The Department of Homeland Security Cybersecurity and Infrastructure Security Agency (DHS CISA) recently released a list of the top 10 most commonly exploited software vulnerabilities across the last four years.
Apache Struts was the second most attacked technology on the list. Apache Struts is an open source web application framework for developing Java EE web applications. While it made headlines as the root cause within the Equifax breach, it was also tied to six other breaches that year and in years since.
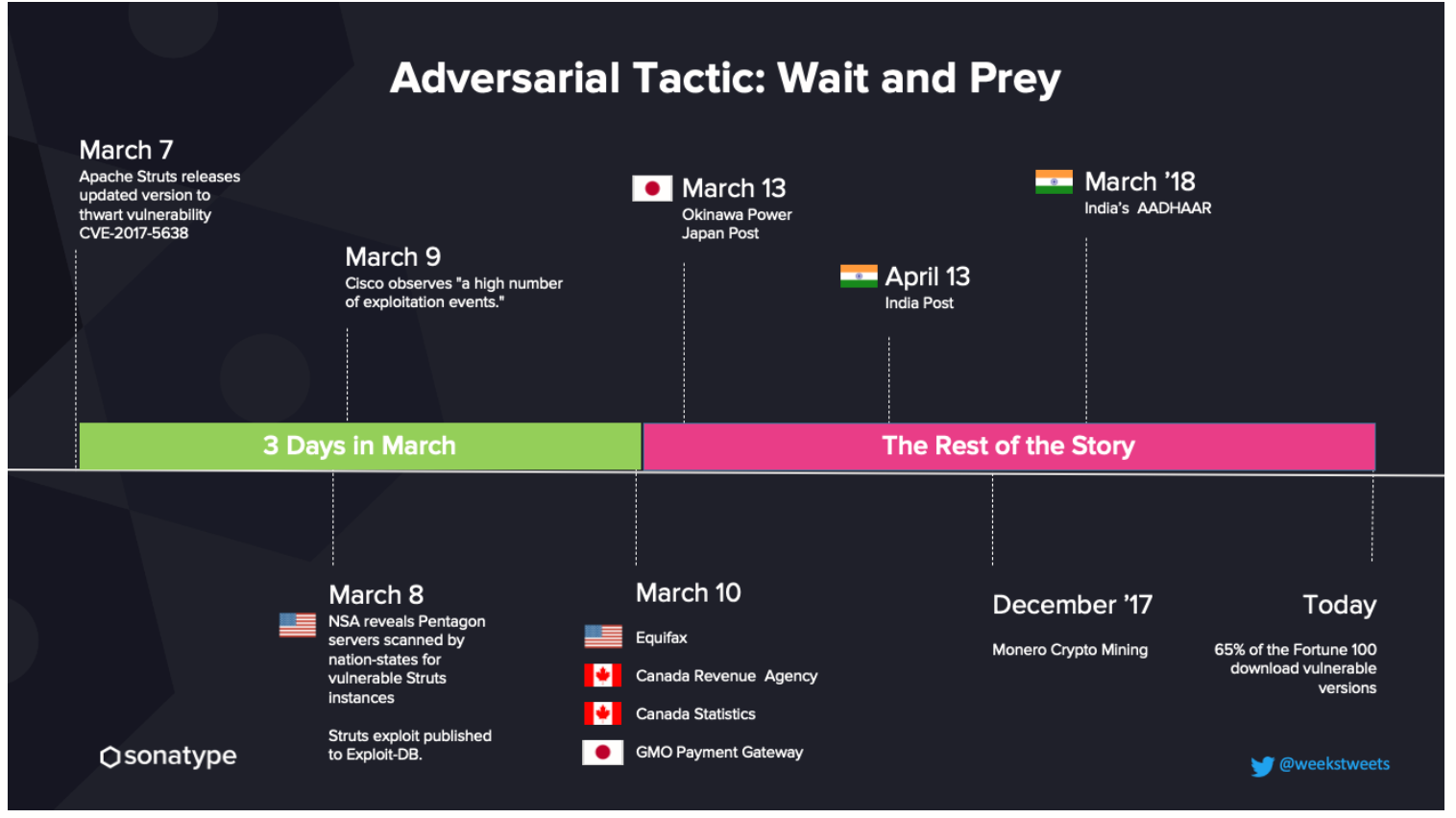
Adversaries breached web applications at Equifax and six other organizations that relied on the Struts framework. Breaches occurred within three days of the vulnerability being announced.
According to Wikipedia:
[Struts 2] uses and extends the Java Servlet API to encourage developers to adopt a model–view–controller (MVC) architecture. Struts 2 has a history of critical security bugs, many tied to its use of OGNL technology; some vulnerabilities can lead to arbitrary code execution. It was reported that failure by Equifax to address a Struts 2 vulnerability advised in March 2017 was later exploited in the data breach that was disclosed by Equifax in September 2017.
Note that this Struts CVE is dated back to 2017, yet CISA and the FBI classify it as one of the most successful breach entry points by adversaries. It has not only been known to be vulnerable since 2017, but known safe versions of Struts were made available on the same day in 2017 that this vulnerability was announced. In other words, the breaches were 100% avoidable if the development teams took the effort to update their Struts framework.
