On March 11, 2024, the Cybersecurity and Infrastructure Security Agency (CISA) and the Office of Management and Budget (OMB) unveiled the final version of the Secure Software Development Attestation Form. This pivotal document, two years in the making, is set to transform the enforcement of minimum security standards for software purchased by US Federal agencies. Crafted in response to the Executive Order on enhancing national cybersecurity issued in 2021, the form requires vendors supplying software to federal entities to certify through a CEO or an authorized designee's signature that their software is developed securely, adhering to the Secure Software Development Framework (SSDF) guidelines established by NIST.
This attestation form, centralizing submissions at https://softwaresecurity.cisa.gov/, places a significant emphasis on the security of the software supply chain, demanding organizations demonstrate advanced maturity levels in this area.
The Sonatype Platform emerges as an invaluable tool in this landscape, offering swift and comprehensive compliance with SSDF requirements, thus facilitating organizations' adherence to these new standards.
Who needs to sign the attestation?
It applies to software developed or significantly updated after September 2022, with exemptions for software directly developed by Federal Agencies, open-source software obtained directly by an agency, third-party open-source components integrated into agency-used software, and software that is freely obtained and publicly available. Essentially, this encompasses software sold to federal agencies, barring bespoke subcontracted solutions (which are subject to similar rules via FAR regulations). For entities already compliant with FedRAMP, written approval can be sought from a third-party assessor in lieu of completing the attestation form.
What are the Major Requirements being attested for?
The attestation focuses on four critical areas:
- The software is developed and built in secure environments;
- The software producer makes a good-faith effort to maintain trusted source code supply chains by employing automated tools or comparable processes to address the security of internal code and third-party components and manage related vulnerabilities;
- The software producer maintains provenance for internal code and third-party components incorporated into the software to the greatest extent feasible;
- The software producer employs automated tools or comparable processes that check for security vulnerabilities. In addition:
a) The software producer operates these processes on an ongoing basis and prior to product, version, or update releases;
b) The software producer has a policy or process to address discovered security vulnerabilities prior to product release; and
c) The software producer operates a vulnerability disclosure program and accepts, reviews, and addresses disclosed software vulnerabilities in a timely fashion and according to any timelines specified in the vulnerability disclosure program or applicable policies.
Each bullet has its own sub-requirements, and each is based on the SSDF which lays out specific examples for each section.
Requirement #1: The software is developed and built in secure environments
The section focuses on verifying the software producer's commitment to maintaining secure and trusted source code supply chains. It encompasses the use of automated tools and processes to secure internal and third-party components and manage vulnerabilities effectively. The form outlines specific security and policy management practices, such as identifying and documenting security requirements, integrating toolchains, deploying and maintaining tools, and securing development environments. Notional examples include defining security policies for development infrastructures, educating on security requirement changes, and integrating security tools in the developer toolchain.
The Sonatype Platform's features align with these practices, offering industry-standard policy engines, automatic policy enforcement, and robust monitoring capabilities. It facilitates the automation of policy definition, vulnerability management, and integration of security tools across the software development life cycle (SDLC). The Platform's features support the continuous and automated verification of software component integrity and compliance with organizational requirements.
Requirements #2 and #3: The software producer makes a good faith effort to maintain trusted source code supply chains and maintains provenance for internal code and third-party components incorporated into the software to the greatest extent feasible
These two sections underscore the software producer's obligation to maintain accurate provenance for both internal code and third-party components integrated into their software. This involves communicating clear security requirements to all third parties supplying commercial software components for reuse, encompassing security criteria, vulnerability disclosure, and product security incident response capabilities. Examples include setting core security requirements for software components in acquisition documents, requiring third parties to attest compliance with these security requirements, and demanding provenance and integrity verification for all software components.
The Sonatype Platform aligns with these requirements by providing a comprehensive policy set that adheres to industry standards such as SSDF, PCI, and IEC. It enables organizations to enforce security policies automatically, verify third-party compliance, create and manage software bills of materials (SBOMs) that detail component provenance and integrity, and automate enforcement actions for non-compliance.
