Like a good holiday the Verizon 2014 Data Breach Investigation Report (DBIR) is something I look forward to every year. Now that I’ve had some office time to digest this, I figured no better time to share my thoughts.
I am not going to cover all sections, but do want to highlight a few things that stuck out to me. I’ve been working in and around security for close to two decades and very few things surprise me anymore. Some people may even say that I tend to be more curmudgeon than security cheerleader these days (though I like to think that security is a journey with many more singles than home runs and true accomplishment requires a lot of strikeouts - hey it is baseball season).
Bigger Than Texas
One thing that clearly stuck out was the size of the report, with over 63,000 confirmed security incidents, a stark rise from last years report. Although there are many reasons for the dramatic increase from year to year, size of sample data for one, what can’t be ignored is that the scale is increasing at a logarithmic rate. While I already am moaning to myself for saying “the volume of breaches this year is big”, I really hope in 10 years from now, I am not making this same comment. None of us will have done enough if the report 10 years from now shows 6,300,000 confirmed incidents.
Security shouldn’t be like playing whack-a-mole at the county fair, though talk to any CISO and it certainly seems that way. One thing I love about the report is that it highlights security as a global problem that targets everywhere and impacts all industry verticals universally. This year’s report highlights that over 97 countries were represented in the data an increase of more than 350%. It seems nobody was immune, 50 million accounts at Evernote, Bit9, Facebook, Twitter, Apple, Microsoft, Sprouts, and many more - “we don’t see any industries flying completely under the radar".
I have said before this shouldn’t be a security game of pin the tail on the donkey. Everyone is, was, or will be impacted at some point. It truly is no-longer a matter of 'if', but more a case of 'when'. The sooner we as an industry begin to think this way universally the more secure we will be (remember “many at bats” and “more singles than home runs”).
Attacks Are Faster...Responses Not So Much
One of the more significant takeaways, for me at least, was the truly poor job we do in understanding the security of our systems. This couldn’t be more evident than the consistent measure of the time taken to attack and exfiltrate data against the time to discovery. Attackers are getting faster, with times measured in seconds to minutes, and our response time is measured in months. When Brian Krebs, knows more about your attack than you do this has to be a wake up call to the ineffective nature of the existing security spend, people, and process. This screams in many cases activity and not action. There may be a lot of security activity occurring but not enough targeted and measurable action.
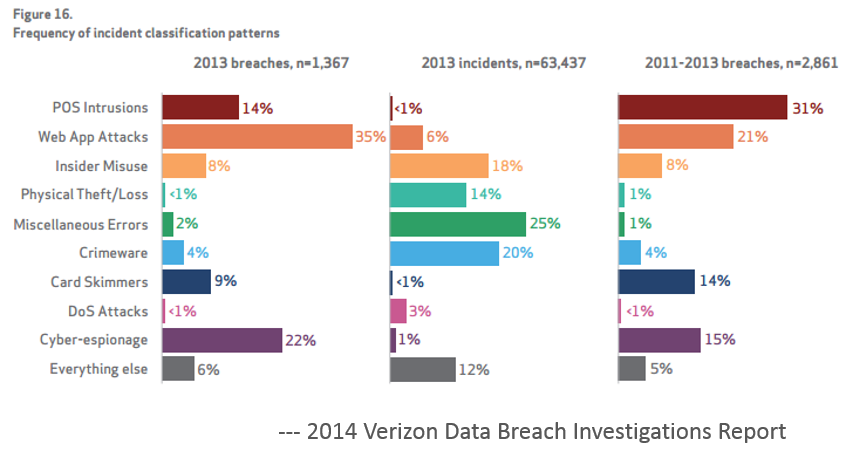
I won’t go into the details since I will safely assume you have or will be reading the report, but another interesting observation was the “nine patterns to rule them all”, while I agree that having a consistent way to group the data is beneficial these patterns unfortunately don’t work for me as they are a combination of attack scenarios, motivations, attack types and a couple of miscellaneous buckets when things don’t fit. That being said there are a few worthy things to note.
