Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Part 3: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 21, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
In part two of my blog 'A Closer Look at Today's Software Supply Chain', I discussed why human-speed supply chain management can’t keep pace with today’s.
Read More...
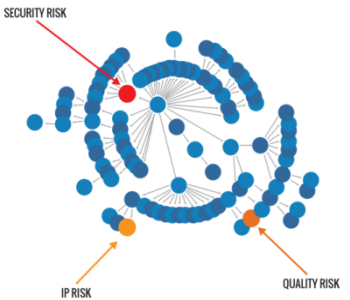
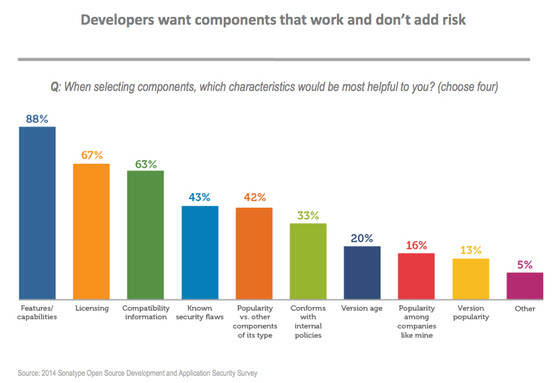
Are You Choosing the "Right" Component?
By
Manfred Moser on July 17, 2014
Cyber Supply Chain Management and Transparency Act
4 minute read time
In our recent open source developer survey we asked, what are the TOP FOUR characteristics considered when selecting a component? And since components are.
Read More...
Part 1: The Internet of Everything: Code, Cars, and More
By
Wayne Jackson on July 17, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Just like automobile manufacturers, software “manufacturers” need to apply supply chain management principles for both efficiency and quality.
Read More...
Stewing Over Software Ingredients
By
Ryan Berg on July 15, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Just the other day I was planning dinner for my family and thought it would be a great idea to bust out the Dutch oven I had to have, but rarely use, and.
Read More...
Open source components, a fine vintage or sour milk?
By
Derek Weeks on July 08, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
The U.S. recently overtook France as the world’s largest wine market. And here at Sonatype, we can proudly say we’ve contributed to this achievement.
Read More...
Securosis Dives Deep into our 2014 Survey
By
Derek Weeks on July 02, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
There are two ways to motivate others to action: emotional appeal and fact based analysis.
Read More...
We're bringing sexy back, Sonatype hits the catwalk
By
Derek Weeks on June 24, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
Enthusiasm for securing the software supply chain is growing in both conversation and practice.
Read More...
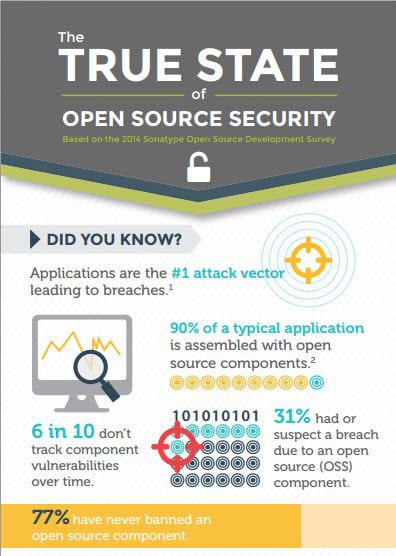
The 2014 Survey: Marked by an Industry Shock Wave
By
Wayne Jackson on June 20, 2014
Cyber Supply Chain Management and Transparency Act
2 minute read time
Wow! What an amazing turnout we had for our 4th annual survey: 3,353 participants this year brings us to over 11,000 participants in the four years we’ve.
Read More...
Walking in the Open Source Component Garden
By
Derek Weeks on June 17, 2014
Cyber Supply Chain Management and Transparency Act
3 minute read time
Its not everyday I can stop to enjoy my afternoon tea outside on my deck, overlooking my garden.
Read More...