For our October Nexus Intelligence Insight we will return to a very popular component that has been both a blessing and a curse to developers around the world. We’ll cover a fundamental change to a default setting and how that change in ‘type’ may impact the security of your next open source project.
Before you read this post, you may want to review the ongoing issue with jackson-databind and Sonatype’s remediation guidance as a result.
Name of Vulnerability: Sonatype-2017-0312
Associated CVEs: CVE-2017-7525, CVE-2017-15095, CVE-2017-17485, CVE-2018-5968, CVE-2018-7489, CVE-2018-11307, CVE-2018-12022, CVE-2018-12023, CVE-2018-14718, CVE-2018-14719, CVE-2018-14720, CVE-2018-14721, CVE-2019-12086, CVE-2019-12384, CVE-2019-12814, CVE-2019-14379, CVE-2019-14439, CVE-2019-14540, sonatype-2019-0371, and CVE-2019-16335.
Type of Vulnerability: Deserialization leading to Remote Code Execution (RCE)
Component Name: `com.fasterxml.jackson.core:jackson-databind`
Versions Affected: ( , 2.10.0)
Criticality/CVSS Metrics: 8.5 CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:H/A:H
Vulnerability Description:
For those who’d prefer a summary, the attack vector for this vulnerable component lies in the deserialization of untrusted data from improperly validated objects being provided as an input to an application. Should an attacker be able to influence the serialized object data and inject malicious code or logic into it, that code could wreak havoc in the application environment upon deserialization - from seemingly benign crashes to remote code execution to a total system compromise.
As mentioned in the previous post, Databind addressed the multiple deserialization vulnerabilities by using a “blacklist” approach, meaning the objects of restricted subtypes were not to be processed by the component for deserialization.
Blacklist approach:
The String-Set "s" maintains a list of "nasty classes" which are known to cause security issues and are restricted from being deserialized.
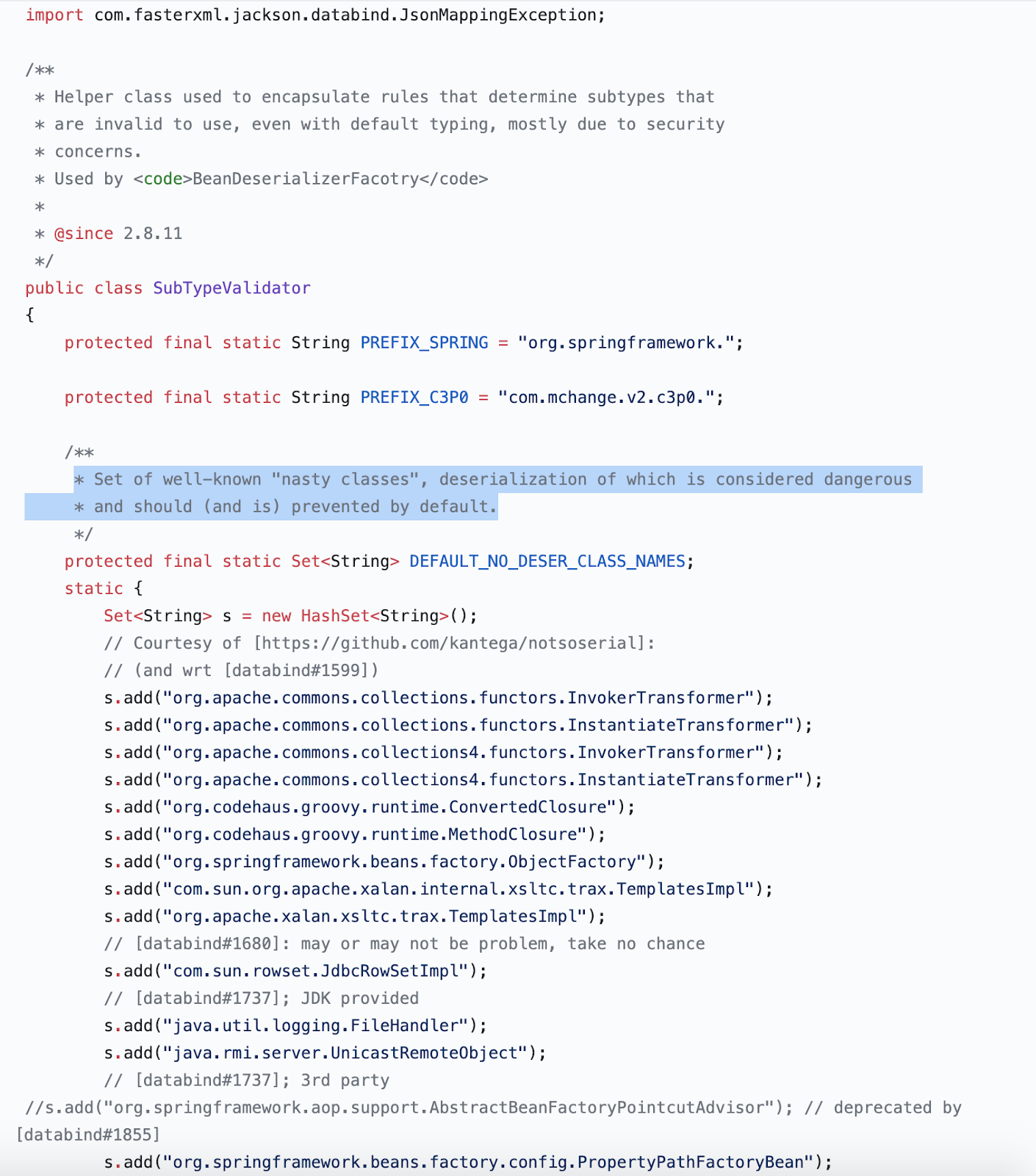
Incomplete fix which further added “more classes” to the same blacklist: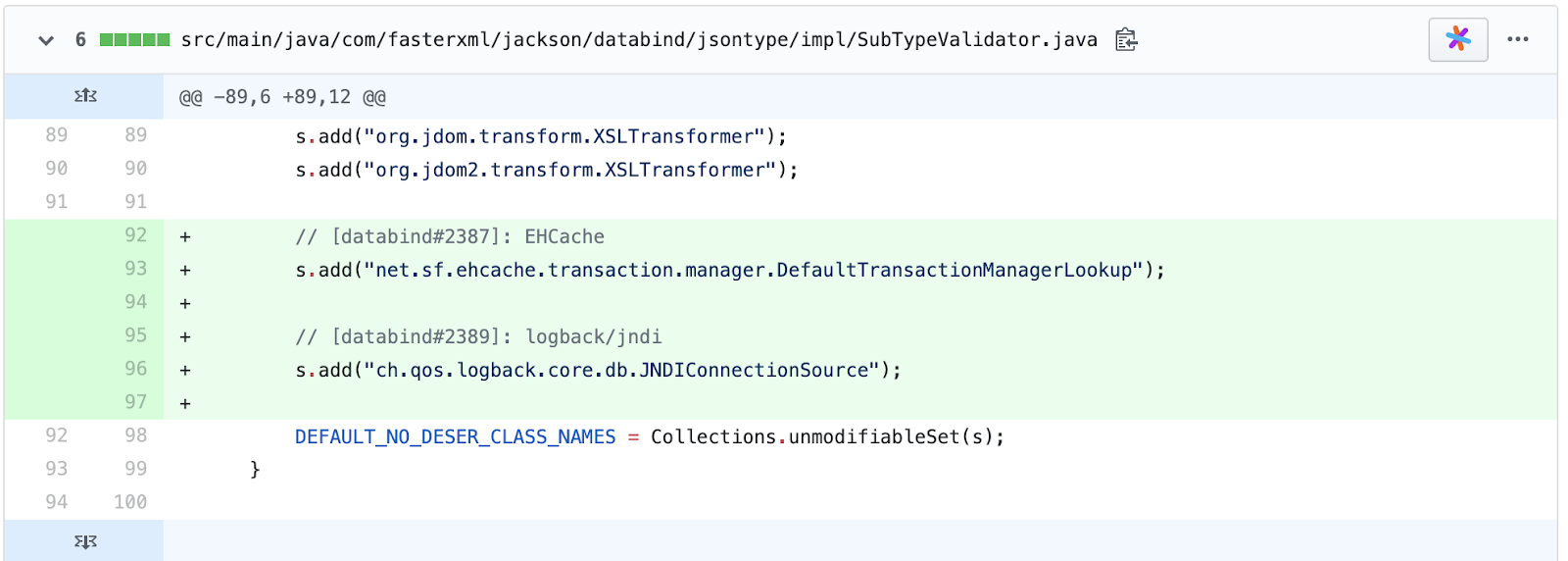
Consequently, the Sonatype data research team concluded all such “fixes” as partial or incomplete.
