The United States Senate is making moves to protect consumer interests, data, and privacy with regard to the Internet of Things (IoT). Today, U.S. Senator’s Mark R. Warner (D-VA) and Cory Gardner (R-CO), co-chairs of the Senate Cybersecurity Caucus, along with Sens. Ron Wyden (D-WA) and Steve Daines (R-MT) introduced bipartisan legislation called the Internet of Things Cybersecurity Improvement Act of 2017.
Addressing IoT Market Failures
According to a fact sheet released by the Senators, “While ‘Internet of Things’ (IoT) devices and the data they transmit present enormous benefits to consumers, the relative insecurity of many devices presents enormous challenges. This legislation is aimed at addressing the market failure by establishing minimum security requirements for federal procurements of connected devices.”
The proposed legislation drives home a new reality for IoT device manufacturers: while development organizations currently decide to invest in cybersecurity using a cost-benefit assessment, they are ultimately liable for the security of their data and systems.
The U.S. Senate’s Proposal
The proposed legislation requires vendor commitments:
- To ensure devices don’t contain known security vulnerabilities when shipped
- To ensure proper disclosure of new security vulnerabilities discovered within their devices
- To prepare remediation plans for any IoT device where known vulnerabilities have been discovered
The Internet of Things Cybersecurity Improvement Act of 2017 is tied directly to Federal government procurement of such devices but Sonatype predicts they will likely extend into private sector guidelines moving forward. While the legislation is clearly aimed at consumer protections and privacy, it also focuses on quality, safety and regulatory standards applied to every other major manufacturing industry (thou shall not ship products with known defects). While commonsensical in other manufacturing industries, Congress is now directing development organizations to apply similar quality standards for the software it develops and ships.
Certify IoT Devices are Free From Known Security Vulnerabilities
The legislation specifically calls for vendors selling IoT devices “to provide written certification that the device does not contain, at the time of submitting the proposal, any hardware, software, or firmware component with any known security vulnerabilities or defects.”
Notification When New IoT Vulnerabilities Are Discovered
Following the purchase of any IoT devices, the government wants the seller “providing the Internet-connected device software or firmware component to notify the purchasing agency of any known security vulnerabilities or defects subsequently disclosed to the vendor by a security researcher or of which the vendor otherwise becomes aware for the duration of the contract”.
Ensure Remediation Paths are Available
Protections go even further in the post-sale period, calling for clear remediation paths. The proposed legislation would require “any future security vulnerability or defect in any part of the software or firmware [of the IoT device] to be patched in order to fix or re-move a vulnerability or defect in the software or firmware component in a properly authenticated and secure manner.”
20 Vulnerabilities Per Application
Two weeks ago, Sonatype released it’s 2017 State of the Software Supply Chain report that shares empirical evidence of the number of known software vulnerabilities that ship in applications -- IoT or otherwise. The report found that development organizations building software with unmanaged software supply chains release applications with an average of 20 known security vulnerabilities, 6 of which had a Common Vulnerability Scoring System (CVSS) rating between 7 and 10.
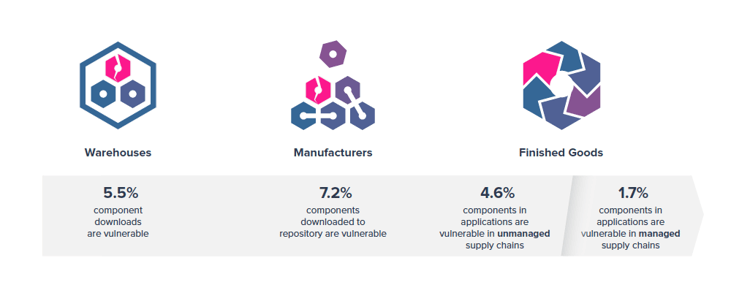
Sonatype’s State of the Software Supply Chain report also reveals how national governments, federal agencies and industry associations are taking action to help organizations improve open source hygiene and application security practices. In the past year, new guidelines have been introduced from the White House, Federal Trade Commission, Department of Homeland Security, Department of Health and Human Services, and the Department of Commerce to improve the quality, safety and security of software supply chains -- related to IoT devices and any other application development efforts.
The Tide Has Turned
While the proposed legislation is still open for debate, there is clear evidence that those once ignorant or turning a blind-eye to such cybersecurity issues are now paying attention -- and they are preparing to make significant changes.
The full text of the proposed legislation for the Internet of Things Cybersecurity Improvement Act of 2017 can be found here.







