The last decade has seen increased reliance on software across every part of our lives. In parallel, we’ve seen a massive increase in attacks on this digital infrastructure, causing harm to financial markets, hospitals, and ultimately human lives. While there has been an increasing understanding within the software industry of these risks, it’s clear that we haven’t responded fast enough.
Governments the world over are struggling to define regulations that achieve the right outcomes, without causing undue harm to the software industry.
The slow pace of change to improve our cybersecurity is not keeping pace with the rapid evolution of the threat actors targeting our systems. The time has passed for half measures. We urgently need a moonshot to move the industry where it needs to be.
Today, the Biden administration announced their updated National Cybersecurity Strategy – and I believe it is the moonshot we need.
The Strategy acknowledges the difficult world we live in, and the threat actors aligned against us, many of which are hostile nation states. It is composed of two main fundamental shifts in how the United States will allocate roles, responsibilities, and resources in cyberspace.
A call for cybersecurity liability—holding software providers responsible
The first shift in this new Strategy is the rebalance of the responsibility to defend cyberspace. This shift contains the largest change in the software industry ever. The White House calls for a transition in the forces and responsibility for defending our digital ecosystem. Specifically, it calls for a radical transformation of software liability and contract law.
This is historic — the U.S. government has never taken a stance on issues of product liability with regard to software. The intent is to remove the ability for organizations to disclaim all liability in an End-User License Agreement (EULA) that consumers have no choice but to accept. The Strategy demands we replace this long-held policy with one that puts the onus on the company producing the software. It enables those companies to earn back liability protections in the form of safe harbors, consisting of well-defined best practices and standards that will likely mature over time.
We’ve long been calling for additional regulation. In an ideal world, companies would self-regulate their cybersecurity hygiene. However, as we see from the daily breach headlines, far too many companies are gambling with their cybersecurity practices — and are facing few consequences.
Government regulations might be the necessary motivator for action.
If no other manufacturing industry is permitted to ship known vulnerable or defective parts in their products, why should software manufacturers be any different? In any other sector it would be considered gross negligence. The Biden Administration’s new Cybersecurity Strategy rightfully wants that to be the same for software.
Furthermore, the Strategy also moves to hold companies accountable that collect massive amounts of information and then leave that information open to attackers. Without regulation changes, the ramifications of these types of breaches can be huge for consumers. Yet, the resulting lawsuits amount to a rounding error and a cost of doing business for the organizations themselves. Changing accountability dynamics is the only way to drive the proper outcomes.
When this Strategy comes to fruition, companies will no longer be able to blame an open source developer of a component integrated into a commercial product. Businesses that create and use software must employ rigorous methods to “prevent bad outcomes” and take full responsibility for protecting the consumer. We have seen this move across other industries result in the adoption of technology solutions – the time is now.
Investing in cybersecurity
The second fundamental shift of the Strategy realigns incentives to favor long-term investments in cybersecurity. This section outlines how the Federal Government will use all the tools available to help reshape motivations and market forces to reward security and resilience, and to embrace security by design. It also speaks to building a robust cyber workforce that will lead us into the future.
In another historic move, the government is calling for generational investments to:
- Renew infrastructure.
- Secure software and semiconductor supply chains.
- Modernize cryptographic technologies.
Similar to the conversation around liability, the government has never before put so much focus on fortifying the future of our cybersecurity posture. It’s an acknowledgement, at the highest level, that no one is going to win the cybersecurity game alone and that we need to work together as an industry, private, non-profit, and government, if we want to stem the surge in cybercrime.
We talk a lot about Edwards Deming and applying his supply chain principles to software – one of which is not passing a known defect downstream. One of the many reasons this is a problem is the incredible amount of technical debt that happens when you have to go back and constantly fix things and prevent forward motion. Not to mention the incredible amount of time and money wasted.
We’ve built a colossal amount of technical debt across our nation's cybersecurity infrastructure. Because there wasn’t a strong emphasis placed on investing for the future, planning for a post-quantum future, or supporting a growing cybersecurity workforce, we have a hole to dig out of.
Liability and resilience: Nearly a perfect duo
I was fortunate to have an opportunity to review and comment on a draft of the Strategy, and wholeheartedly support its call for accountability and holistic approach to solving a multifaceted problem. This is a bold move by the administration, ONCD, CISA, and every other agency involved in developing this, and a landmark moment for the industry. But it’s a moment not all in the technology and cybersecurity industries are going to appreciate… organizations who most need this shove forward are the same ones resisting all the existing best practices focusing instead only on the bottom line or moving through “check the box” minimal actions.
However, shifting accountability alone will not prevent bad actors from launching malicious attacks. Only when married with investment and hardwork, can progress be made. As organizations move to protect themselves, we must not lose sight of the overall goal – resilience through prevention. Successful security strategies will still depend on preemptive measures and vulnerability management programs.
