*Note: Join us live and online for the 2019 Nexus User Conference on June 12. Registration is free.
According to our 2019 DevSecOps Community survey of over 5,500 IT professionals, just 24% of companies with mature DevOps practices have integrated and automate security into their DevOps pipeline - that drops to 3% for those without a DevOps practice. While the change to integrating security into the development process is a big culture shift, the benefits in security compliance and eventual cost savings, far outweigh the initial friction.
But, alas, that is a case for different posts and presentations.
The point of today’s article is embedding security into the full lifecycle of containers. Containers are used by more and more DevOps organizations to secure their applications and provide more consistent server management. John Morello, the CTO of Twistlock, presented at the 2018 Nexus User Conference on the importance of securing containers across the full software lifecycle.
As John points out in his talk, containers have characteristics that make them more secure. They are minimal, so it is easier to understand what is inside. They are declarative, so it is better documented, by default, since you have to write the manifest to build it. Finally, it is predictable because it does the same thing from run to kill.
Of course, you still need to secure containers, and there are a few things you need to be aware of.
First, you have a lot more entities and there is a high rate of change. As John notes, with a multi-tier app, you might have a handful of VMs. To do the same thing properly with containers, you might have dozens of containers in order to break down your app into microservices.
Additionally, security is largely in the hands of the developers. Since a container is an immutable image that the developer sets up, the developer becomes responsible for updating the entire stack. Because of this, you may need new tooling since the ones you have are likely not container aware and, even if they are, they can’t see upstream in the Continuous Integration pipeline. Now with Nexus and tools such as Twistlock, you can see inside every build, including data about vulnerabilities, and your security team can set policies and force the build to fail before it ever leaves the environment.
So, how do you effectively secure cloud-native apps? John notes that the only way is through increased knowledge, responsibility, and enforcement, and you get that by moving it up in the lifecycle (shifting left) rather than in production. This isn’t a technical shift, but a people and process shift. The tools have been around for years - you have to build it into the the day-to-day, into what everyone does naturally.
Docker, the prominent container company, has a motto of, “build, ship, run.” The below illustrates where responsibilities lie after shifting container security left.
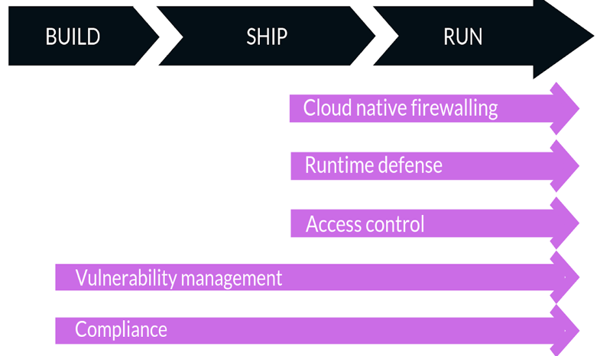
Looking at the first of the two areas shifting left, vulnerability management with containers, When you shift security left, you have to ease the friction for vulnerability management. If a developer has to leave the development-build environment to scan for vulnerabilities, it adds friction This friction means some people ignore it. However, when it is a natural part of the process, compliance increases.
Vulnerability management also means having automated, policy-driven blocking of builds and deployments when vulnerabilities are found. When this is done during the build, it is the lowest cost and effort to resolve it and it doesn’t expose the production environment.
With automated, policy-driven builds and deployments, compliance also increases because human error and emotion are minimized. Tools, such as Nexus, are able to enforce whitelist rules and manage threats automatically, and polices aren’t ignored for convenience or inadvertently misapplied because of human error or misunderstanding. This all gives auditors peace-of-mind because they know scans are happening and policies are being enforced consistently and with a digital paper trail.
John's full talk did an excellent job of laying out how to further secure containers, which are inherently more secure than traditional environments, with culture, policies, and tools. The tools, such as Nexus products and Twistlock, enable and enforce the culture and policies.
If you are interested in learning more about all of the Nexus products, check out the platform here.
And, keep an eye out for more session recaps from the 2018 Nexus User Conference - we'll be sharing many of them leading up to this year's conference on June 12.







