An npm package called 'stringjs_lib' was identified by Sonatype this week. The package typosquats the popular npm library 'string' (or StringJS) and ships a Discord info-stealer obfuscated not one, five times.
The legitimate 'string' library is downloaded anywhere between 70,000 and 100,000 times in any given week. Which explains why a threat actor would be lured to ship counterfeit versions of this library — a theme we've repeatedly observed when it comes to malware distributed via open source typosquats.
The malicious 'stringjs_lib' package was caught by Sonatype's automated malware detection systems, which are an integral part of Sonatype Repository Firewall.
Analysis by our security researcher Carlos Fernandez revealed that the package goes to great lengths to hide its true purpose.
Packed and Obfuscated 5x to Hinder Analysis
This week, the 'stringjs_lib' package appeared on the npm registry, and was caught by our automated malware detection bots. While both the empty README and the name closely resembling StringJS raised red flags, it took some time before the package's purpose became completely clear.
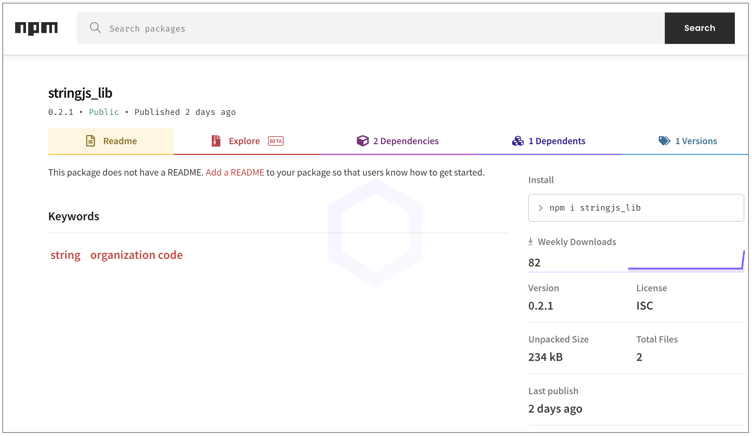
The package was published from a standalone, pseudonymous npm account, 'stringjs_npm.'
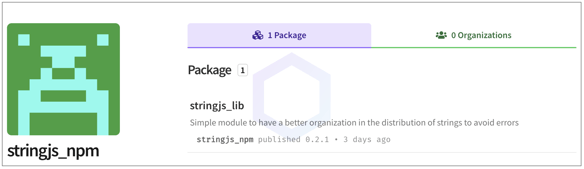
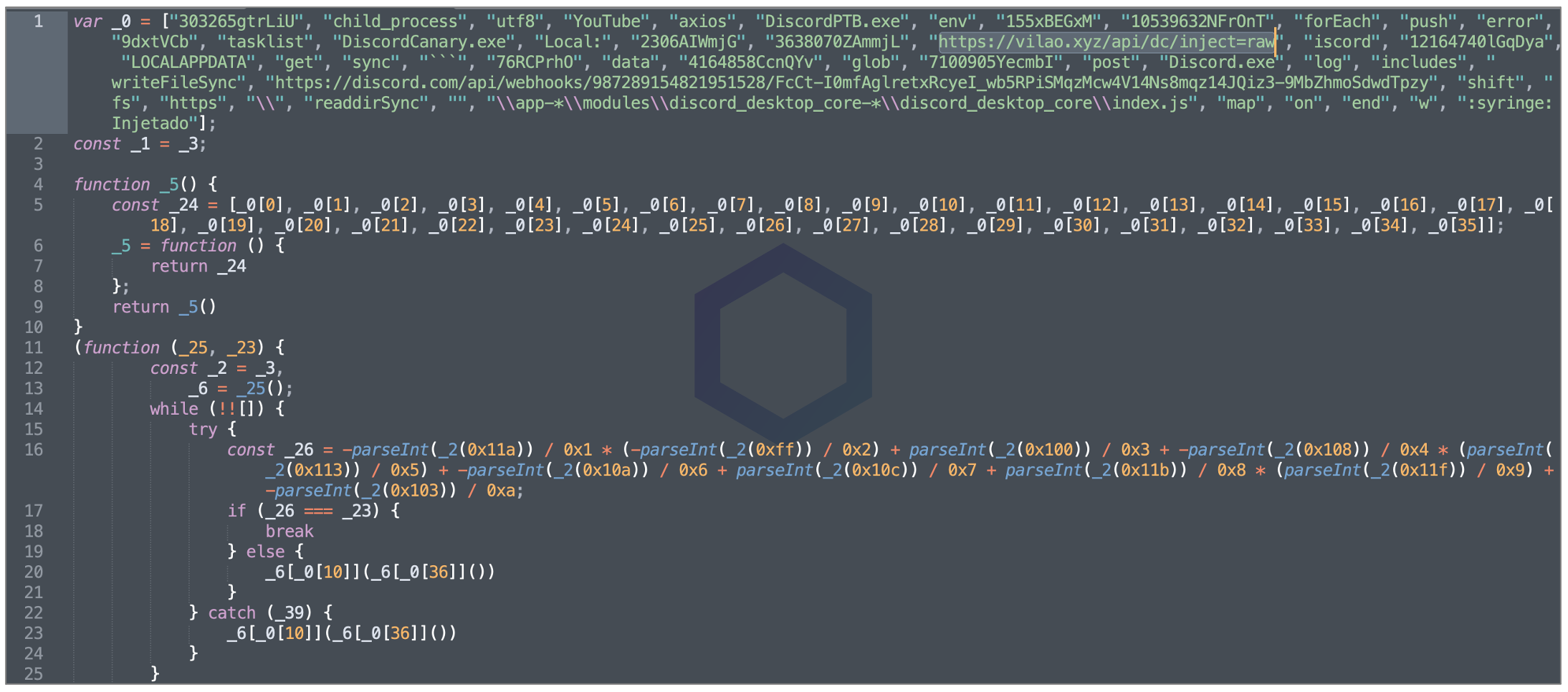
Within the package, there's a simple manifest file (package.json) and an index.js file. And it is this 'index.js' file that'd leave an analyst scratching their heads:
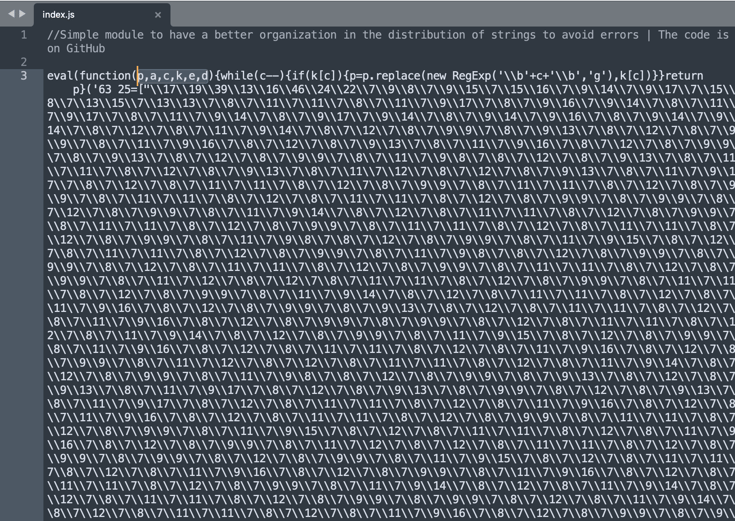
The above string sequence spans several lines — rather the 233,700+ character sequence is tightly packed in a single line by the author, but would otherwise exceed roughly 4,250 lines of code if it had newline characters.
The sequence ends cryptically too:
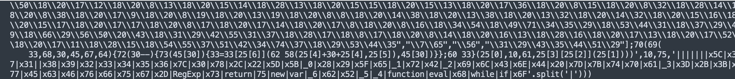
Simple deobfuscation techniques and paths we usually use to unpack malware didn't help much. But, Fernandez noticed a few things that helped it all come to light:
