This week in malware .... err actually ... this week in protestware, let's call it, and the tale of two-year-old Struts bug that's returned.
Sonatype continues to see an ongoing trend of developers voluntarily sabotaging their own projects to stand up for issues of public interest they deem paramount.
The return of Apache Struts RCE
As I reported this week, in 2020, Apache Struts project had patched a remote code execution (RCE) vulnerability, tracked as CVE-2020-17530. The vulnerability stemmed from untrusted OGNL Injections and was assigned a CVSS severity rating of 9.8 (Critical).
Although it was previously believed that the issue was squashed in Struts 2.5.26, security researcher Chris McCown found that the fix was incomplete.
The "double evaluation" of OGNL could still very well take place in versions 2.5.26 and above, leading to the assignment of a new vulnerability identifier: CVE-2021-31805, disclosed by Apache this week.
My colleague and security researcher Ali ElShakankiry traced the new fix for CVE-2021-31805 that went into Apache Struts version 2.5.30:
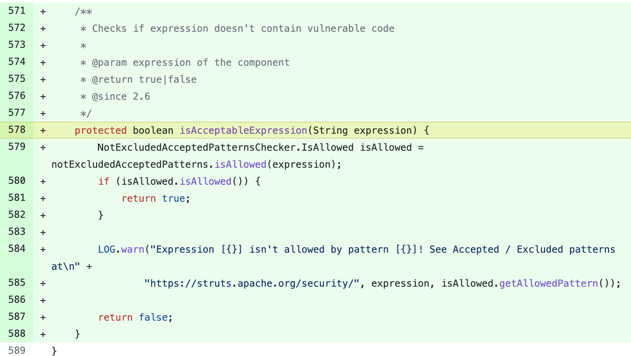
The newly applied fix prevents double evaluation of OGNL expressions crafted from untrusted user input, therefore preventing RCE.
U.S. CISA is urging everyone to upgrade to Struts 2.5.30 or greater to safeguard themselves against this RCE flaw. Users should additionally avoid using forced OGNL evaluation in the tag's attributes based on untrusted user input.
Protestware: An ongoing theme
What's more? Protestware—cases of maintainers behind popular open source projects sabotaging their own software to make a point continue to ramp up.
Although left-pad's incident of 2016 seemed isolated at the time, 2022 is turning out to be a whole lot different with the self-sabotage incidents repeating themselves. Below are some of these incidents:
- Jan 2022: Maintainer of popular 'colors' and 'faker' libraries adds code to DoS applications in protest of big corporations using open source but not contributing anything back to the community.
- March 2022: 'node-ipc' project begins deleting data of users it suspects to be Russian or Belarusian. Any application using the library ends up overwriting Russian users' files with a '❤️' emoji.
- March-April 2022: In days following the incident, maintainers behind npm libraries like 'event-source-polyfill', 'es5-ext' and 'styled-components' add peaceful anti-war messages to their packages.
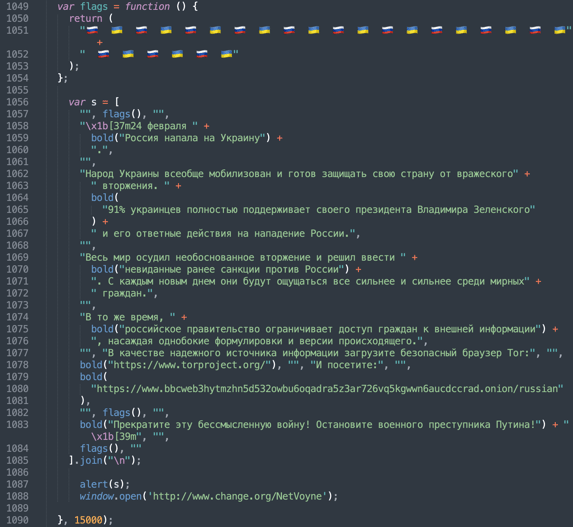
Granted, the current protestware wave is centered around trending issues that matter to most people, like open source funding, and the war, we are yet to see what future cases entail.
Developers have discovered an avenue of creative self-expression that no longer restricts them to just delivering expected functionality — a developer can, on a whim, decide to change their mind and their code as they please. A neglected premise of open source is that they always could.
Sonatype users remain protected
Customers of Sonatype Intelligence-powered products including Sonatype Repository Firewall, can rest assured that their software supply chains are protected from emerging threats to the open source ecosystem.
Within a few hours of the new Struts CVE being disclosed, the Sonatype security research team expedited full Deep Dive research on CVE-2021-31805 to notify IQ users of safe Struts 2 versions to upgrade to.
Last month, Sonatype Repository Firewall detected a sharp uptick in open source attacks after finding over 130 npm typosquats and dozens of malicious PyPI packages. Further, over 400 typosquats targeting Azure, Airbnb, and Uber developers were found and automatically blocked.
Firewall has also helped prevent dependency confusion attacks against prominent open source libraries like VMware VSphere automation SDK, keeping the overall software supply chain protected.
Users of Sonatype Repository Firewall are protected from such attacks as the suspicious packages once caught are automatically blocked from reaching development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is pending, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






