Sonatype has identified two npm packages distube-config and discordyt that typosquat open source packages like Discord modules, in an attempt to infect Windows users with a Trojan. Our security researcher, Juan Aguirre, who analyzed the malware shares some insights.
This week, among the hundreds of suspicious and malicious packages identified by Sonatype's automated malware detection systems, distube-config and discordyt make interesting candidates.
Tracked under sonatype-2024-0173 and sonatype-2024-0176, these packages claim to be a "configuration module" for Distube, which is a legitimate Discord module that allows developers to "simplify your music commands and play songs with audio filters on Discord."
It didn't take Sonatype security researcher Juan Aguirre long, however, to unmask what these packages are really up to.
Obfuscated code downloads Windows Trojan
Upon installation, the distube-config package runs a highly obfuscated file index.js but its purpose does not become clear upfront.

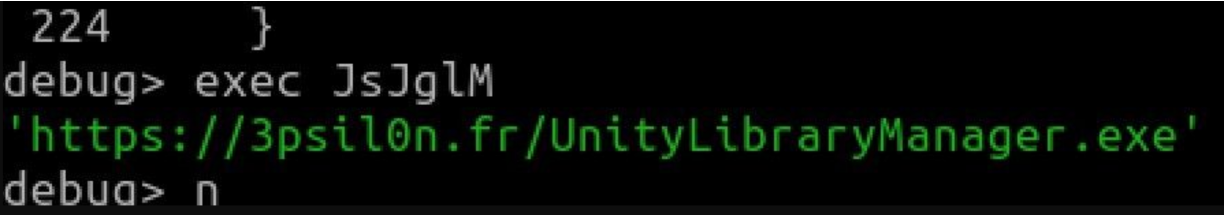
After a deep dive analysis and some debugging, Aguirre identified an illicit URL (shown below), that the file connects to, and downloads a Windows executable:
hxxps://3psil0n[.]fr/UnityLibraryManager.exe
The domain 3psil0n[.]fr has previously been associated with multiple malware artifacts and analysis reports seen on threat intel platforms, such as VirusTotal.
"I tried my go-to online deobfuscators for this payload but without any success, so I had to dive in a bit with dynamic analysis to pull out the malicious URL that the malware was trying to reach out to," says Aguirre.
The name, "UnityLibraryManager.exe" is once again misleading — giving off the impression that the binary file is associated with the Unity video game engine.
The executable, however, is a Windows info-stealer and identified as such by at least 6% of the leading antivirus engines.
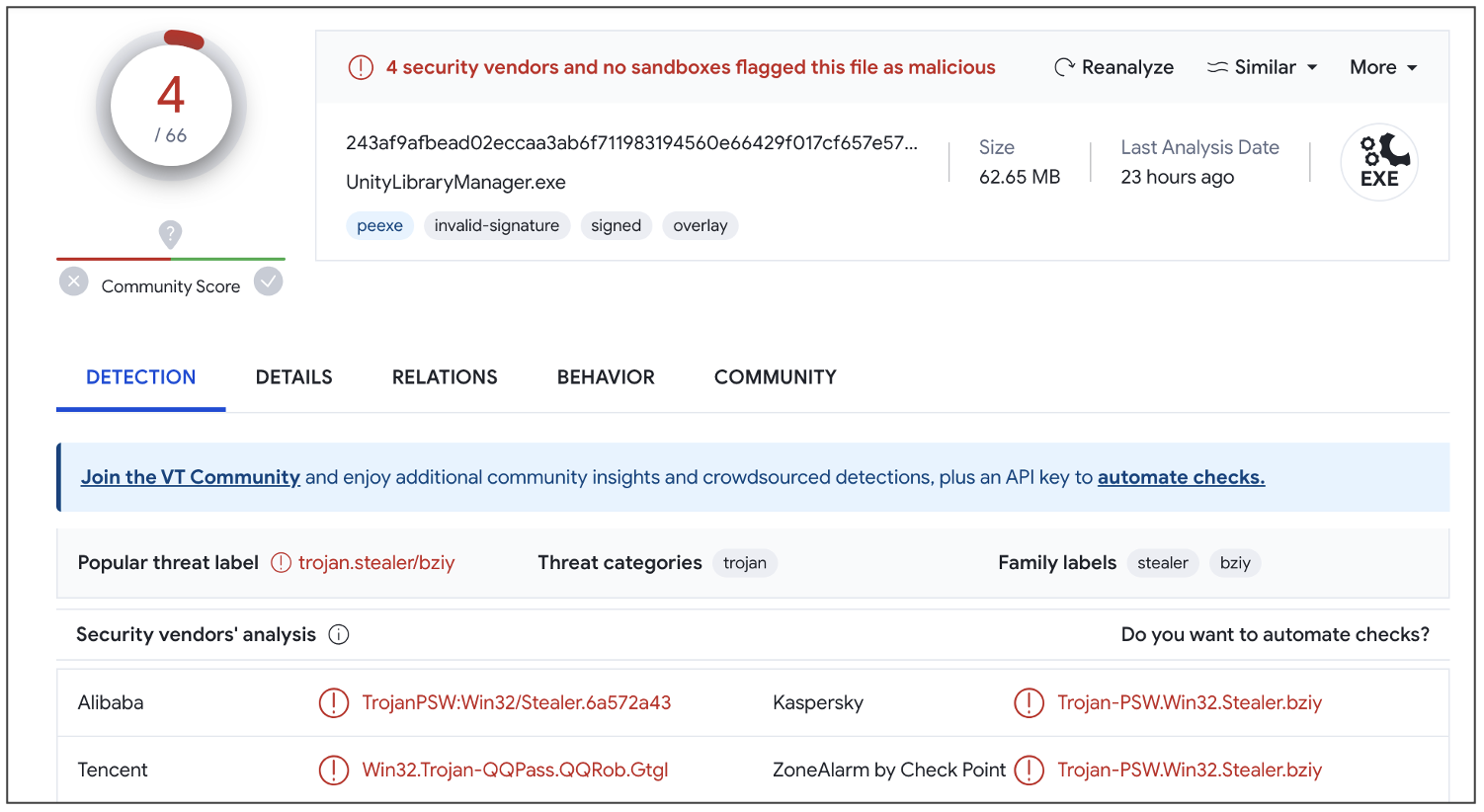
The low detection rate isn't surprising, however, given the presence of anti-detection and anti-reverse engineering techniques (such as checking the presence of a debugger) attributing to the stealthy nature of the executable.