Are you wondering how to evaluate if you’re close to “securing by design”? Or ready to take on the liability this Strategy calls for? Start by assessing your software supply chain.
Applying Deming's principles to software can help guide you:
- Use better and fewer open source projects.
- Use high quality components from those projects.
- Fix vulnerabilities or code quality issues at the beginning, and never pass them farther into the SDLC.
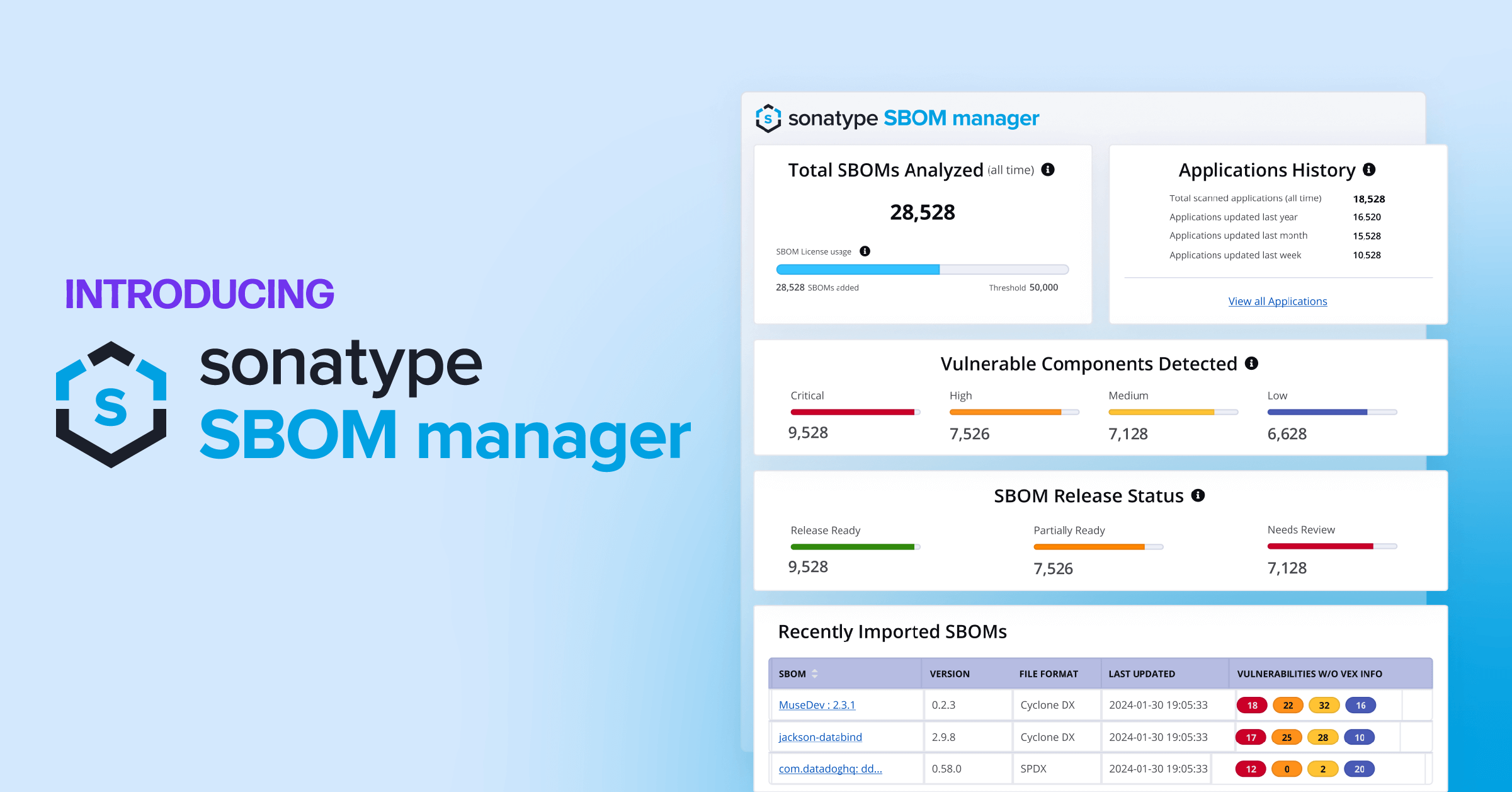
- Create transparency with software bill of material (SBOMs) that you continuously monitor.
Sonatype is also here to help however we can.
Twenty years ago, security technologist Bruce Schneier said, “there are no real consequences for having bad security, or having low-quality software of any kind.” For twenty years, I’ve been saying not much has changed. Today, we can finally retire this quote.


.jpg)