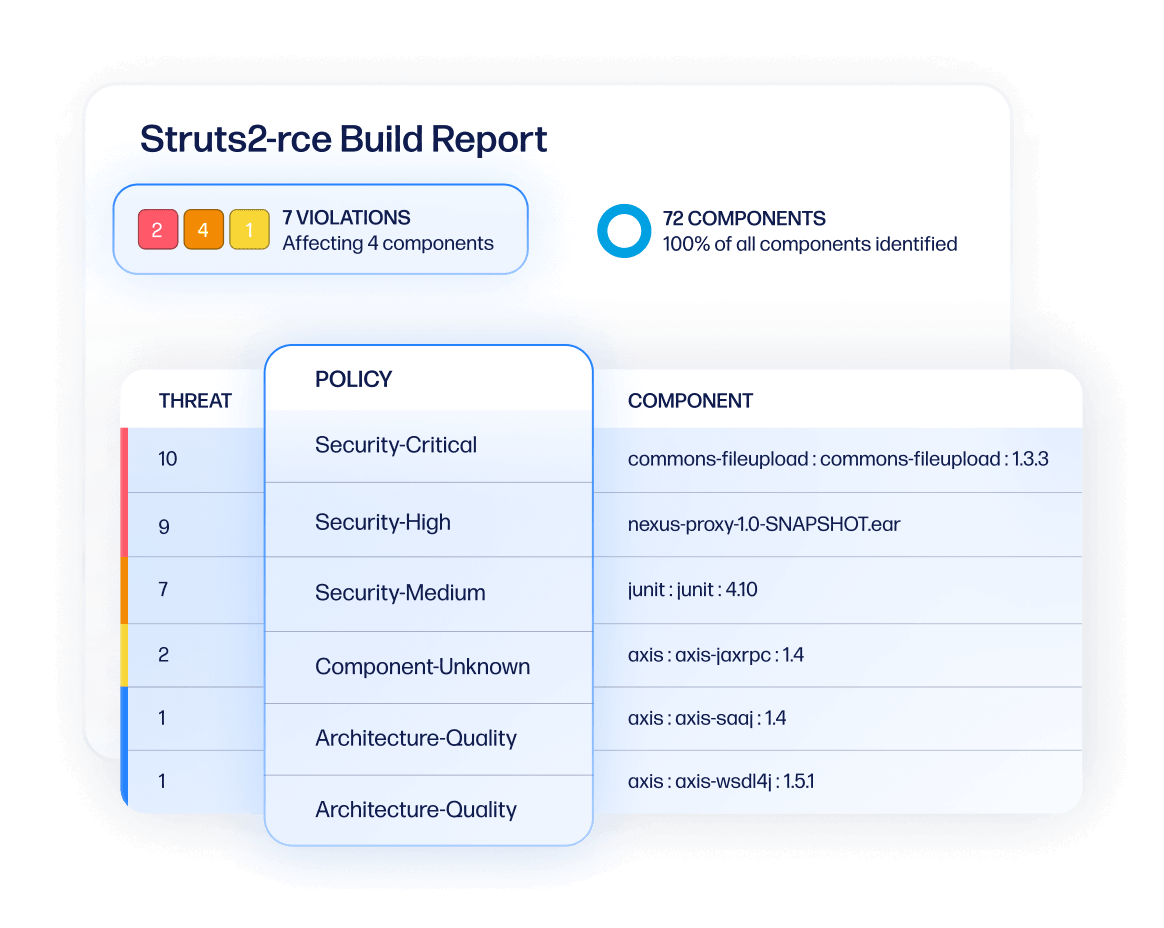
This automation extends to generating and updating SBOMs for each software release, safeguarding and verifying the integrity of provenance data, and integrating these practices into the software development and acquisition process.
Furthermore, the Platform's continuous monitoring capabilities facilitate the collection, maintenance, and sharing of provenance data in standard formats, enhancing the organization's ability to respond to and mitigate software vulnerabilities efficiently. By integrating with the software development toolchain, the Sonatype Platform supports continuous code analysis and testing, ensuring that all releases are regularly screened for new vulnerabilities. This comprehensive approach to managing software component provenance and integrity verification positions the Sonatype Platform as a crucial tool for organizations seeking to uphold stringent security standards in their software development and acquisition processes.
Requirement #4 - The software producer's approach towards managing security vulnerabilities is thorough and aligned with best practices, leveraging automated tools and processes for consistent monitoring and mitigation efforts.
The producer commits to running these processes regularly, especially before releasing any product, version, or update, to ensure the detection and handling of security vulnerabilities. The Sonatype Platform plays a pivotal role in this requirement by providing automation in scanning and detection of vulnerabilities within third-party components. Its comprehensive suite of integrations ensures seamless information gathering throughout the SDLC, eliminating the need for additional tools. The Platform's policy sets automate decision-making processes, relying on automated policy enforcement to manage security vulnerabilities effectively. This includes automated generation and management of SBOMs and continuous monitoring of third-party plugins for integrity issues.
-png.png?width=3841&height=2161&name=Sonatype-Platform-Lifecycle-Firewall-Repository@2x%20(1)-png.png)
Further emphasizing the importance of secure coding practices and toolchain integrity, the Sonatype Platform assists in selecting up-to-date and secure third-party build tool plugins. It coexists with other security tools, contributing to a robust defense against potential malware attacks targeting the software supply chain.
The Platform's capabilities extend to supporting secure coding standards, contributing to the identification and mitigation of vulnerabilities in third-party components, and ensuring compliance with secure coding practices. While the Platform primarily focuses on third-party component security, its functionalities complement other tools aimed at secure coding and build tool integrity, underscoring the importance of a holistic approach to software security.
Reach out to talk to a compliance expert, who can help you understand how to complete attestation.