Among other things, the executable is seen accessing and altering Windows registry keys, including those concerned with the system's security policy.
"This keeps up a trend we've seen of bad actors trying to leverage Discord-like packages to inject their malicious payloads in," continues Aguirre, referring to the ongoing efforts by threat actors to push similar info-stealers on open source registries.
"It's so easy to run a piece of code you downloaded from a seemingly trusted source, like npm, especially when its so obfuscated you cant really tell what's happening. But it is crucial to understand what we are bringing into our pipeline and putting into our code."
Repository Firewall customers remain safe
Sonatype's products such as Repository Firewall and Lifecycle stay on top of nascent attacks and vulnerabilities and provide you with detailed insights to thwart malware, Potentially Unwanted Applications (PUAs), and vulnerable components from reaching your builds:
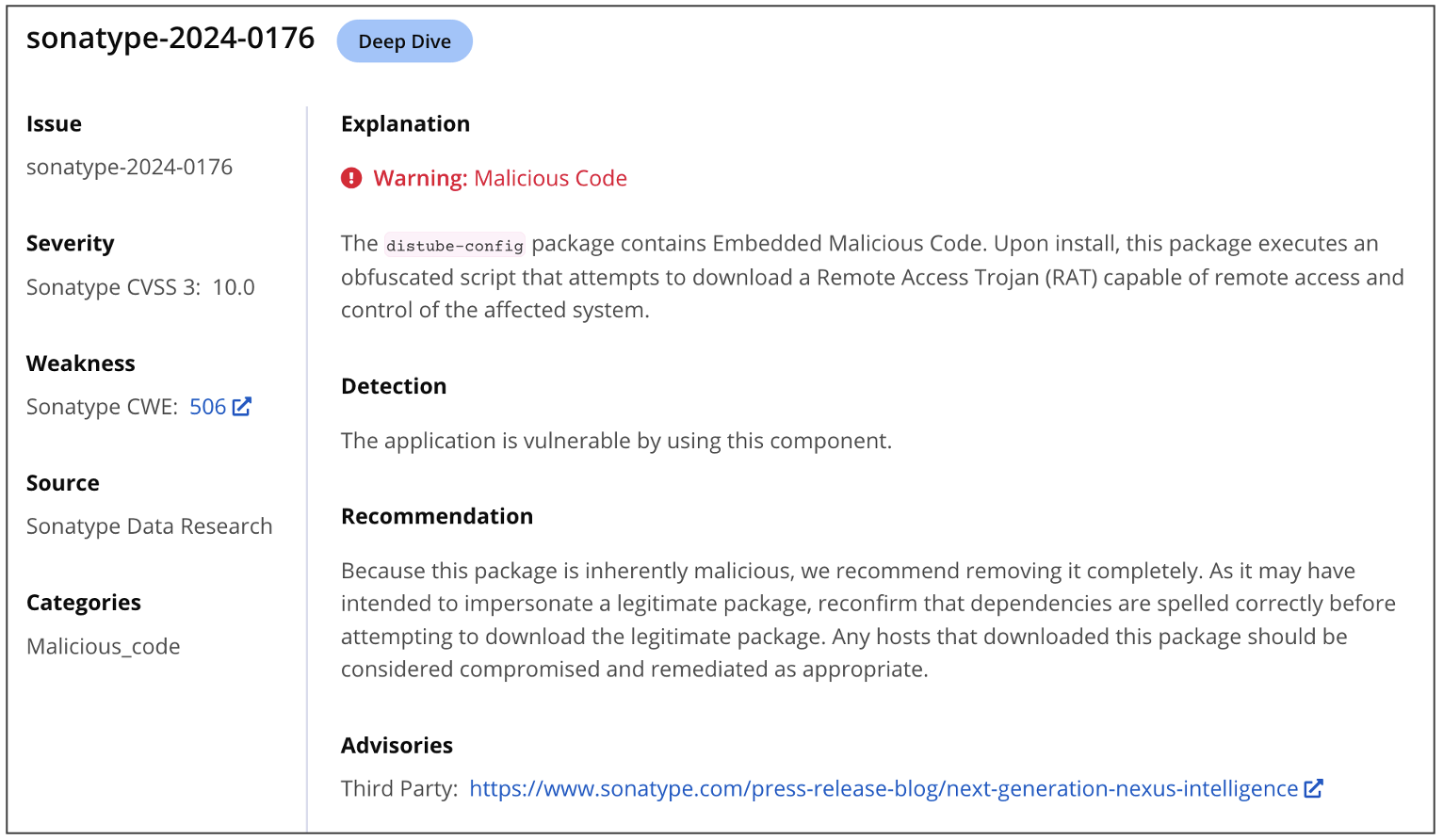
Users of Sonatype Repository Firewall can rest easy knowing that these packages would automatically be blocked from reaching their development builds and keep their software development life cycle (SDLC) hygienic.





