As a developer, you know the importance of building a robust application. With cyberattacks increasing every day, you should make sure your application is safe from the attacks and isn’t vulnerable.
To assess your application for security and to help you find vulnerabilities in your application so you can fix them, our open source vulnerability scanner would be of great help!
So, in this post, I’ll be telling you what this tool is and how to use it.
What Is the Sonatype Vulnerability Scanner?
Sonatype Vulnerability Scanner is a tool that scans your application for vulnerabilities and gives you a report on its analysis.
As claimed by Sonatype, the average application consists of around 100+ open-source components and around 20+ vulnerabilities.
Obviously, with so many potential weak points in your application, it’s not deployment ready. And ignoring the security of your application might affect the business.
Once you’ve developed your application and made sure that it works as expected, you should concentrate on how secure the application is.
Now, let me show you how you can use Sonatype Vulnerability Scanner to scan your application.
Setting Up Sonatype Vulnerability Scanner
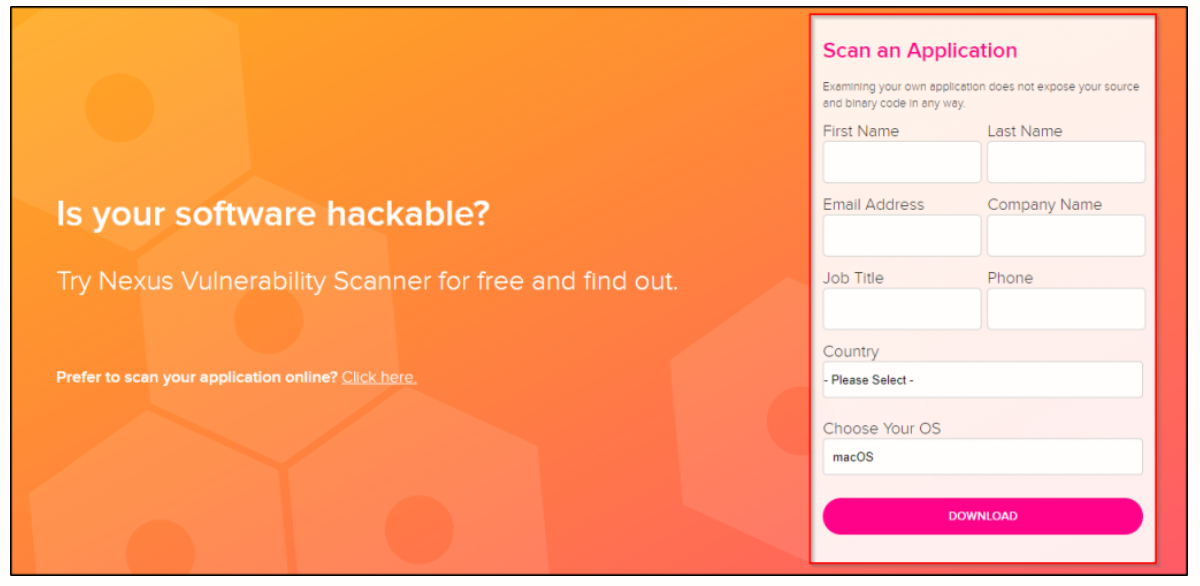
The first step is to download the tool. You can find it here. To access the tool, you have to fill out a simple form and then click on the download button.
The application you have to download is small in size so it won’t take much time.
Once the download is complete, extract the contents from the downloaded file. That’s it! You’ve set up the scanner!
Using Sonatype Vulnerability Scanner
Now, to start the application, get into the application folder and execute the application-check file.
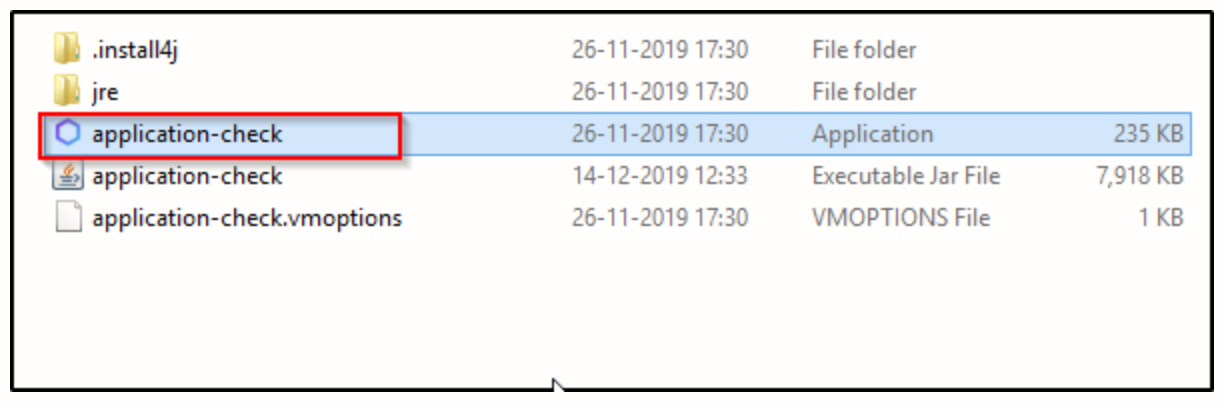
After the application starts, you’ll see the application window. It will ask you to select the application in which you want to find vulnerabilities.
Sonatype Sample Applications
If you just want to check how this tool works and don’t want to run it on your application, or if you don’t have your application ready, that’s fine!
Sonatype gives you sample applications that you can run this tool on, too. After you download the tool, you’ll be redirected to a page with a list of applications.