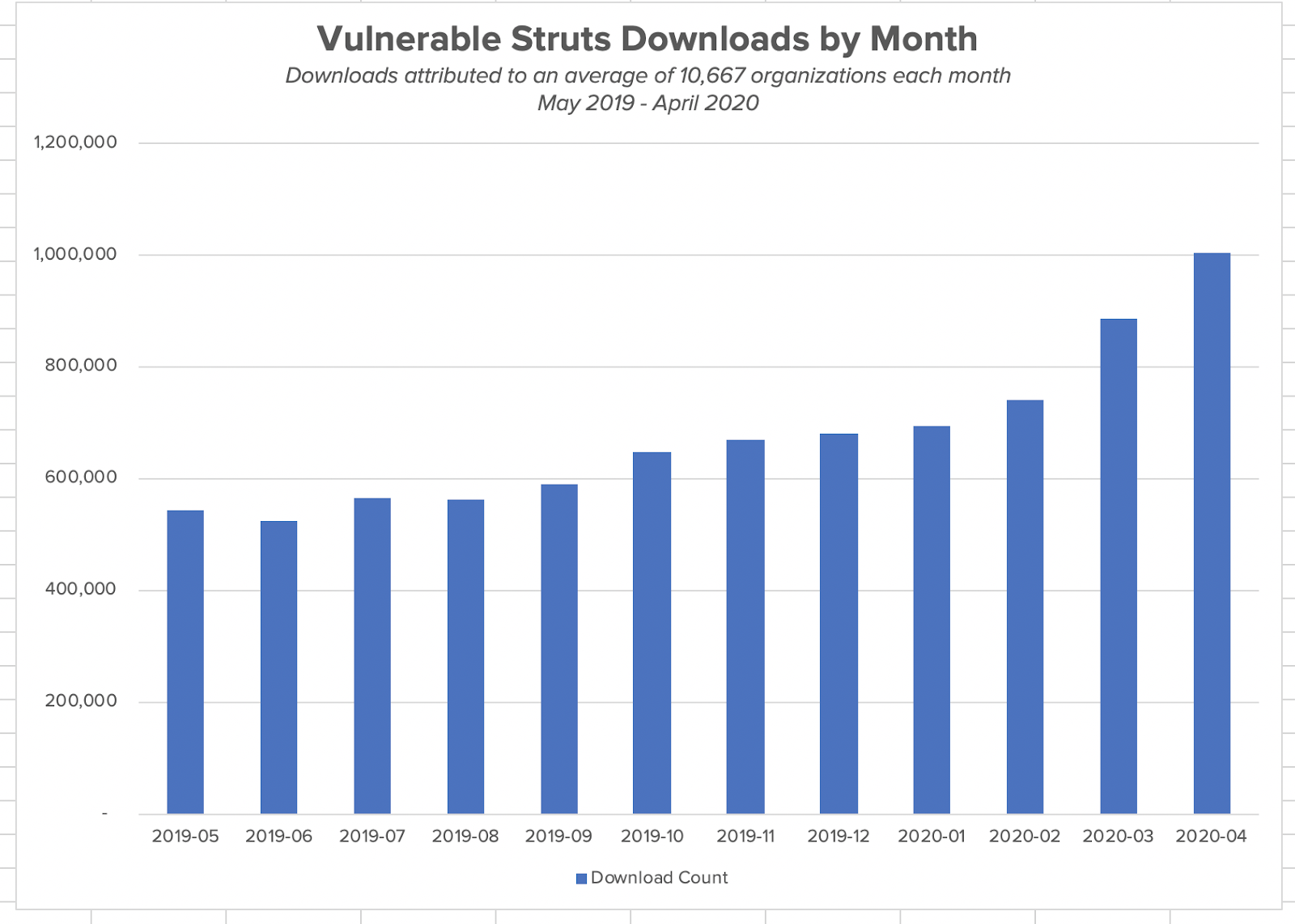
Vulnerable versions of Struts are still downloaded
Three years after the Equifax and other Struts related breaches, downloads of vulnerable Struts versions are still on the rise. A year ago, monthly vulnerable download counts were just under 600,000, but by the end of the year, downloads of vulnerable Struts versions topped one million. It's not just a few active development teams unwittingly downloading all of the vulnerable Struts versions. Our research of downloads from Maven Central show over 10,000 organizations downloading these components.
What could be causing this risky behavior?
It may be a result of organizations enjoying the benefits of using an established, well known, and free development framework. One of the benefits of using Apache Struts is the user community and the notifications you receive about security bugs. However, the downside is developers still have to manually keep track of these notifications. The ongoing use of the Struts component could reflect developers avoiding the difficulties that come along with updates and migrations.
How to benefit from free OSS while protecting software security
There is a better way to keep up with vulnerability notifications and repair components quickly. It is important for organizations to have the knowledge of, and monitor, all open source components they are using. After all, evidence suggests organizations will continue to download open source components, even those that are, or may become, vulnerable. So what should an organization do?
In short, it's critical to better understand what open source and third-party components are in your applications.
See if your application uses Struts, one of the top 10 vulnerabilities DHS CISA warns about, by using our free analysis in the Sonatype Vulnerability Scanner. Developers are encouraged to use DepShield, which directly integrates into GitHub repositories to evaluate open source software dependencies.
You can also configure your security policy based on the actual vulnerabilities found in components rather than manually managing the blacklist provided by your security team. Use policy controls to keep vulnerable versions of Struts out of your Nexus Repository. This way, when new vulnerabilities are discovered in components, even the ones on your security whitelist, Sonatype Lifecycle's Continuous Monitoring will report the violations quicker than your security team could update their whitelist.
And remember open source breaches, including those caused by exploited vulnerabilities in Apache Struts, like the 2017 Equifax breach, are entirely preventable when we shift security left.