**NOTE: The results of the 2019 DevSecOps Community Survey, mentioned below, are now available for download here.
Early this morning news broke that 620 million account details stolen from hacked websites were up for sale on the dark web. The scale of the stolen account details is daunting. But the more interesting revelation about this news is that the adversary responsible for breaching the 16 sites in question, noted his entry point: exploiting security vulnerabilities within web applications to gain remote-code execution and then extract user account data.
Web application breaches are a not new topic to us at Sonatype. It’s an area of software development and cybersecurity hygiene that we have covered for several years. In fact, we just wrapped up the collection of responses from our 2019 DevSecOps Community Survey on February 4th, where we had asked the question “Have you experienced a web application breach in the past 12 months?”
While we’ll be releasing full set of findings on March 4th, we thought it imperative with today’s news to share one of this year’s survey responses: 26% of respondents (797 of 3104) said they either confirmed or suspected a web application breach within their organization over the past 12 months.
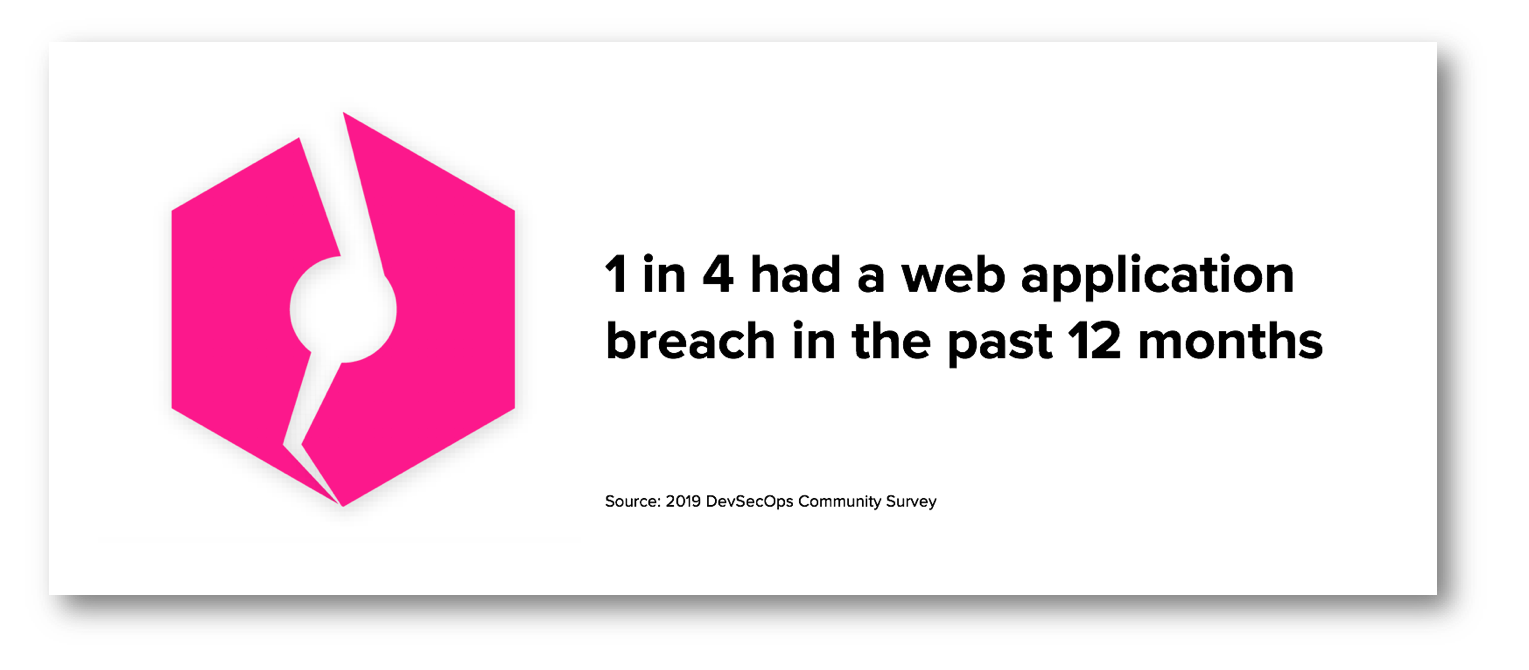
Let that begin to sink in: 1 in 4 organizations were acknowledging breaches due to a security vulnerability in a web application. The same approach used by adversaries to breach 16 sites and gain access to 620 million account details, also impacted 797 respondents from our 2019 survey.
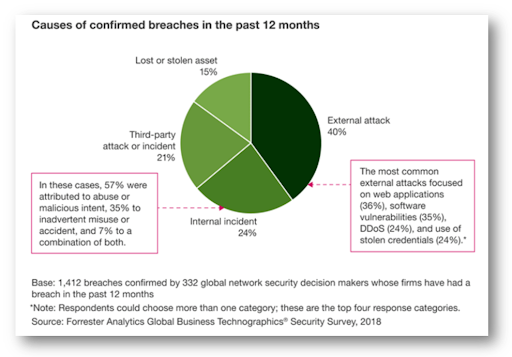
We are not the only ones to see this pattern of successful breaches emerging. In December, Forrester Research released data showing that the leading cause of successful breaches stemmed from external attacks. Among those external attacks, web applications breaches topped the list of most successful breach points (36%).
What makes web applications more vulnerable to a breach than other forms of attack? First of all, web applications are publicly facing and are easy for adversaries to find. Then, one only needs to look so far as cybersecurity hygiene reports from the JavaScript community. JavaScript is one of the world’s most popular programming languages used by web application developers to create dynamic and interactive web pages. To accelerate the composition of these applications, 6 million JavaScript developers around the world rely upon reusable sets of JavaScript code known as npm packages. Over 85% of a modern web application is composed from these npm packages.
Pair that perspective with data from an October 2018 report that revealed 51% of npm packages downloaded by web application developers had a known security vulnerability.
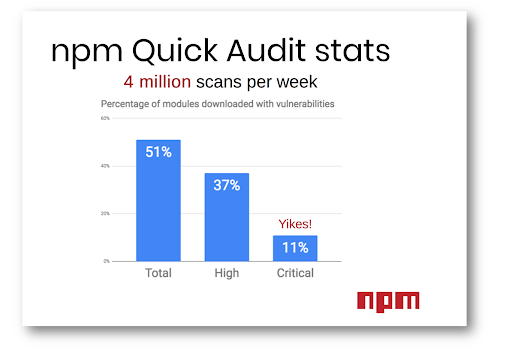
When empirical evidence shows that half of components commonly used to build web pages from have a known security vulnerability, one has to ask if anyone is paying attention to what parts are being used to assemble today’s software. In fact, researchers at Northeastern university did ask this question and shared their results in the report, Thou Shall Not Depend on Me. The researchers noted that “using data from over 133,000 websites, we show that 37 % of them include at least one [npm package] with a known vulnerability.
This latest announcement is yet another example of how businesses electively put their customers’ data at risk. As consumer awareness increases, they are likely to become much less tolerant of those companies who fail to implement proper security when they have the tools available to do so.







