Cybersecurity Status, 2018. Standing to the many available reports on cybercrime, 2018 has seen the "definitive" rise of cyber attacks. From Ransomware (see IOCTA2018) to Extended Supply Chain Threats (see Cyber Threatscape Report 2018), cybercrime is one of the most profitable activities that is going to cost the world an extra $6 trillion annually by 2021 (Cybersecurity Ventures).
Given that, our company has to assure competitive business to minimizing the risk of cyber attacks. We cannot ignore security and delay until something happens, because whatever the exploited threat will be, it is going to disrupt our business. Considering that the biggest successful cyber attacks in 2018 were against companies supposedly on top of security awareness (for instance, Yahoo, Adobe, Equifax, Sony), this should let us think about the problem with higher priority than ever.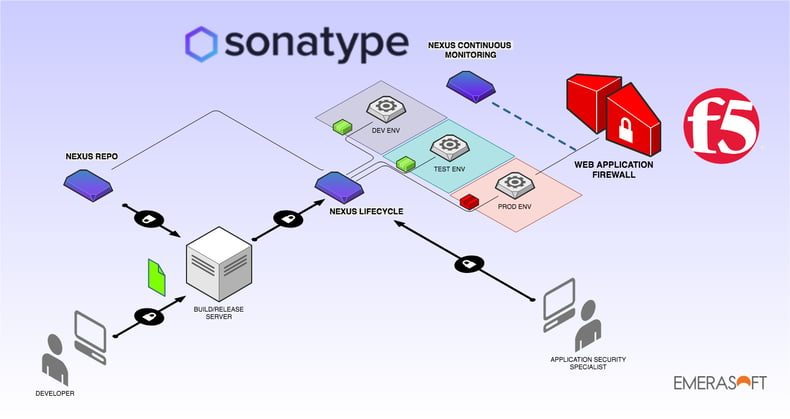
Our vision. Emerasoft promotes DevSecOps principles and practices. This means that we adhere to the DevSecOps manifesto leading our continuous research for improvement and keeping in mind that DevOps and Security are strongly interwoven. Increasing the number of software/service deploy is a step forward the time to market. Ignoring security is going to increase the risk of security weaknesses. In our mind, DevSecOps is the shorted way to keep development and operations safe from cyber threats. DevSecOps actually means sharing the responsibility of application security across all stages of the software lifecycle from design to production.
The challenge: proactive patching and fast reaction to zero-day vulnerabilities. The current scenario tells us that software is no longer built in-house, rather it is assembled starting from de-facto standard frameworks (see Hadoop, Kafka and most of the Apache Foundation projects), open-source libraries (see Spring). Furthermore, the stack our software relies on directly affects the security of our applications: application servers (Tomcat, Jetty, etc.) and containers are going to be part of the final solution we deliver and deploy to production.
On average, we deliver applications composed by up and over 90% of third-party components (see the 2018 State of the Software Supply Chain report), so that most of the focus must be on open-source components when dealing with application security.
At Emerasoft, we were wondering if there could exist a solution that lets us monitor vulnerabilities in production and immediately (automatically) react to those threats balancing against two key factors: risk of cyber attack and service availability.
Our solution. We got it done! A nice pipeline should work as follows:
- Detect the security weakness in production (monitoring)
- Mitigate the issue in production immediately (automation)
- Inform Dev and Sec teams to work it out (collaboration)
- Fix the issue and move on with a new deploy (lean)
Sonatype Nexus Lifecycle detects security vulnerabilities on open-source components released to production. It can be integrated throughout the entire software lifecycle at any stage (develop, integration, testing). As any new vulnerability appears in production, Nexus Continuous Monitoring is able to alert on time for an immediate reaction.
F5-Networks, the worldwide leader for network management solutions, includes the Advanced Web Application Firewall: a WAF of modern conception and highly customizable, plenty of security signatures and exposing rest APIs for a full orchestration and integration with any ecosystem. The F5 Networks Advanced WAF is able to protect against numerous critical scenarios (Injection, XSS, MitM, etc) by applying security policies (and consequently virtual patches) that depend on applications and context.
The combination of these two tools represents the solution to our problem.
Precision and automation. Sonatype Nexus Lifecycle can be easily be automated and it is fast. Most of all, it provides amazing precision to detect the vulnerabilities of third-party components. The software released to production gets continuously monitored. New vulnerabilities are automatically revealed by means of the Nexus Intelligence. Precision is the first step towards automation. Algorithms with low precision are not reliable. They don't allow for safe automation and lack of precision surely lead to two bad consequences:
- Exposing your company to high risk whenever your software includes a false negative (a vulnerable component that has not been detected)
- Disservice every time you are deploying a false positive (components that are not vulnerable but you consider them to be)
Orchestration and control. F5-Networks provides enterprise solutions for network management well-known at a global level. In addition, the Advanced WAF allows for full control and orchestration. The governance of policies can be tailored to address application security in a very careful way so that virtual patching applies only when strictly required.
Thus, given precision on vulnerability detection by Sonatype Nexus Lifecycle and easy orchestration through F5 Networks Advanced WAF, we can deliver software with less risk and more control avoiding to compromising business continuity.
--
**This article originally appeared on Medium.com and was written and translated into English by Ugo Ciracì, IT Advisor and Senior Solutions Architect at Emerasoft. Emerasoft is a Sonatype partner. **