To reduce the scan noise for our customers, we continuously updated and revised the jackson-databind version numbers impacted by the “blacklist” fix, their associated CVE numbers (around 23 separate CVEs) and assigned a proprietary vulnerability number, sonatype-2017-0312 to cover new versions of Databind subject to the “blacklist” fix, but not already covered by a CVE, until a permanent fix was released.
Recently, the project released version 2.10.0 which is a sufficient, holistic fix for the deserialization vulnerability in jackson-databind. This most recent version release introduces a “whitelist” approach to the relief of everyone involved.
Proper fix - whitelist approach:
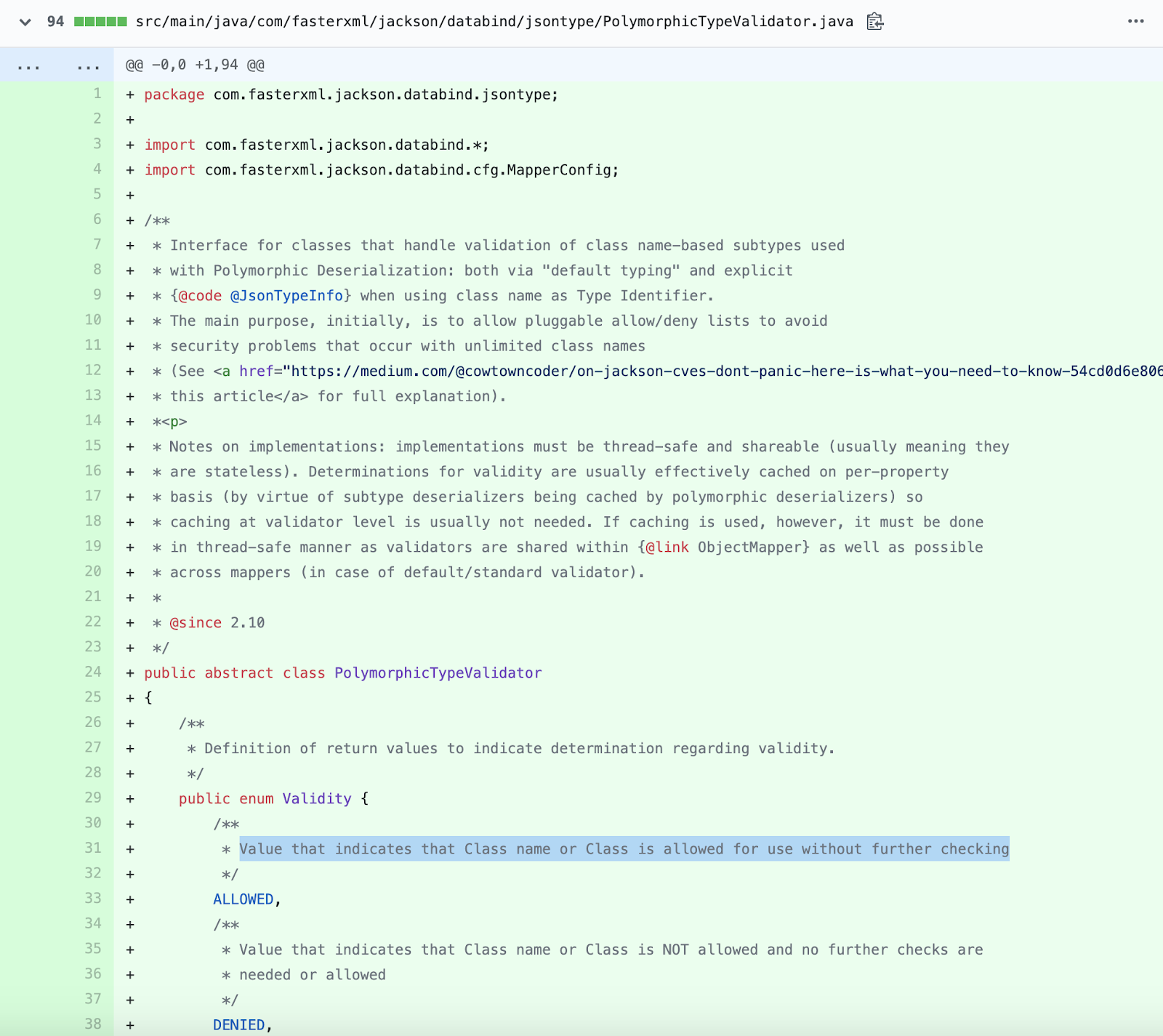
As the official release notes highlight, version 2.10.0 of the component now uses “Safe Default Typing” using the `activateDefaultTyping()` method as opposed to the deprecated `enableDefaultTyping()` method. This drastic improvement is especially significant in terms of basic, default security and remediation time when another component is blacklisted.
The new method introduced in the fix now requires the developer to explicitly specify what subtypes of classes are allowed to be deserialized, via `PolymorphicTypeValidator’. This means objects belonging to types other than those specified in the list would be safely ignored and untrusted deserialization no longer remains a viable possibility.
