This Spring, the National Institute of Standards and Technology (NIST), released updated recommendations (.pdf) to improve software resilience against vulnerabilities. This builds on an earlier, four-part framework released last year.
As the department explains:
Few software development life cycle (SDLC) models explicitly address software security in detail, so secure software development practices usually need to be added to each SDLC model to ensure the software being developed is well secured. This whitepaper recommends a core set of high-level secure software development practices called a secure software development framework (SSDF) to be integrated within each SDLC implementation.
NIST updated the framework to provide guidance for assessing cybersecurity risks within open source components used by developers, building a software bill of materials (SBOM) to track the use and whereabouts of OSS components that may have vulnerabilities discovered in the future, and integrating automated security controls throughout the SDLC. NIST understands that secure software development practices in federal agencies is critical for successful digital transformations, delivering higher quality applications, and staying one step ahead of adversaries.
In our 2019 State of the Software Supply Chain report, we compared teams with and without automated open source governance capabilities to reveal the benefit of building applications using secure software development practices. Development teams who regularly automatically analyze and track open source components throughout the SDLC reduce the presence of known vulnerable components by 55%.
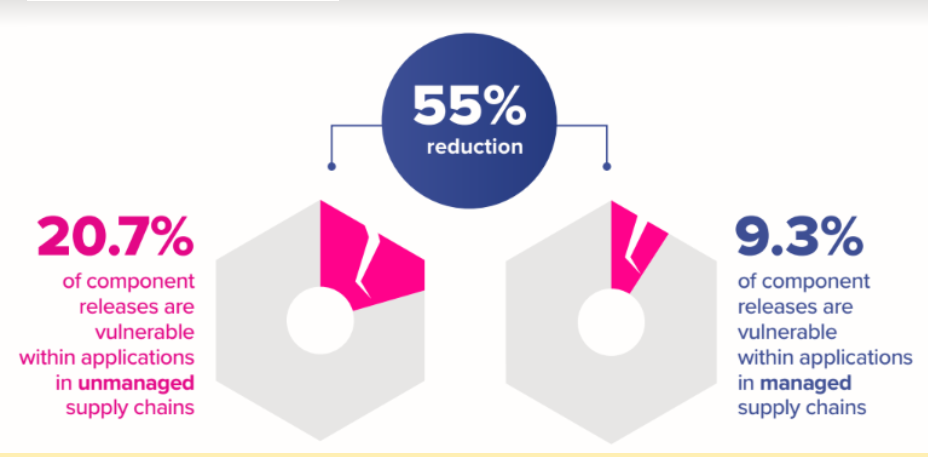
Image: 2019 State of the Software Supply Chain report
Software supply chains across industry and government are a primary target for adversaries today. The result: open source related breaches have jumped 71% over the past five years. Further, 22% of public sector developers reported a breach tied to their application development practices within the last 12 months, according to our latest DevSecOps Community Survey. Although the government sector had the highest percentage of teams beginning to apply DevSecOps practices compared to other industries (36%), the institutionalization of practices remains a necessity.
Agencies and industry adopting the NIST framework and guidelines will pave the way forward to protect citizens, businesses, and critical infrastructure from vulnerabilities in their SLDC.
Ron Ross, NIST Fellow and speaker at the DevSecOps Federal Leadership Forum said, "In the DevSecOps world things move very quickly. This is the exciting world of technology we are living in, DevSecOps practices can really help us manage the risks that go with this rapid development approach."
If you would like to learn more about the new NIST Framework updates, we invite you to join Ron Ross (NIST Fellow) and Derek Weeks (Sonatype VP) on June 24th for an interactive fireside chat. Tune in to hear why we should protect all forms of code, defend our software supply chains, and stay ahead of the latest adversarial attacks.





