Executive summary
In this blog post we list at least 10 open source packages affected by the HTTP/2 'Rapid Reset' vulnerability, disclosed by Cloudflare this week.
Tracked as CVE-2023-44487, the vulnerability resides in the HTTP/2 protocol, or rather the way it's implemented by various software projects, many being open source.
According to Cloudflare, the vulnerability stems from a weakness in the HTTP/2 protocol that can be exploited "to generate enormous, hyper-volumetric Distributed Denial of Service (DDoS) attacks." Attackers that exploited the flaw in the wild have reportedly been able to conduct "record-breaking" DDoS attacks, exceeding 201 million requests per second (rps) as observed between August and this month alone.
While the much-hyped curl CVE ended up being overblown [1, 2] and not nearly as bad as expected, HTTP/2 'Rapid Reset' on the other hand resides in and has been patched by several open source projects — some of which continue to announce a fix for the flaw in their latest versions.
U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an advisory urging "organizations that provide HTTP/2 services "to apply patches when available and consider configuration changes and other mitigations." Similar advisories have followed from Google Cloud, Amazon Web Services (AWS), and Microsoft.
Whereas open source projects impacted by the bug are in the likes of Apple's swift-nio-http2 library, Eclipse Jetty, Tomcat Coyote, among others.
Open source projects affected by HTTP/2 'Rapid Reset'
Given the significant number of distinct components affected by CVE-2023-44487, we have chosen to assign distinct Sonatype IDs to these projects, as listed below, for simplicity of cataloguing and due to intricacies (e.g. backports) associated with individual projects.
A huge shout out to Austin Brinkman, our principal security researcher, for staying on top of these projects as disclosures unfolded in real time.
- sonatype-2023-4379 - org.eclipse.jetty.http2:jetty-http2-common
- sonatype-2023-4385 - proxygen
- sonatype-2023-4380 - io.netty:netty-codec-http2
- sonatype-2023-4382 - org.apache.tomcat:tomcat-coyote
- sonatype-2023-4383 - github.com/nghttp2/nghttp2 (golang)
- sonatype-2023-4389 - Apache Traffic Server
- sonatype-2023-4386 - google.golang.org/grpc
- sonatype-2023-4387 - k8s.io/kubernetes
- sonatype-2023-4384 - github.com/envoyproxy/envoy
- sonatype-2023-4388 - libnghttp2
The Sonatype Security Research team continues to track the growing list of open source projects affected by the flaw, and we are keeping our products up to date with these disclosures to safeguard our customers against vulnerable components.
Users are advised to check their instances for specific detection and remediation advice.
Sonatype’s products such as Lifecycle and Repository Firewall stay on top of attacks and vulnerabilities and provide you with detailed insights to thwart zero-days, Potentially Unwanted Applications (PUAs), malware, and vulnerable components from reaching your builds:
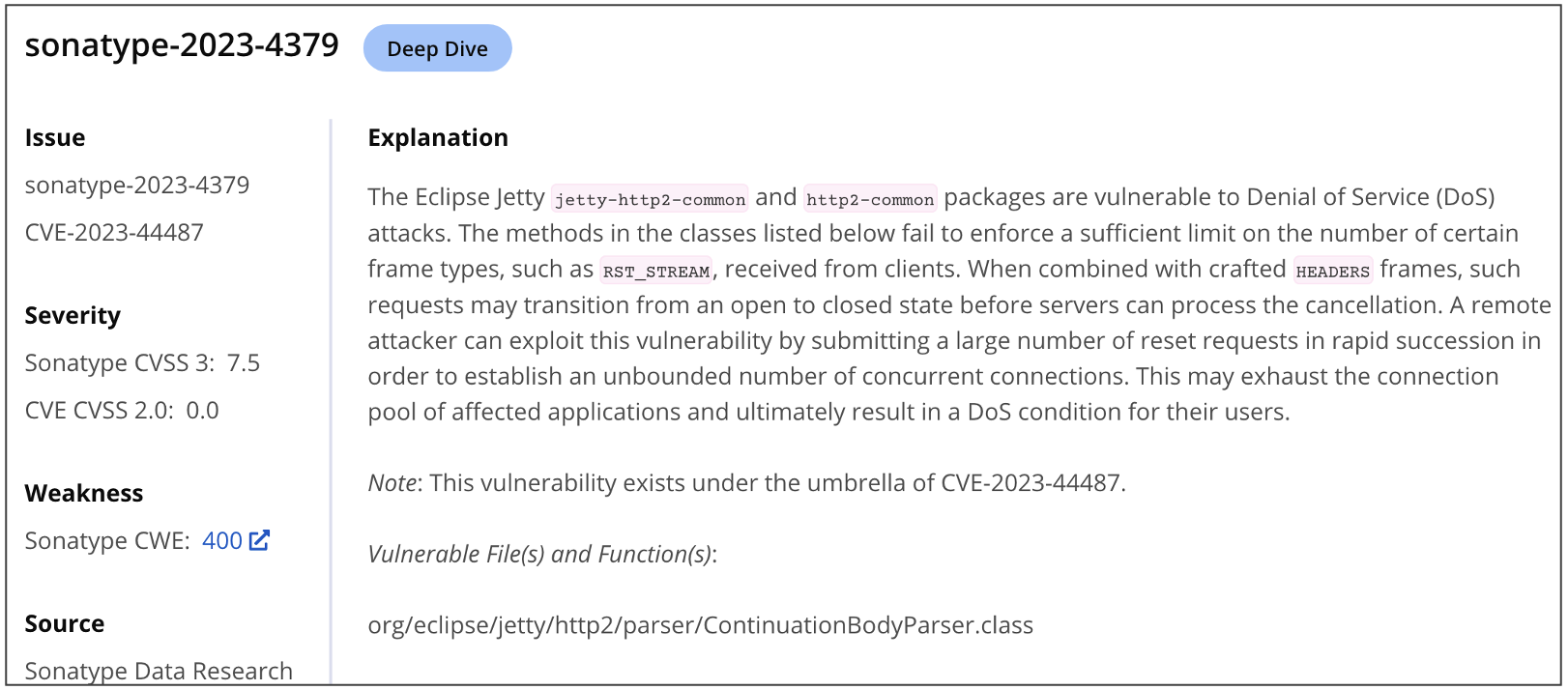
Lifecycle customers can rest easy knowing that vulnerable components lurking in their development builds would be flagged. Developers are provided specific advice on detection and remediation for every vulnerability thereby empowering them during the software development life cycle.




