The “Sec” in DevSecOps introduces application security in an agile framework as part of a continuous development process instead of as a secondary step to releasing software.
However, while adding security checks throughout the software development process has many benefits, such as decreasing the cost of fixing a security issue, it introduces some challenges as well.
In traditional software development, application developers and security teams are siloed into separate organizations in part due to the highly specialized knowledge technical security professionals maintain.
DevSecOps shares the responsibility of security with the application developer, who may not have this skill set. For this reason, it's important to choose tools that provide this knowledge and identify vulnerabilities for developers.
Two such types of tools are Software Composition Analysis (SCA) and Static Application Security Testing (SAST). Many articles attempt to pit these types of tools against each other in an SCA vs. SAST battle. In reality, they solve different pieces of the security problem.
A well-positioned application development team should really have both solutions in place. Read on to find out why.
What do SAST and SCA tools do?
While both SAST and SCA play vital roles in software development, they focus on different aspects of the security problem. Let's take a look at what these tools do.
Static Application Security Testing (SAST)
SAST tools examine source code for insecure code patterns, often providing feedback in a developer’s IDE or version control system, such as with GitHub Pull Requests.
SAST products are derived from static analysis tools, often known as linters, which have many uses outside security, such as detecting style deviations and general programming errors in source code that may not be caught by a language compiler. Often, these products will go beyond simply linting and attempt to help the developer prioritize insecure code issues that are the most important to address.
Software Composition Analysis (SCA)
SCA tools, on the other hand, detect the use of third-party (often open source) software dependencies, typically in the form of binaries, that contain known vulnerabilities.
These tools scan codebases to create a list of all used dependencies, both direct and transitive. The compilation of dependencies will then be compared to a list of known vulnerabilities, such as from the National Vulnerability Database. The SCA tool can then raise any concerns about packages found, and it may even provide upgrade recommendations.
Due to the high reliance of modern software on third-party code, in 2022 the average Java application contained 148 dependencies. It can be complicated and time-consuming to generate an accurate map of application dependencies. Data quality and scanning accuracy are both considerations to make when choosing an SCA tool.
SAST vs. SCA: What are the key differences?
One key difference between SCA and SAST is that SCA tools primarily identify and analyze binaries, while SAST tools focus on identifying security weaknesses in the source code itself.
From a dependency point of view, software applications can be divided into two parts: third-party (binaries) and first-party (application) code. The following diagram illustrates how SAST and SCA tools fit into that model.
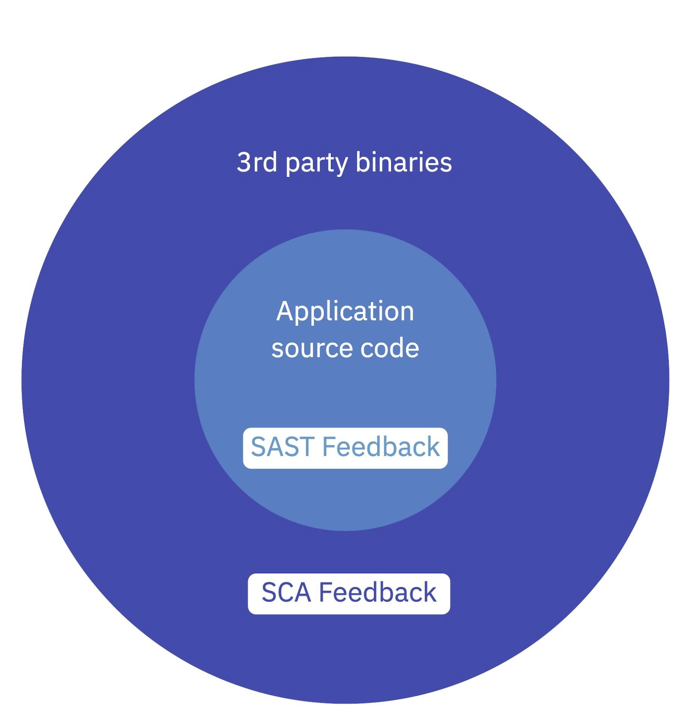
Each of SCA and SAST cover a different aspect of application code, and when used together, can provide a full picture of security posture, at least that which can be identified from looking at an application from a static context.
Why development teams need both
SCA and SAST tools both help ensure the security and stability of software applications. While they serve similar purposes, they contain key differences that make them suitable for different types of tasks. SCA tools identify and track dependencies and assess the security risks associated with them, while SAST tools identify security weaknesses in the source code of a software application.
Ideally, both SCA and SAST tools provide results in a tight feedback loop for actively developed applications. SCA tools help developers use third-party dependencies more safely by identifying known vulnerabilities that may be lurking in direct or transitive dependencies. Simply put, SAST and SCA both scan for security vulnerabilities — SAST scans your code, while SCA scans your dependencies.
While they serve different tasks, their functions also can be complementary. Both SCA and SAST tools improve the quality and security of software applications. While SCA tools focus on identifying potential issues in the code, SAST tools focus specifically on identifying security vulnerabilities. As such, these tools can be used together to provide a more comprehensive analysis of the codebase and help ensure the quality and security of the software.
SCA and SAST solutions from Sonatype
While there are many SCA and SAST tools available on the market, I would be remiss not to mention the robust solutions available through Sonatype.
OSS Index: SCA
Sonatype produces free open source tools for most major programming languages (including Java, JavaScript, Python, Go and many more) that can be used to scan open source dependencies.
Find out more about OSS Index.
Sonatype Lifecycle: SCA
For larger organizations that require a more robust SCA solution, Sonatype Lifecycle is a great option. When it comes to finding security vulnerabilities in open source dependencies, using a solution with high-quality data is one of the best ways to set your organization up for security success.
Find out more about how we curate this data.
Key takeaways
Long story short, when it comes to SCA and SAST tools, it's not about choosing one or the other. It's about learning how these two can complete each other, providing you with the most comprehensive security analysis.