Spring, a widely used component, makes programming multiple things in Java easier, faster, and safer. The project’s focus on speed, simplicity, and productivity has made it one of the world's most popular Java frameworks. Spring’s multifaceted use cases include building microservices, cloud apps, and event driven systems. Spring is the choice of framework for countless Java developers building sleek MVC applications.
Today, however, we bring to light a serious vulnerability that has impacted some versions of Spring and offer remediation tips. If you’re an avid Spring Web user it is a good idea to check and see if you are impacted by this vulnerability.
Name of the vulnerability: CVE-2019-3773
Type of vulnerability: XXE
Severity 8.8
CVSS 3.0 Metrics: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Version Affected:
- org.springframework.ws:spring-ws-core-tiger - All versions are vulnerable.
- Org.springframework.ws:spring-xml
- For 3.x: all versions prior to 3.0.5.RELEASE are vulnerable.
- For 1.x and 2.x: all versions prior to 2.4.4.RELEASE are vulnerable.
- org.springframework.ws:spring-ws-core:
- For 3.x: all versions prior to 3.0.5.RELEASE are vulnerable.
- For 1.x and 2.x: all versions prior to 2.4.4.RELEASE are vulnerable.
Vulnerability Description:
The Spring Web Services `spring-ws-core` and `spring-xml` packages are vulnerable to XML External Entity (XXE) attacks. Multiple files throughout the component fail to properly restrict the processing of malicious XML external entities. A remote attacker can exploit this vulnerability by crafting and submitting XML data containing malicious external entity references. The attacker can leverage this vulnerability to perform various XXE related attacks against the server.
Advisory Deviation Notice: The Sonatype security research team discovered that the fix for this vulnerability was actually introduced in version 3.0.5.RELEASE (for 3.x versions) and not version 3.0.6.RELEASE as stated in the advisory.
Attack Mechanics:
A remote attacker can exploit this vulnerability by crafting and submitting XML data containing malicious external entity references. The attacker can leverage this vulnerability to perform various XXE related attacks against the server.
XXE attacks work because within the legitimate XML input which was expected by the application, an attacker manages to inject external DTD links within the <!DOCTYPE> tags. The tags when parsed by the application can cause all sorts of security issues depending on the context in which they are being used in the application. XXE attacks have been the delivery vector for security vulnerabilities like Server-Side Request Forgery (SSRF), Code Injection or Denial of Service (DoS).
Here’s an example of how a typical attack might work:
The `DocumentBuilderFactory`, `XMLInputFactory` and other `*Factory` classes present in vulnerable versions of Spring Framework did not previously restrict loading of external XML entities present in the input. This would have made conducting XXE attacks possible for an attacker. The fixed classes (typically ending in “Utils.class”) disabled loading of external XXE entities by default.
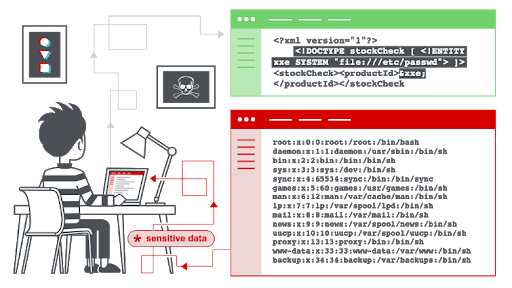 Image source: https://portswigger.net/web-security/xxe
Image source: https://portswigger.net/web-security/xxe
Remediation Recommendation:
Luckily, the `TransformerFactoryUtils` and similar `*Utils` classes implemented in the fix for the vulnerability contains an in-built protection which prevents “external entities from accessing,” right when a TransformerFactory object is conceptualised. Therefore, when working with a project relying on XML data heavily, developers can incorporate the equivalent classes ending in `*Utils` to benefit from the inbuilt protections.
Sonatype recommends upgrading to version 3.0.5.RELEASE or above of component `org.springframework.ws:spring-ws-core` which contains the fix for this vulnerability. For users of 1.x or 2.x, who are unable to upgrade to 3.0.5.RELEASE, can upgrade to the fixed 2.4.4.RELEASE instead.
DevOps-native organizations with the ability to continuously deploy software releases have an automation advantage that allows them to stay one step ahead of the hackers. Customers of Sonatype Nexus were notified of CVE-2019-3773 within hours of the discovery. Their development teams automatically received instructions on how to remediate the risk.
If you're not a Sonatype customer and want to find out if your code is vulnerable, you can use Sonatype's free Nexus Vulnerability Scanner to quickly find out.
Visit the Nexus Intelligence Insights page for a deep dive into other vulnerabilities like this one. Or, subscribe to automatically receive Nexus Intelligence Insights hot off the press.






