing certain traversal character sequences may result in extraction to unintended locations. A remote attacker can leverage this vulnerability to overwrite arbitrary files accessible to the affected process by supplying an archive that exploits this issue.
Note: This vulnerability exists due to an insufficient fix for CVE-2018-1263.
Our recommendation:
We recommend upgrading to a version of this component that is not vulnerable to this specific issue.
Versions containing the fix: 1.0.4.RELEASE and later.
Note: If this component is included as a bundled/transitive dependency of another component, there may not be an upgrade path. In this instance, we recommend contacting the maintainers who included the vulnerable package. Alternatively, we recommend investigating alternative components or a potential mitigating control.
If you're not yet a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype's free Sonatype Vulnerability Scanner to quickly find out.
Visit the Sonatype Intelligence Insights page for a deep dive into other vulnerabilities like this one. Or subscribe to our blog to receive Nexus Intelligence Insights hot off the press.