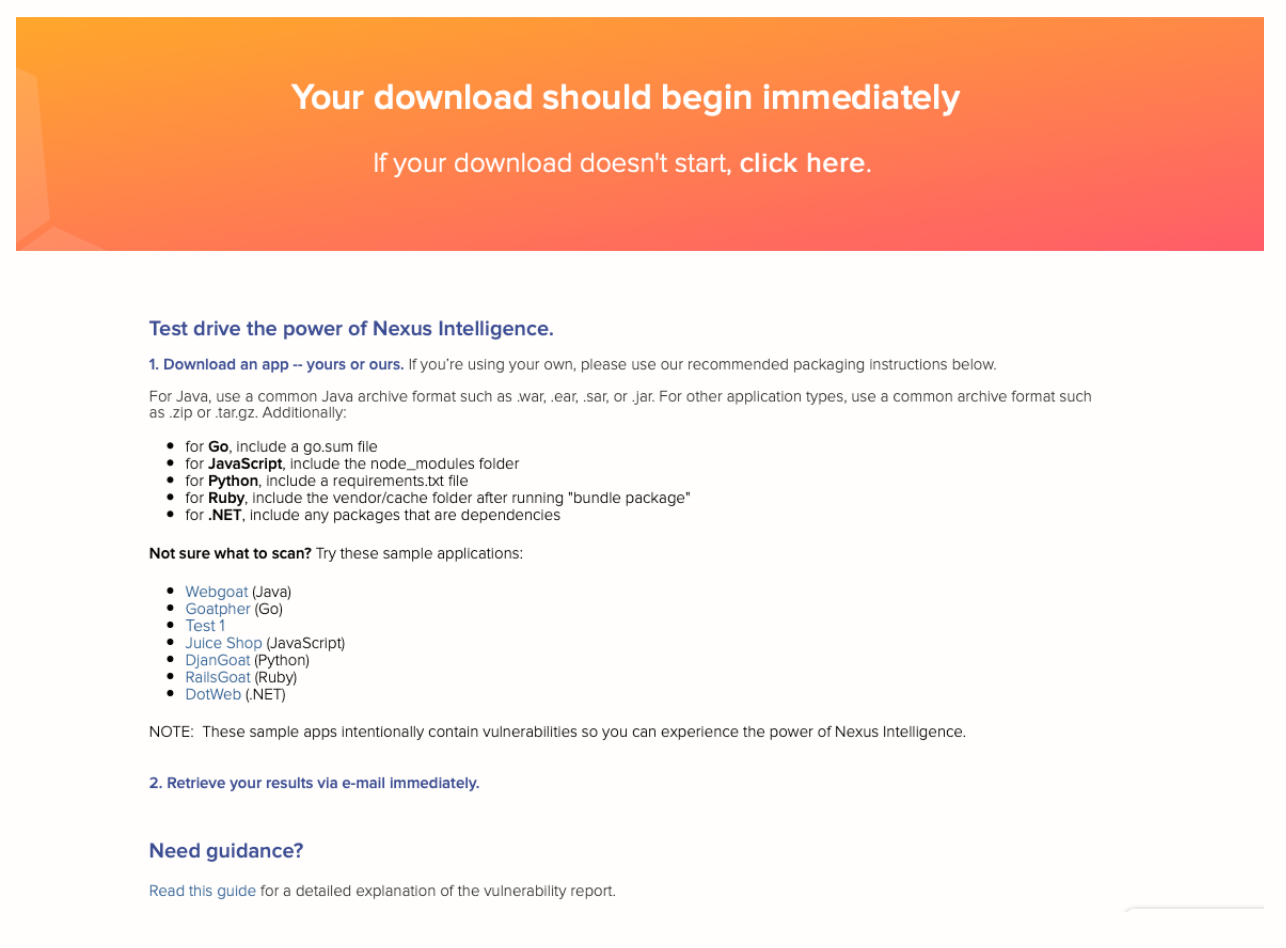
Let’s walk through how this looks. I see several applications listed.
I know what WebGoat is. It’s a web application that’s designed to be vulnerable on purpose. But I’m curious about the Test1 application so I’m going to use that for this demo.
So, I’ve downloaded the sample application. You can do this by just clicking on the application name.
Running the Scan
Now, let’s come back to our scanner. I’m going to select the sample applications I’ve downloaded. You can select a name for your report and also make it password protected. I like this feature. Let me tell you why.
Suppose you build an application and run the scanner. You’ve got a list of vulnerabilities that exist in the application. You wouldn’t want this information to get into the hands of any unauthorized person, especially a hacker.
If a hacker did have access to this information, it would just make things easy for them. Even though you would fix the vulnerabilities, the hacker would know which vulnerability was fixed, and that reveals a lot of information about your application. Now, even if a hacker somehow gets access to your email address, they still wouldn’t be able to look at the report because it is password protected.
After you’ve selected the application and filled in other details, click on the START SCAN button to start scanning. Give it some time, and once the scan is complete, the report will be sent to your email address.
Scan Report
To view the scan results, you’ll have to click on the link sent to your email address. You’ll be asked to enter your username and password, and on correct entry, you’ll be shown the report.
The result page has four main categories:
- Summary
- Policy violations
- Security issues
- License analysis
Let me tell you about each of these.