1. Security makes headlines long after the first shark attack.
This is evident in the recent focus on POS intrusions leveraging RAM scraping. As the report highlights, RAM scraping was noted in previous years. But even though this attack technique was well known organizations weren’t aware, didn’t care, or played the game of “likelihood chicken”. Either way, our lack of ability to hit some singles, for an attack already understood, certainly lead to some high profile exposures.
2. Hello FBI, no I didn’t know my credit cards were stolen. Are you sure?
The report highlights several times that 99% of companies attacked had to be told by someone else there was a problem. We know more about the “likes” and desires of our customers than who is stealing data from us, maybe we shouldn’t be surprised as it is a case of priorities after all.
3. Internet of Things (IoT) is the new WWW and all your friends are invited
Web applications remain the proverbial punching bag of the Internet. And increasingly we are seeing web and mobile apps to control devices in all areas of our lives. No surprise here, the running to the cloud mentality is only adding fuel to the fire. Everything is CRUD, REST, or some type of service and it's turtles all the way down.
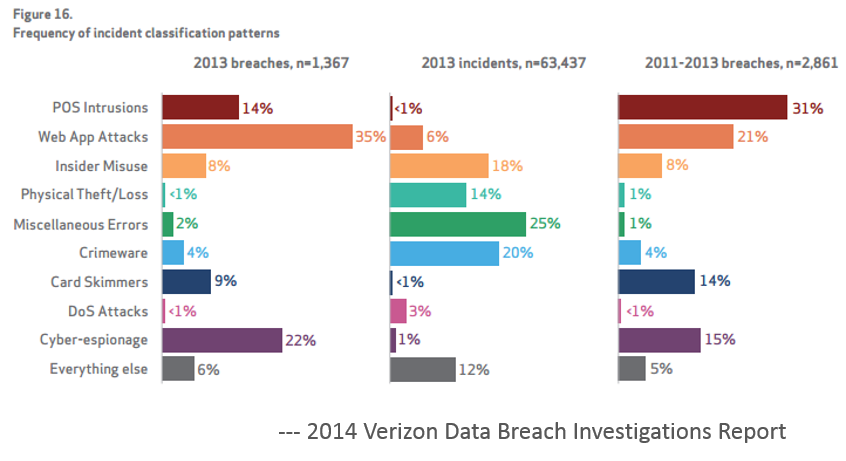
4. Cyber Espionage (they said Cyber not me)
Whatever you want to call it, the rules have changed, the Snowden revelations have made public what many people suspected in private, Governments have declared open season on the Internet and everyone is on notice. Unfortunately most organizations are simply unprepared, under resourced, and out gunned for this type of adversary.
5. Patch all things
Even though this was highlighted deep in the report, we shouldn’t take this lightly. EVERYTHING must be considered part of your global supply chain, not just your browser, OS, third-party software, but also the open source software components that make up of all of the above. This part of our software supply chain has seen several high profile attacks, including OpenSSL and Struts (just within the last few weeks).
Open source components are an increasing focus for attacks and far too many organizations aren’t paying attention to the alerts, tracking what components they are using, or patching them when vulnerabilities are disclosed. Even worse, organizations continue to download and reuse components with known vulnerabilities long, long after the first disclosure of risk. Where the time to breach and time to discovery is measured in months, the time to update a known component with a known vulnerability and a known fix is often measured in years.
The Heartbleed response to patching was an anomaly. Organizations are not patching their software, and the hackers are having a field day with your web applications because of it.
6. Controls, More Controls, and Even More Controls
Controls are great, and having a place to start even better, but when we treat security as a measurement against a specific set of controls that are non-sufficient, out of date, or simply not applicable, it makes it too easy to not see the forest through the trees. One thing that stood out to me from the SANS Critical Security Controls is that we still haven’t addressed the software we build as part of a global supply chain and if you don’t have controls surrounding all aspects of the software you use, build, and depend on, your mileage may vary.
Draw Your Own Conclusions, and Share Them
This year’s report is well written and sums up a lot of security activity in a mornings read, and this year was no exception. If you haven’t read it yet and you have any interest in security you should, it can be found here: Verizon 2014 Data Breach Investigation Report.
If interested in more commentary, you can also follow remarks on Twitter by following hashtag #DBIR.