Featured Article
Devs flood npm with 15,000 packages to reward themselves with Tea 'tokens'
By Ax Sharma on
April 16, 2024
vulnerabilities
The Sonatype Security Research team has identified over 15,000 npm packages that flood npm registry in a new trend where devs involved in the blockchain and cryptocurrency communities are leveraging
- Filter by:
- News & Views
- Product
- DevSecOps
- Open Source
- AppSec
- Vulnerabilities
Better software development: Insights from the SBOM Scorecard
By
Omar Torres on June 08, 2023
AppSec
2 minute read time
Data Insights– a look at Sonatype's SBOM scorecard.
Read More...
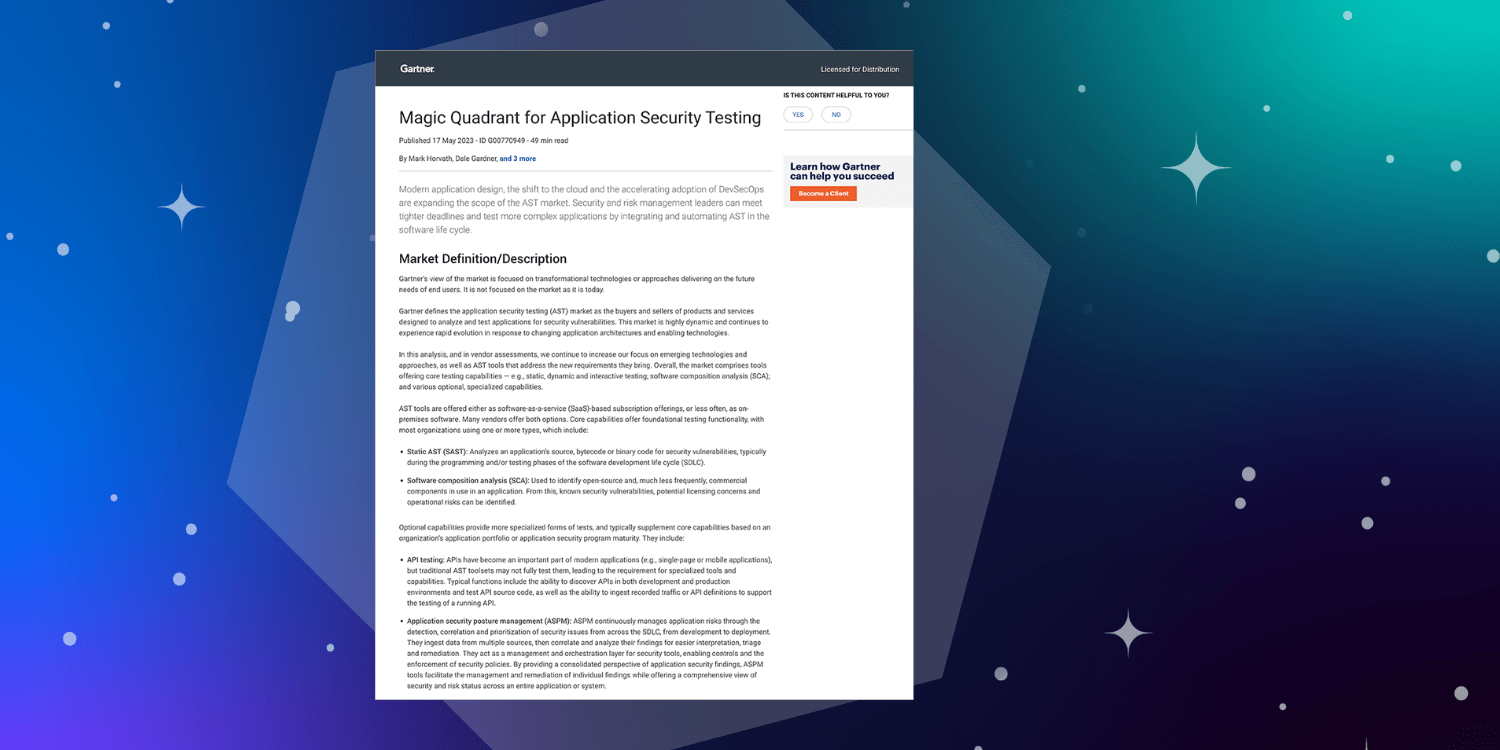
Sonatype named in the 2023 Gartner® Magic Quadrant™ for Application Security Testing
By
Tara Flynn Condon on May 23, 2023
AppSec
4 minute read time
Sonatype is named to the 2023 Gartner Magic Quadrant for Application Security Testing (AST).
Read More...
Another SolarWinds? The latest software supply chain attack on 3CX
By
Luke Mcbride on April 06, 2023
Software Supply Chain
6 minute read time
Get insights on the recent 3CX software supply chain attack and the growing importance of effective dependency management to protect against cyberattacks.
Read More...
Best practices in dependency management: Cooking a meal of gourmet code
By
Aaron Linskens on January 12, 2023
secure software supply chain
5 minute read time
Close to 85% of every application is open source software. Better understanding your software supply chain starts with understanding dependency management.
Read More...
SCA and SAST: What do they do and how can they help developers like you?
By
Theresa Mammarella on January 03, 2023
AppSec
5 minute read time
SCA and SAST tools help DevSecOps teams and application developers work together to identify vulnerabilities and improve security.
Read More...
What do Log4Shell and a global pandemic have in common?
By
Theresa Mammarella on November 15, 2022
AppSec
4 minute read time
A look at development through the lens of weddings, including long-term planning, contingencies, and disasters. A video talk from this years DEVOXX.
Read More...
Breaking organizational silos for better application security
By
Phil Vuollet on July 08, 2021
AppSec
4 minute read time
Security depends on collaboration and communication. Our recent Elevate talk breaks down pillars, structure, and suggestions for organizational silos.
Read More...
Caroline Wong is a Chief Strategy Officer who teaches the OWASP Top 10. She uses memorable analogies to explain all ten.
Read More...
With zero trust, you assume everything on the network is unsafe. You have to check trust explicitly. This stance improves security throughout the SDLC.
Read More...