Summary
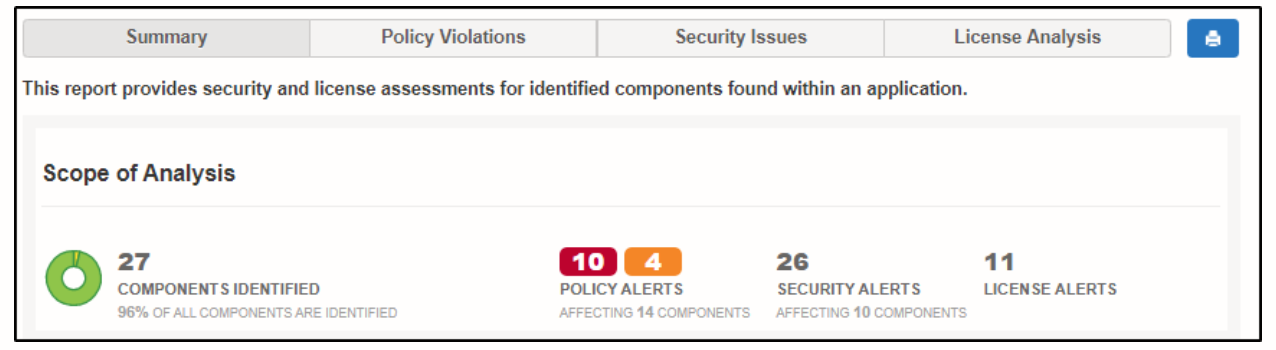
Here, you’ll see the summary of the results. Obviously, that’s self-explanatory. The summary is helpful when you want to have a quick peek of your scan’s result.
Under the summary tab, you’ll see the scope of analysis, the number of alerts under different categories, and the number of vulnerabilities found under different levels: moderate, severe, or critical. This gives you an idea of how serious the effect of a particular problem can be.
Policy Violations
Under this tab, you’ll see the details about all the alerts related to policy violations. A policy violation is doing something against the standards of the organization.
The first sub-tab shows you which component contains the problem. This helps in debugging. It wouldn’t make a big difference in a small application. However, in a large-scale application, this information will save you time in searching for the component.