This “whitelist” approach mitigates the risk of deserialization of untrusted data which gave rise to sonatype-2017-0312 in the first place, due to incomplete fixes having been applied to multiple vulnerabilities by the project: CVE-2017-7525, CVE-2017-15095, CVE-2017-17485, CVE-2018-5968, CVE-2018-7489, CVE-2018-11307, CVE-2018-12022, CVE-2018-12023, CVE-2018-14718, CVE-2018-14719, CVE-2018-14720, CVE-2018-14721, CVE-2019-12086, CVE-2019-12384, CVE-2019-12814, CVE-2019-14379, CVE-2019-14439, CVE-2019-14540, sonatype-2019-0371, and CVE-2019-16335.
Recommendation:
As of today, we recommend upgrading to at least version 2.10.0 of `com.fasterxml.jackson.core:jackson-databind`, as present in Maven Central, and changing any usages of `enableDefaultTyping()` to `activateDefaultTyping()` in order to mitigate this vulnerability.
For more information on jackson-databind:
- Nexus Intelligence Insights - CVE-2018-14721 - jackson-databind remote code execution
- Jackson 2.10 features (esp. “Safe Default Typing” to vanquish stream of CVE patches!)
- On Jackson CVEs: Don't Panic — Here's What You Need to Know
- Jackson Release 2.10 on GitHub
DevOps-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers. Customers of Sonatype Nexus were notified of sonatype-2017-0312 within hours of the project being notified. Their development teams automatically received instructions on how to remediate the risk.
If you're not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype's free Nexus Vulnerability Scanner to quickly find out.
If you are a Sonatype customer and have additional questions about this component, its presence in a scan or a policy violation, please contact your Customer Success representative
Interested in learning about other vulnerabilities impacting the open source ecosystem? Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one.







