We've seen so many software supply chain attacks in recent weeks that it's hard for us to talk about all of them. But, in the last 24 hours, we've seen two major issues that are important for everyone to take notice of:
-
A critical improper input validation vulnerability in the npm component "netmask"
-
PHP's Git server was hacked in a sophisticated supply chain attack
First, let's discuss netmask. Yesterday evening, I broke the news on a critical improper input validation vulnerability that had been lurking in a popular npm component.
Assigned CVE-2021-28918, the flaw concerns the netmask component that gets over 3 million weekly downloads on npm, and is a dependency for almost 280,000 GitHub repositories.
The flaw itself stemmed from netmask treating octal IP addresses as decimal. More specifically, if an IP address started with "0," the zero would simply be discarded by netmask rather than the component considering the possibility of the IP having been provided in a different (octal) format.
Although IPv4 addresses are most commonly expressed in decimal form, an IP address can be written in a different format too, including hexadecimal and integer.
For example, your localhost or loopback address 127.0.0.1 is the same as writing "2130706433" or "0177.0.0.1."
Applications interacting with networks, including your web browser, account for this and for example, typing 2130706433/ in your web browser's address bar will quickly resolve to and go to its decimal equivalent, which is 127.0.0.1.
However, what should happen if you prefixed a zero to what looked like an IPv4 address?
0127.0.0.1 (notice the prefixed zero) is actually not the same as 127.0.0.1, but a different IP address 87.0.0.1 expressed in octal format.
netmask did not account for different IPv4 formats
Whereas, typing (an octal IP) 0127.0.0.1/ in your web browser quickly changes to its decimal equivalent 87.0.0.1/, in case of "netmask" the zero would be simply discarded.
This in turn can weaken Access Control Lists (ACL) depending on how these are implemented. And because, "netmask" is used by a huge number of applications, the exact scope of risk resulting from exploitation of such a flaw remains wide, comprising many possibilities.
In examples shared by researchers Victor Viale, Sick Codes, Nick Sahler, Kelly Kaoudis, and John Jackson, who had responsibly reported this vulnerability, attackers can abuse this flaw to conduct attacks from Server-Side Request Forgery (SSRF) bypass to Remote File Inclusion (RFI).
Supply chain vulnerabilities and attacks rising, Sonatype customers have an edge
Because of the critical nature of this vulnerability, the aforenamed researchers engaged in a coordinated vulnerability disclosure process with netmask's developer and waited to publicly disclose their findings until multiple bugs associated with this CVE were fixed.
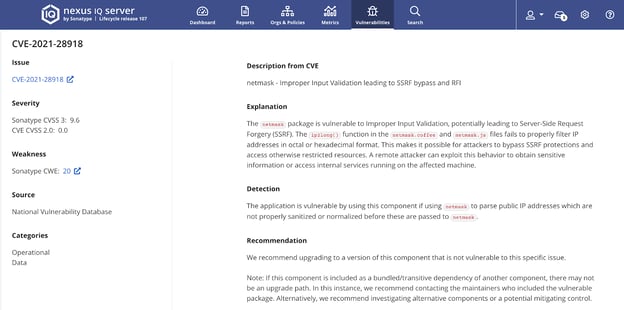
As soon as details on CVE-2021-28918 were released, Sonatype customers using the vulnerable "netmask" versions immediately received remediation instructions on the vulnerability, giving them an edge.
Users of "netmask" should upgrade to version 2.0.0 or above released on npm downloads.
PHP Git server attacked in a sophisticated supply chain attack
Unfortunately, this was not the only news to start off the week, a new story emerged this morning on how PHP's Git server was hacked in a supply chain attack.
The threat actors behind the hack altered PHP's source code via illicit commits that served no other purpose than planting backdoors right within PHP code base.
This news is alarming as the PHP programming language powers almost 8 out of 10 websites on the internet.
This is what makes attacks on the open source ecosystem so attractive to adversaries.
By breaching PHP's official code base and committing malicious code upstream, had it gone unnoticed, attackers would have been able to distribute their malicious code downstream to an unprecedented number of sites and web assets.
Thankfully, PHP developers and maintainers quickly caught the malicious commits before these were merged and distributed downstream.
As a safeguard, PHP's official git repository has now been relocated to GitHub, with code contributors now required to follow a specific set of instructions before they can contribute.
While the exact cause of compromise of PHP's Git server is yet to be determined, another lesson that can be learned from this incident is that CI/CD tools running on self-hosted servers can fall out-of-date easily, unless the latest patches and updates for vulnerabilities are applied from time to time.
Sonatype's 2020 State of the Software Supply Chain states that next-generation upstream software supply chain attacks are far more sinister because bad actors are no longer waiting for public vulnerability disclosures. Instead, they are taking the initiative to contribute code to open source projects and then - unbeknownst to the other OSS project maintainers - injecting malicious code. Those code changes then make their way into open source projects that feed the software supply chains of developers around the world.
And this is happening at a rapidly increased rate. In fact, there was a 430% increase in upstream software supply chain attacks in 2020, and we've already recorded over 5,000 upstream attacks in 2021. Keeping this in mind, it would be impossible to manually assess and track all changes to all components that might be targeted in upstream attacks.
Between 2020 and now, we have time and time again seen open source malware infiltrating multiple ecosystems, novel security vulnerabilities lurking in components, and the notorious dependency confusion attack that caught numerous Fortune 500 corporations off guard.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from such attacks.

Ax is a Staff Security Researcher & Malware Analyst at Sonatype with a penchant for open source software. His works and expert analyses have frequently been featured by leading media outlets including the BBC. Ax's expertise lies in security vulnerability research, reverse engineering, and ...
Explore All Posts by Ax Sharma