- First, Line 3 of the code starts with eval(function(p,a,c,k,e,d)... which is a big hint the code had been processed through one or more JavaScript packers that are known to generate these code patterns.
- Secondly, every time Fernandez ran the code through an "unpacker," the resulting output would be a mutated version of the packed code but not reveal the unpacked code. This indicated the payload had been packed several times. After running the 5th "unpack" iteration, we obtained an output that further had to be run through a JS de-obfuscator to reach a meaningful result.
Discord infostealer drops more malicious code
That is when the true nature of 'stringjs_lib' is revealed. Dynamic analysis of the code had indicated it was attempting to make dubious web requests, but seeing the deciphered version of the static code confirmed our suspicions.
The package contains malicious code akin to the ones we've analyzed in Discord infostealers before. These stealers look for a user's Discord files and tokens, and upload this information to the threat actor via Discord webhooks hardcoded in the application.
In addition to 'stringjs_lib' doing all that, the package downloads even more payload which is, yet again obfuscated, from the URL shown below:
hxxps://vilao[.]xyz/api/dc/inject=raw
 We reported our findings to npm who took the package down within a day.
We reported our findings to npm who took the package down within a day.
Sonatype Repository Firewall keeps you protected
This discovery follows our earlier report of malicious Python packages that stole Telegram cache files and set up illicit Remote Desktop (RDP) accounts on Windows systems.
As a DevSecOps organization, we remain committed to identifying and stopping attacks against open source developers and the wider software supply chain, like the ones discussed above.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection systems while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.






