Nate Silver’s 2012 book “The Signal and The Noise” crisply explains the inevitability of earthquakes and the accuracy with which their frequencies and magnitudes can be predicted. The smoothness of the plot relating these two variables – a visualization of the Gutenberg-Richter law at work – is striking.
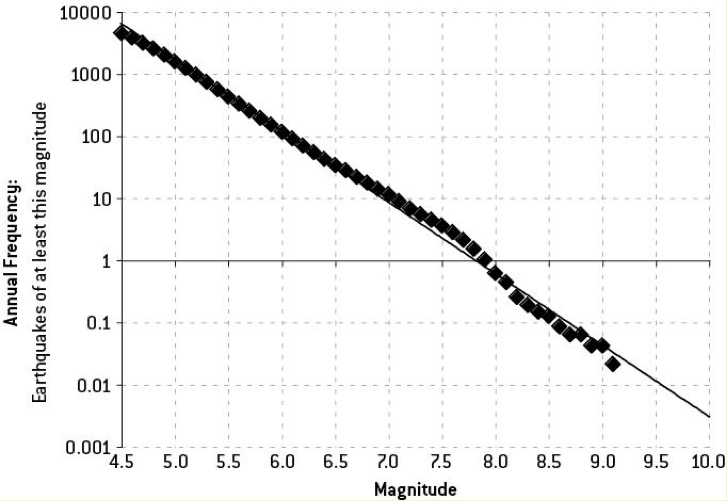
Earthquakes follow a power-law distribution. In this particular case, for a roughly one point increase in magnitude, the frequency of occurrence drops by a factor of 10 while the energy released increases 32-fold. This exponential relationship leads to a very small number of events causing a disproportionately large degree of total impact, Fukushima, Haiti and Jakarta being examples. This is a characteristic of application security breaches as well, with Equifax being the highest impact breach in history. A lot of low impact events – most you never even hear about – punctuated by the rare, catastrophe.
Despite being able to accurately predict the likelihood of a certain magnitude earthquake in different geographies, we still cannot determine when or where a particular event might occur. Given enough time, high magnitude earthquakes are an inevitability no matter where you might live.
Similarly, it is impossible to determine when the next major open source vulnerability is going to be announced and how and where it might be exploited. However, like earthquakes, such events are inevitable.
Open Source Exploits and Power-Law Distributions
As the complexity of software continues to increase, so does the difficulty in keeping it secure. More recently, this challenge has grown even faster with the explosion in the use of open source software and the many hidden complexities that come with it. The ground beneath applications has slowly shifted over the last 20 years as the technology stacks have converged on common, open platforms. If left unchecked, the combination of bad actors, growing software complexity and suboptimal software supply chain hygiene – poor use of open source – makes successful attacks not only an inevitability but increasingly likely and with much greater impact. These conditions approximate a power-law distribution relating open source exploits and their corresponding impact.
Because of the understood inevitability of earthquakes, building codes are used to significantly reduce the resulting impact of major quakes and in many cases prevent catastrophe. The Haitian earthquake of 2010 resulted in fatalities numbering in the hundreds of thousands with over a million people left homeless in the aftermath. This event impacted the neighboring Dominican Republic – occupying the same island as Haiti – dramatically less due primarily to construction quality.
Similar “building codes” can be used in the development of software. In this case, the requirements demand a high-degree of software supply chain hygiene, which can be achieved by leveraging automation and other tooling to effectively manage the use of open source software. Developers become empowered to make better decisions in the software components they choose to use, with their actions thoughtfully guided following the disclosure of high-impact software vulnerabilities. Bad actors will invariably continue to prey on the weak and in this case the victims will be those with poor open source hygiene – said differently, inadequate building codes.
When new widely used open source projects announce critical vulnerabilities, probes for weakness by bad actors are now manifesting within a day or two. This was the case with the Struts vulnerability that led to the compromise of Equifax’s store of personal data. This timeframe will only compress as techniques for reverse engineering fixes and turning those into working exploits improve. The race is on. For those affected, the mean-time-to-remediation following these announcements must be on the order of hours to minimize exposure to attack. At the scale that many organizations are developing, automation then becomes a necessity.
Be Prepared
The discovery of the next high-impact vulnerability is inevitable. We’re just not sure exactly where or when. Attackers are going to take advantage wherever they can and more and more quickly. Are your own software building codes sufficient? Do your development, security and ops teams have the tooling available to respond immediately and decisively to the next major open source vulnerability?
Start preparing for the next major open source quake now. More information can be found in this prior post.