Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Part 3: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 21, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
In part two of my blog 'A Closer Look at Today's Software Supply Chain', I discussed why human-speed supply chain management can’t keep pace with today’s.
Read More...
Stewing Over Software Ingredients
By
Ryan Berg on July 15, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Just the other day I was planning dinner for my family and thought it would be a great idea to bust out the Dutch oven I had to have, but rarely use, and.
Read More...
Cheeseburger Risk: Not for the Faint of Heart
By
Derek Weeks on May 20, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
If you had a heart attack, would you stop eating cheeseburgers? For most people, the answer is “No”.
Read More...
Now that Heartbleed has become the new measuring stick for vulnerability disclosures, I have had several people ask me, “Is this OpenId/Oauth thing the next.
Read More...
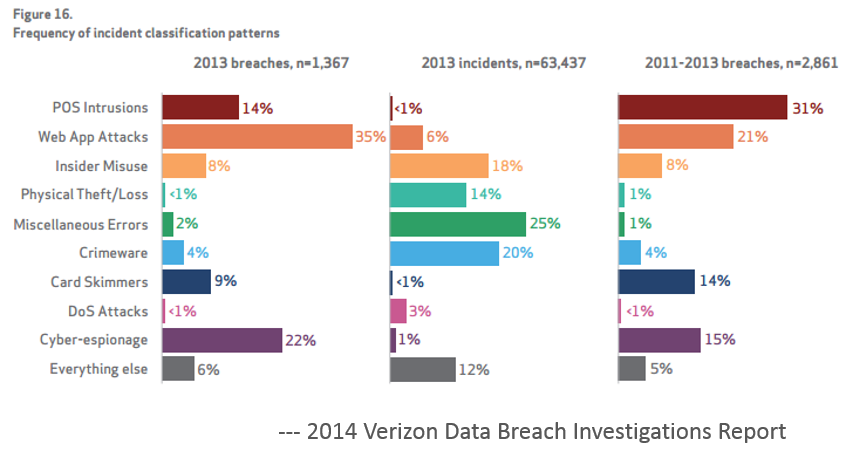
Like a Good Holiday, the Verizon Breach Report is Here
By
Ryan Berg on May 02, 2014
Sonatype Says
5 minute read time
Like a good holiday the Verizon 2014 Data Breach Investigation Report (DBIR) is something I look forward to every year.
Read More...
Do you trust your software supplier? Questions to ask yourself - and them!
By
Jessica Dodson on July 24, 2013
supply chain management
1 minute read time
Do you trust your software supplier? Questions to ask yourself - and them!
Read More...
Good Hygiene Should be a Foundation of Application Security
3 minute read time
Good Hygiene Should be a Foundation of Application Security
Read More...
Is it time for a Nexus Repository Health Check? Come to the Nexus Office Hours to get your Diagnosis.
By
Jessica Dodson on May 27, 2013
Nexus Repo Reel
1 minute read time
Is it time for a Nexus Repository Health Check? Come to the Nexus Office Hours to get your Diagnosis.
Read More...
Vulnerability database infected for at least two months
By
VAO on March 19, 2013
component vulnerabilities
15 second read time
Vulnerability database infected for at least two months
Read More...