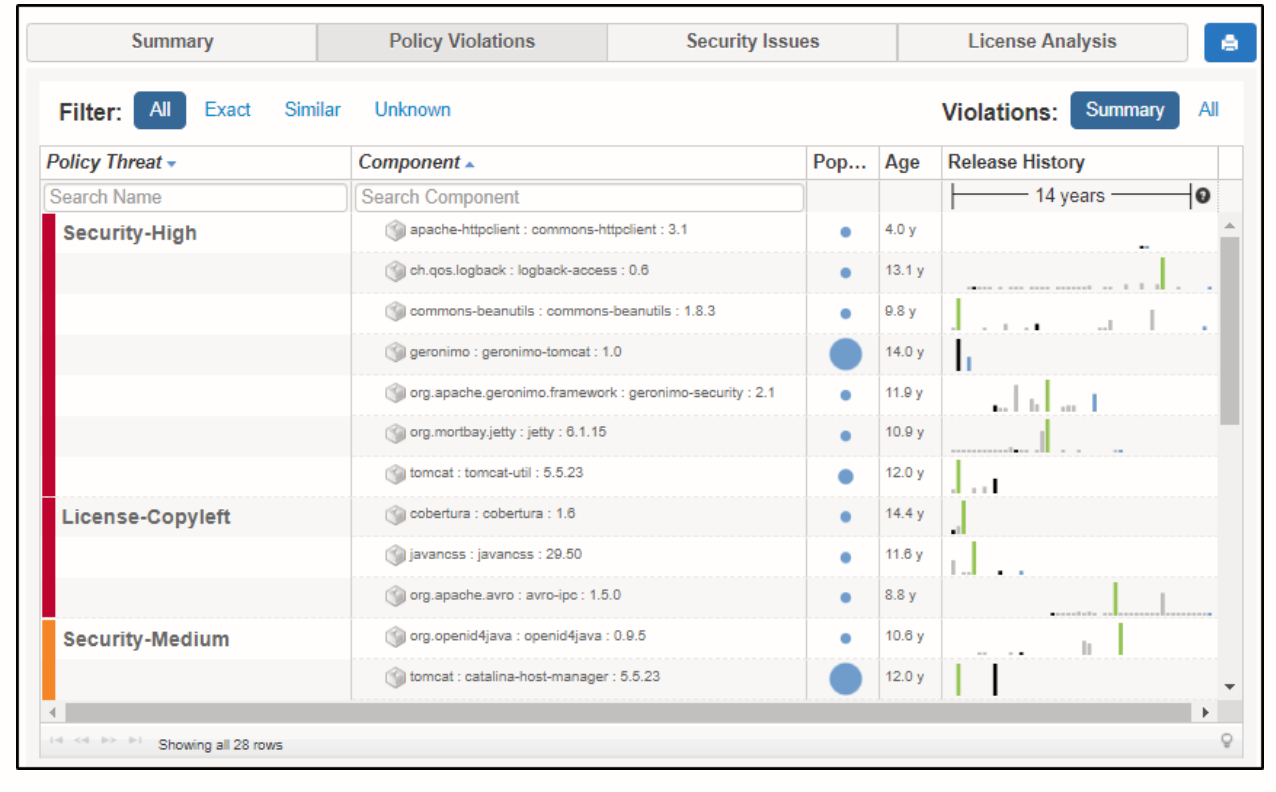
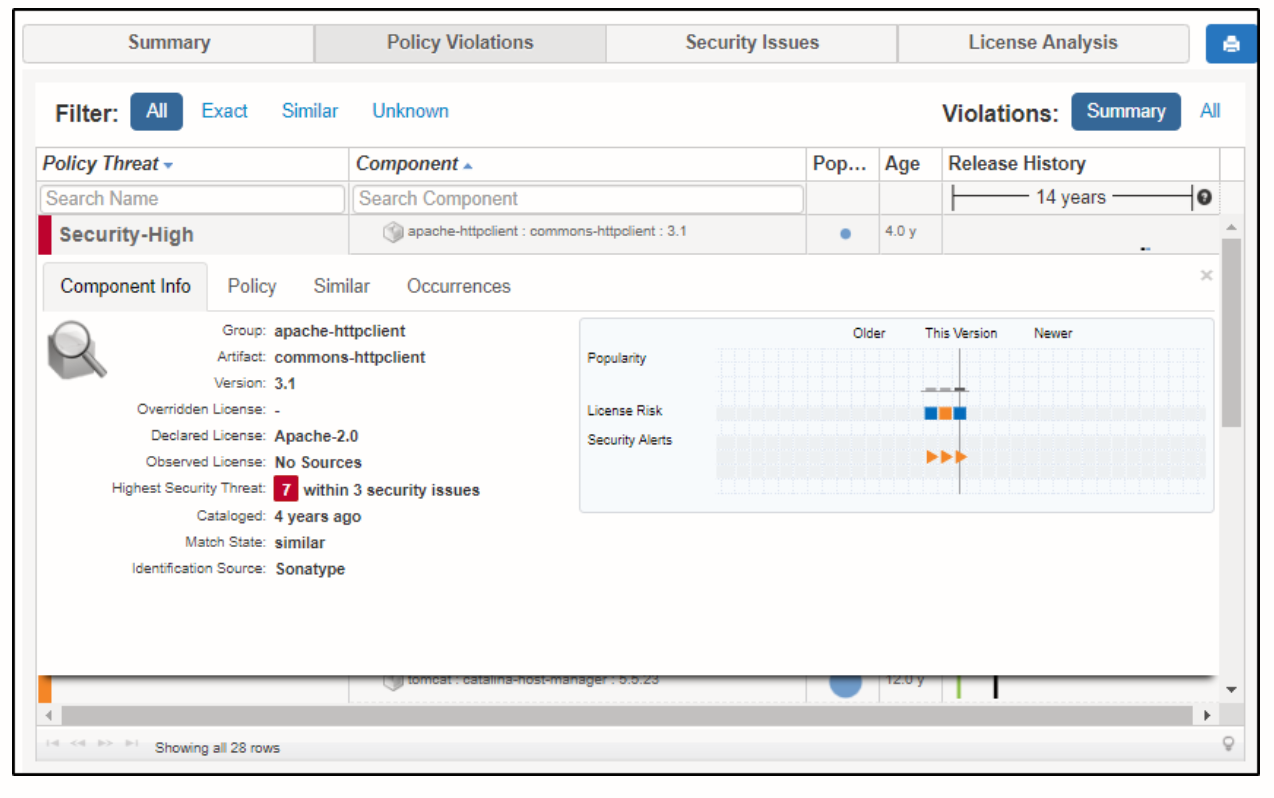 The next sub-tab will show you the policy details. In this case, there are three security issues. You can also see the CVE (Common Vulnerabilities and Exposures) number which would help you learn more about the vulnerability.
The next sub-tab will show you the policy details. In this case, there are three security issues. You can also see the CVE (Common Vulnerabilities and Exposures) number which would help you learn more about the vulnerability.
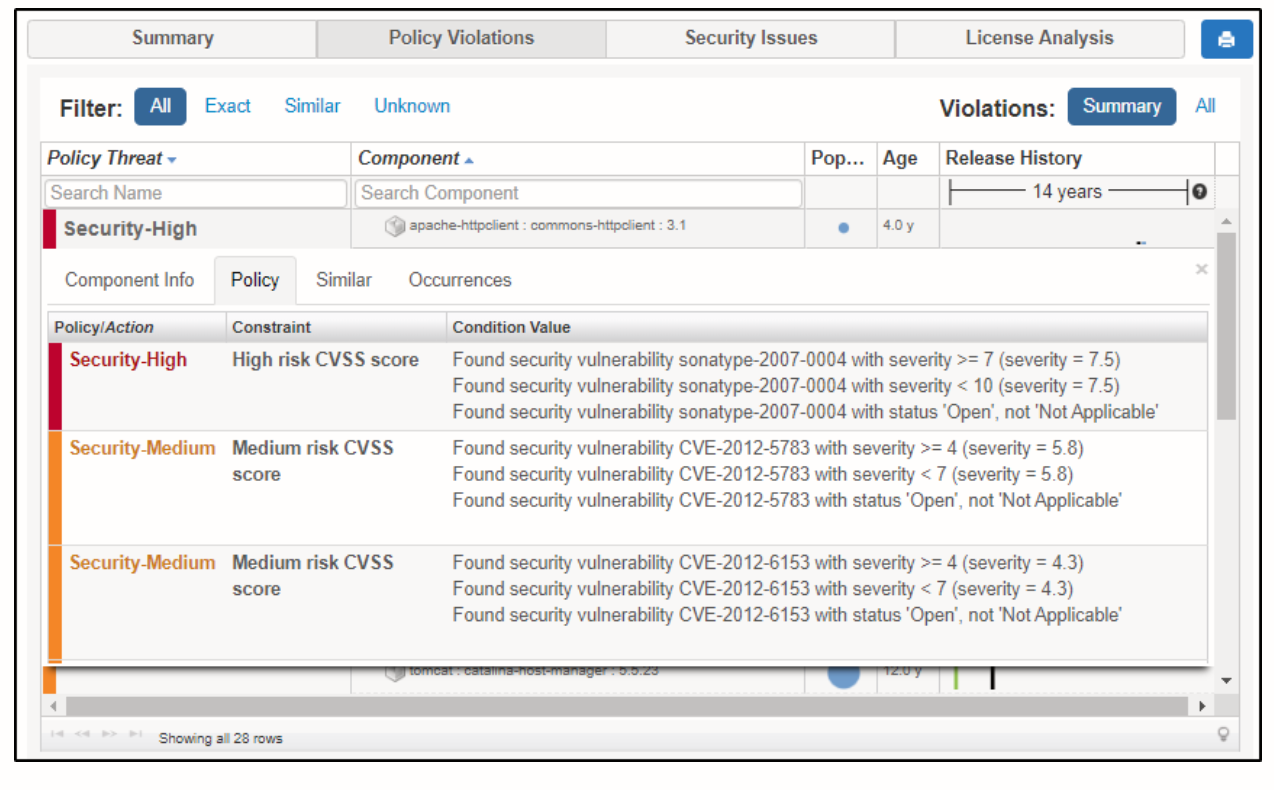 This feature of Sonatype Vulnerability Scanner is one of my favorites. I’ve used a lot of vulnerability scanners, and most of them just look for vulnerabilities and ignore the policies. This feature will really help you, as a developer, solve policy issues.
