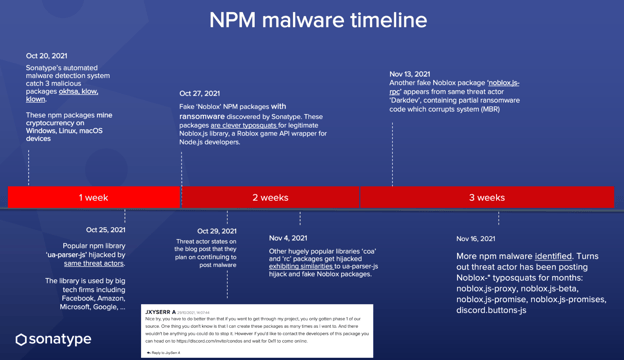
A new malicious package, noblox.js-rpc was spotted on the npm registry this month that leverages the same techniques we saw before to steal all sorts of sensitive data like credentials, files, and even the windows registration key and finally install ransomware. The package is being tracked under the identifier, sonatype-2021-1526 in Sonatype's security data.
The culprit, you ask? Darkdev — author of the fake Roblox API npm package that we caught last month installing ransomware on infected machines. This time around we are going to discuss the technical details behind the new malicious package and dive a bit deeper into the exploitation process that's behind these attacks.
To give you a recap, the following timeline illustrates the progression of events leading up to the discovery of "noblox.js-rpc":
Once again it all starts with a postinstall script in the package.json file of noblox.js-rpc. A simple one-line command is enough to start the mayhem, `node postinstall.js`.
The postinstall.js file is obfuscated similar to what we have seen before. We can start to figure it out or we can also run it and pay close attention to what happens behind the screen.
This seems to only target Windows machines by checking the operating system before grabbing the rest of the payload. A setup.bat file is created and executed. The batch script is obfuscated using variable expansion, which we demystify in a previous article, but this time with added complexity by repeating the variable expansion process multiple times. This batch script is where it really starts to get interesting and the one in charge of grabbing the rest of the executables to complete the attack, also known as a dropper.
The setup.bat file grabs four additional executables and one by one executes them.
- Rar.bat
- Rar.exe
- Rara.exe
- Mbr.exe
Similar to what we've seen before the first course of action is a batch script that adds a very general exclusion to Windows Defender, "C:\." This assures Defender will not stop the malicious executables from running. Next is exfiltration. This is achieved with both Rar.exe and Rara.exe.
First, what looks to be a custom-made stealer, Rar.exe. We can decompile it and take a look at the actual code behind the binary.
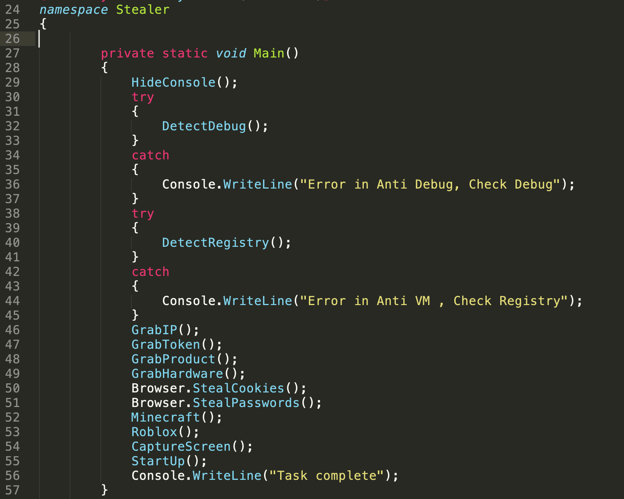
From the main method and the method calls, we can get a pretty good idea as to what this binary is trying to accomplish. The Minecraft() and Roblox() methods attempt to extract Minecraft session files and a Roblox cookie respectively. This speaks to the target audience the bad actors have in mind. At the end of the day, this package is going to be installed by Roblox players so it's worth checking if they also enjoy playing Minecraft.
No chances are to be taken, so in case anything was missed with this custom stealer, Rara.exe is then executed which proceeds to steal all credentials it can find.
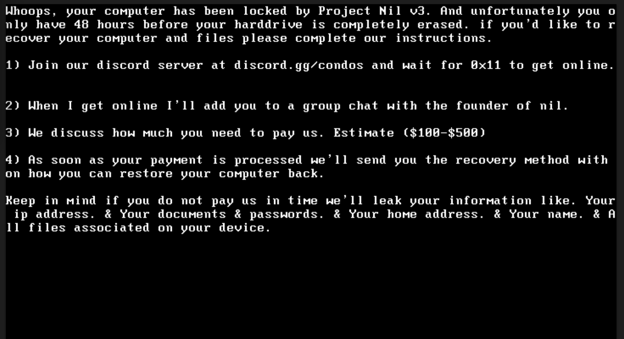
Finally, it's time to deploy the ransomware. Previous ransom notes suggested this could be an MBRLocker variant commonly used in pranks, and we continue to see consistent behavior here. Mbr.exe is used to overwrite the Master Boot Record, which leaves the machine unbootable. No evidence can be seen of files actually being encrypted, but it does leave your files inaccessible since the machine is not able to boot. The ransom message comes up asking the victim to wait for payment instruction in a discord server and although the attacker can't fix the victim's machine again, they likely have a good amount of sensitive data they can leak:
How are victims chosen?
Due to the nature of these packages, we know the attackers are targeting users of the popular Roblox game. But how do they get them to actually install a rogue npm package and then run it!? This was all made more clear when looking at the discord server named condos and with the help of one of the legitimate Noblox.js API maintainers, Moh Suufi who reached out to me via twitter.
"Condos is a euphemism for Roblox games about sex," Suufi tells me.
The attackers run a discord server where users share custom Roblox games, many of which are quickly reported and removed from the Roblox game platform. But this is also the place where attackers ask users to host bots for them in exchange for Robux, an in-game currency.
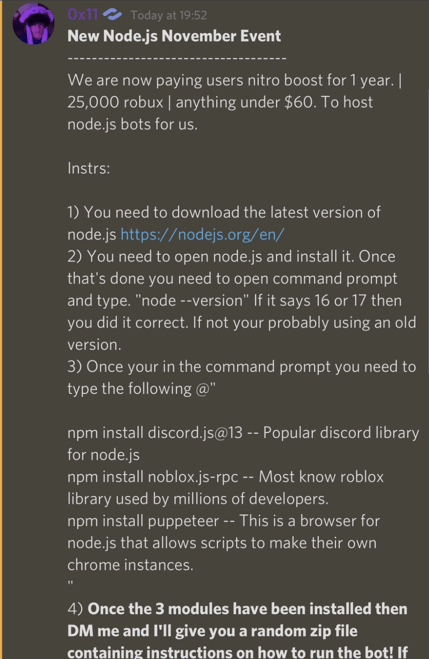
Once users install the malicious packages they are enticed into running them under the impression that they will be running bots for money. "He tries to make it seem like users will get something out of installing the malicious packages, but instead they get ransomware-like attacks on their computer," says Suufi. I guess in a way they are, except that instead of being paid they are asked to pay.
As demonstrated by the timeline above, and our prior blog posts, it seems the attacks against OSS repositories like npm are here to stay with threat actors finding innovative ways to infect their victims, and compromise the integrity and security of the software supply chain. Sonatype customers can rest assured with products like Sonatype Repository Firewall, powered by Sonatype Intelligence that keeps your software builds safe from threats like malicious npm releases, dependency hijacking packages, and similar risky OSS components.