This feature of Sonatype Vulnerability Scanner is one of my favorites. I’ve used a lot of vulnerability scanners, and most of them just look for vulnerabilities and ignore the policies. This feature will really help you, as a developer, solve policy issues.
Security Issues
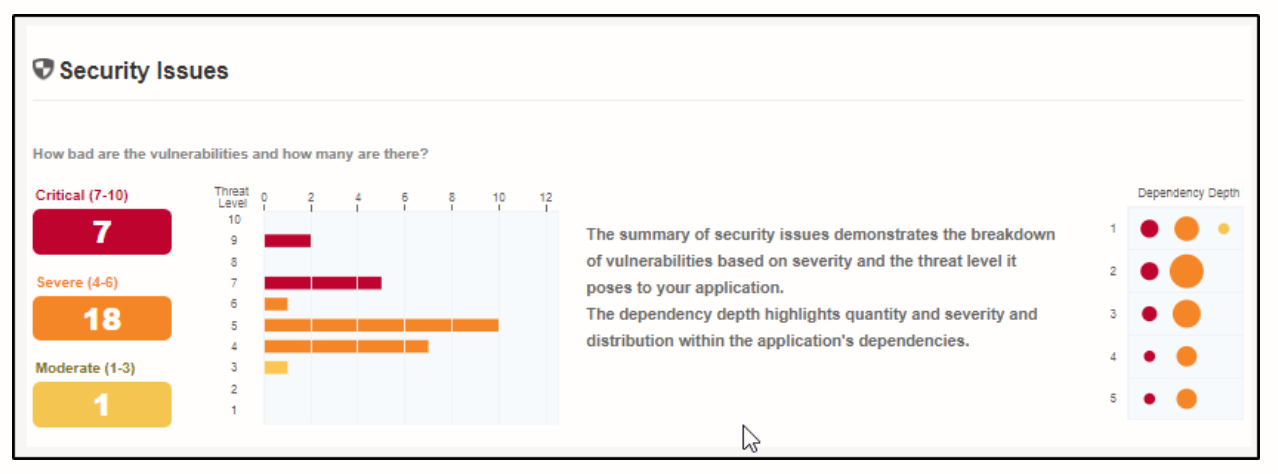
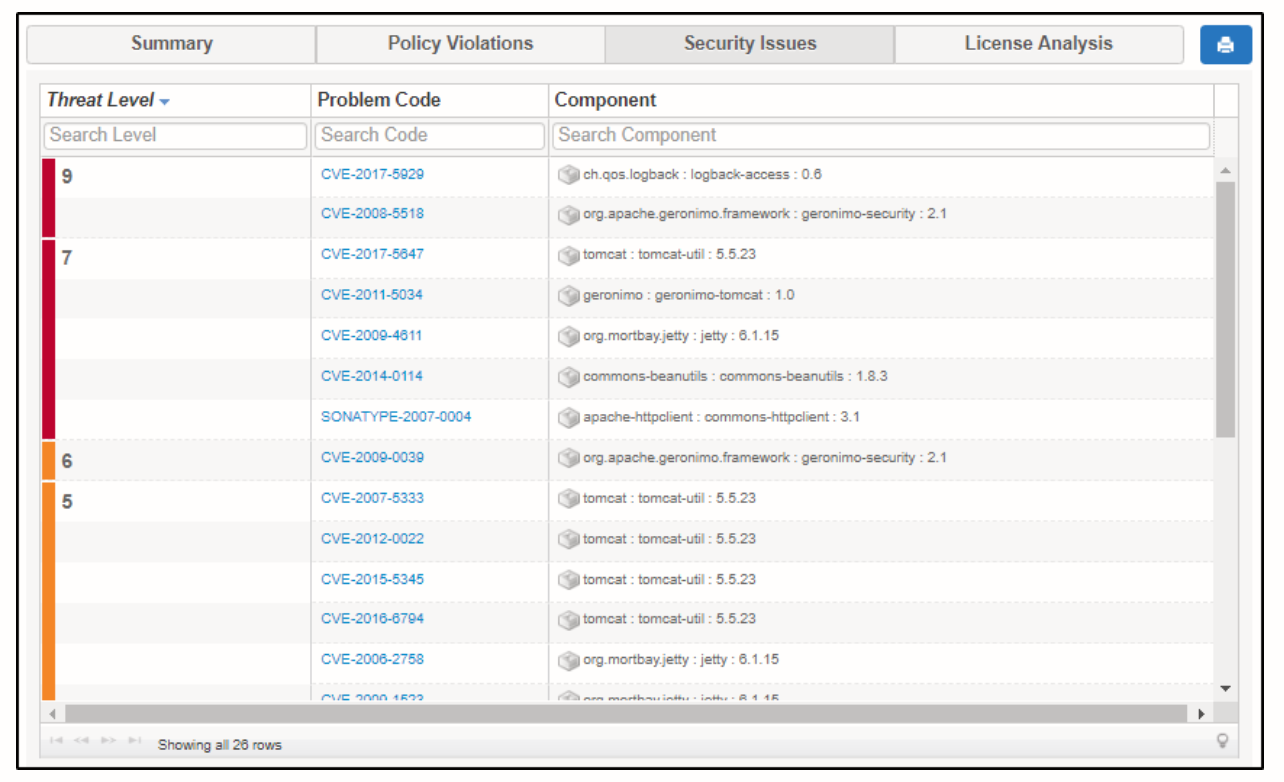
This is one of the most important parts of the report and the reason why vulnerability scanners are used. The security issues tab lists out the number of issues found, their threat level, the component in which the threat was found, and the vulnerability.
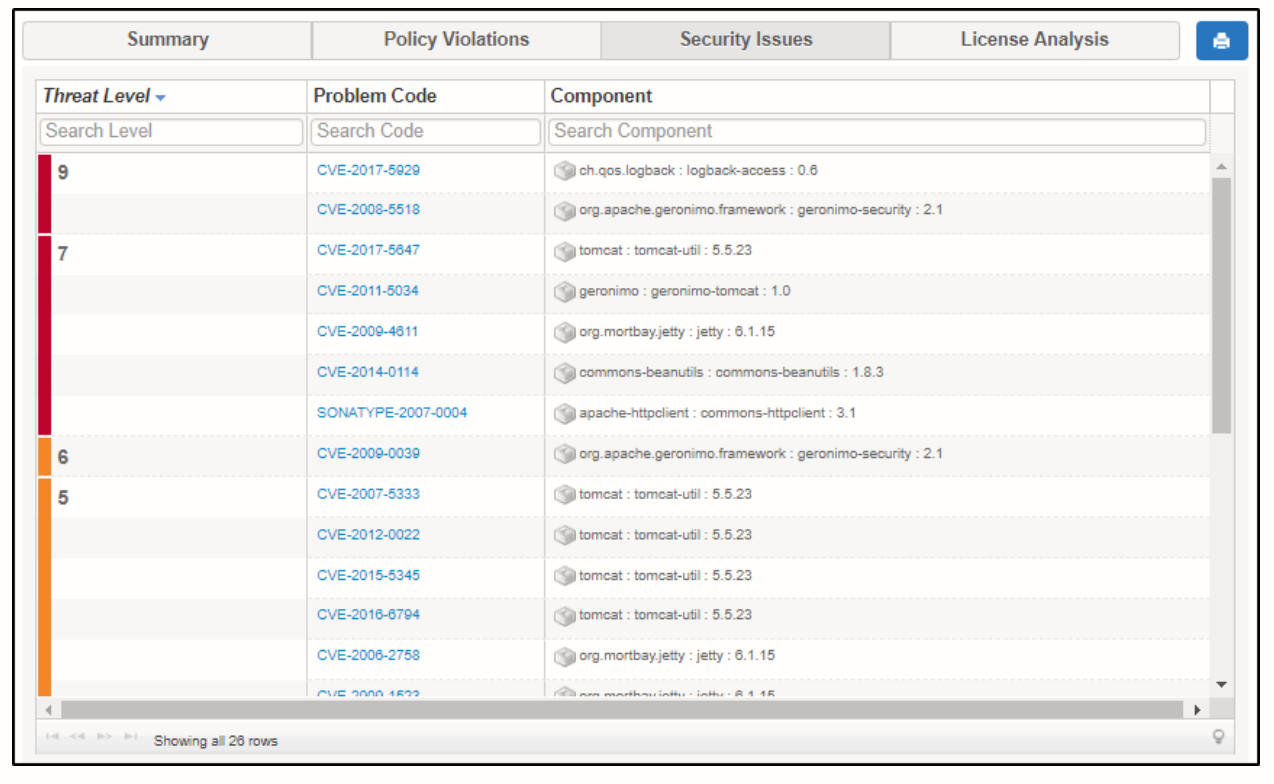
One of the things under this tab that I found very informative is the problem code. The problem code is a unique identifier to that particular vulnerability. You’ll find this helpful when you want to understand more about that vulnerability. This also helps you understand how that particular vulnerability can be exploited.
If you want to know more about problem codes and have a look at the vulnerability and exploit database, check this link.
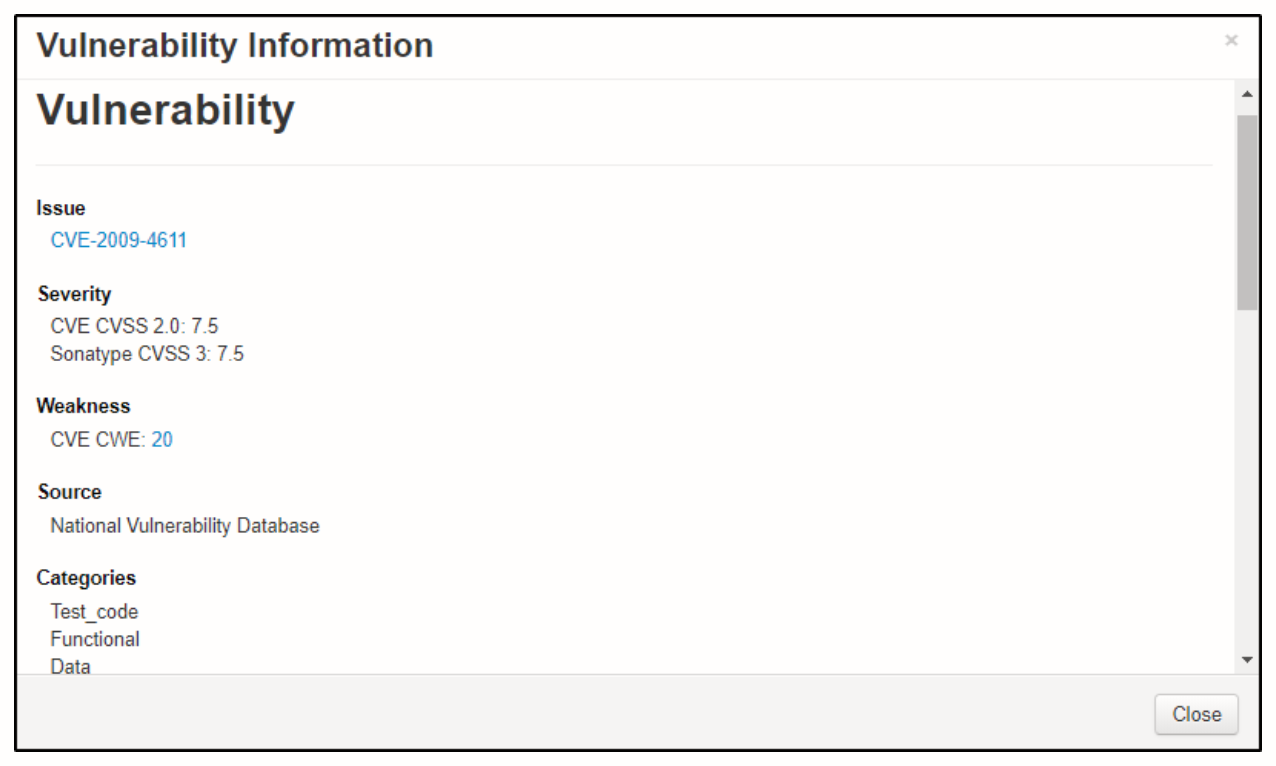
To know more about the security issues found by the scanner, you can click on the problem code and it will show you a pop-up with more details.
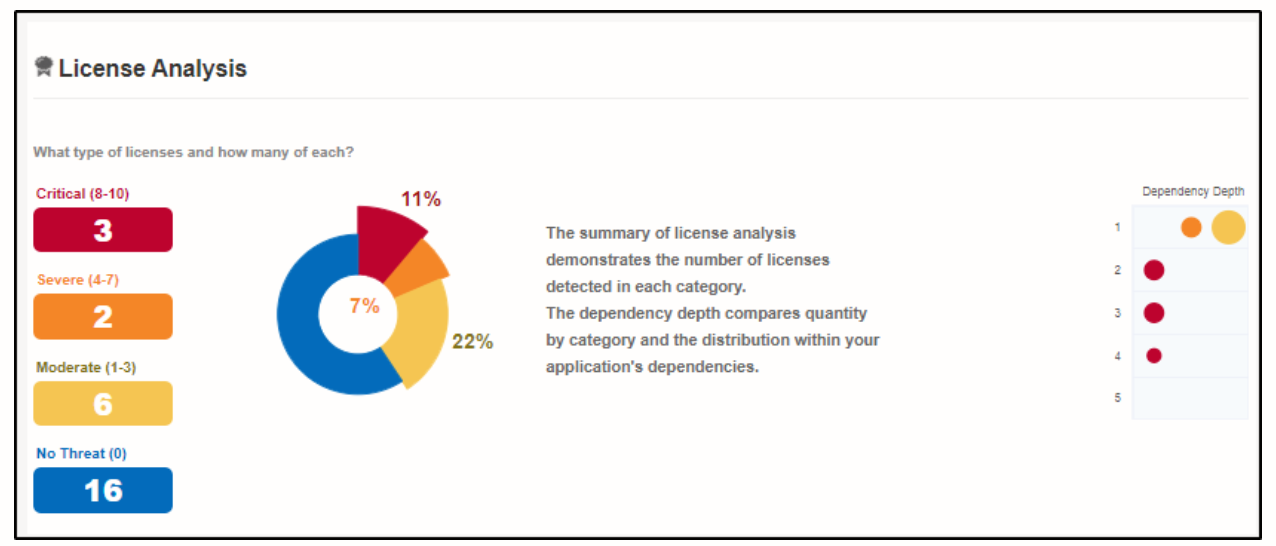
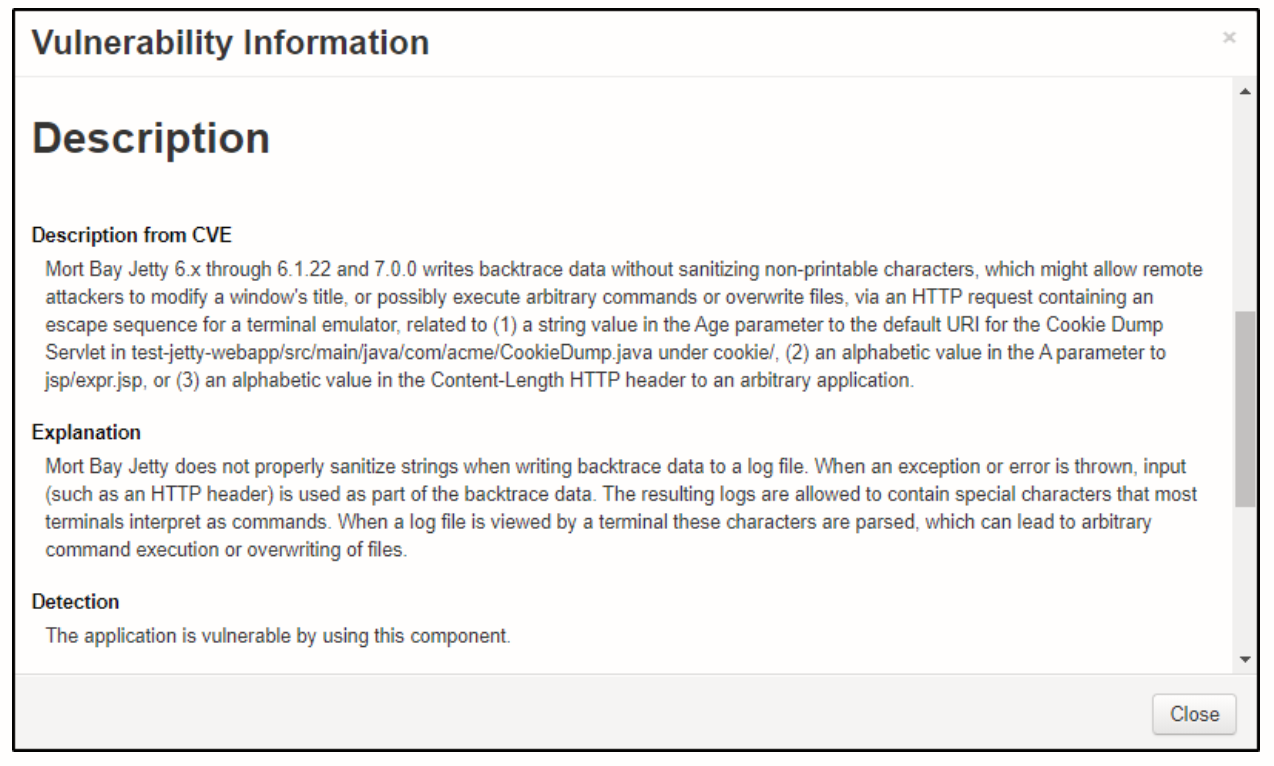 License Analysis
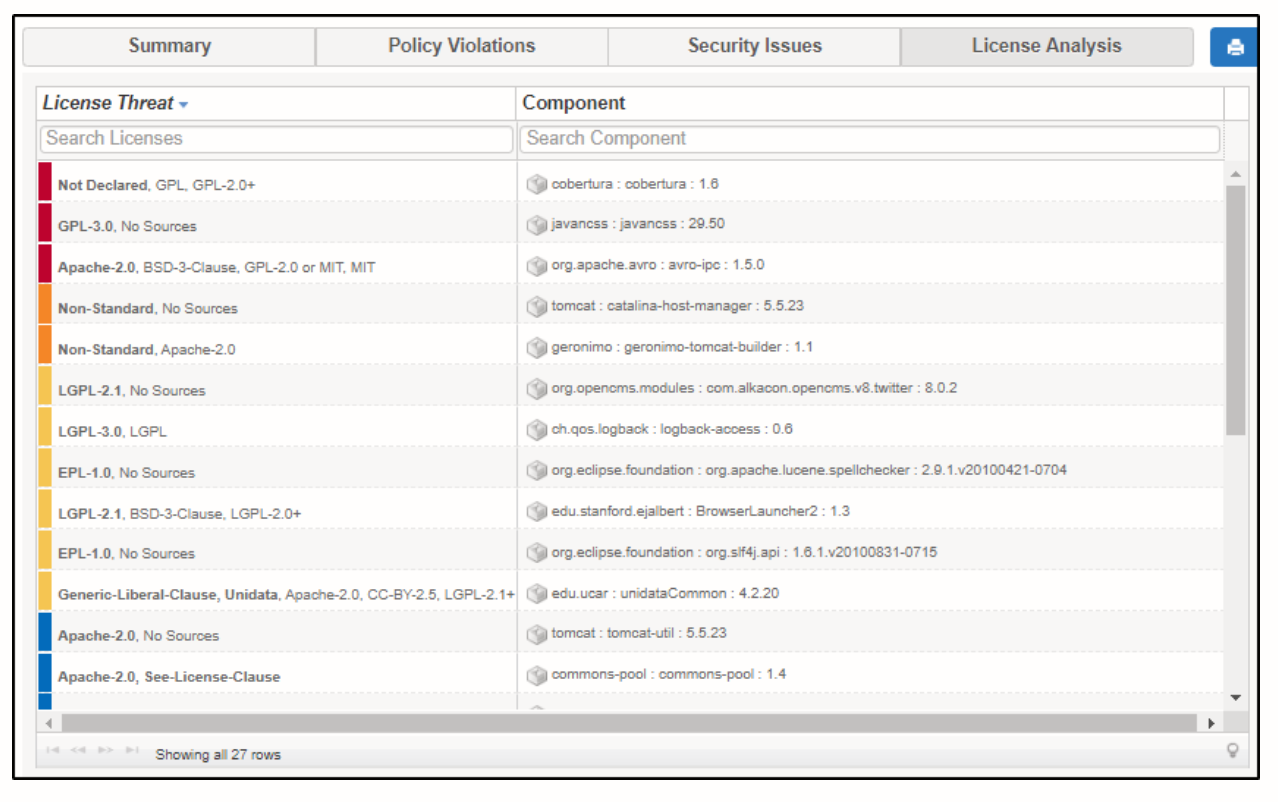
License Analysis
This tab will display policy violations with regard to the license of the application. Here again, you’ll find the details about the component and the policy that is violated.
Why You Should Use Sonatype Vulnerability Scanner
As I mentioned earlier, I’ve used a lot of vulnerability scanners. One major benefit of Nexus Vulnerability Scanner is that it’s one of the lightest scanners. It’s just about 40+ MB in size. This makes it easy for you if you want to use the scan on multiple host systems because it doesn’t take much time to download. (You can also upload your application to NVS in the cloud if you would prefer not to download the scanner.)
Additionally, installing and setting up the scanner is easy. All you have to do is download and extract. The application is in the form of an executable jar file.
Also, the results are presented well. As you’ve seen in the screenshots above, it’s very easy to analyze the results. Scanners such as Nmap and Nikto show the results on the terminal by just printing out the vulnerability issue. This looks unpleasant compared to the way Nexus Vulnerability Scanner displays the results.
And, finally, displaying the level of threat will help you prioritize your tasks when fixing problems.
Overall, Sonatype Vulnerability Scanner is a useful tool, and I’d suggest you try this scan and get the feel of it.